mirror of
https://github.com/goharbor/harbor.git
synced 2024-12-26 18:48:02 +01:00
commit
b5788f0695
32
src/Gopkg.lock
generated
32
src/Gopkg.lock
generated
@ -7,6 +7,12 @@
|
||||
revision = "b26d9c308763d68093482582cea63d69be07a0f0"
|
||||
version = "v0.3.0"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/Knetic/govaluate"
|
||||
packages = ["."]
|
||||
revision = "d216395917cc49052c7c7094cf57f09657ca08a8"
|
||||
version = "v3.0.0"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/Masterminds/semver"
|
||||
packages = ["."]
|
||||
@ -59,6 +65,23 @@
|
||||
packages = ["."]
|
||||
revision = "e87155e8f0c05bf323d0b13470e1b97af0cb5652"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/casbin/casbin"
|
||||
packages = [
|
||||
".",
|
||||
"config",
|
||||
"effect",
|
||||
"log",
|
||||
"model",
|
||||
"persist",
|
||||
"persist/file-adapter",
|
||||
"rbac",
|
||||
"rbac/default-role-manager",
|
||||
"util"
|
||||
]
|
||||
revision = "542e16cac74562eefac970a7d0d1467640d1f1cb"
|
||||
version = "v1.7.0"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/davecgh/go-spew"
|
||||
packages = ["spew"]
|
||||
@ -248,6 +271,12 @@
|
||||
revision = "aa2ec055abd10d26d539eb630a92241b781ce4bc"
|
||||
version = "v1.0.0-rc0"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/pkg/errors"
|
||||
packages = ["."]
|
||||
revision = "645ef00459ed84a119197bfb8d8205042c6df63d"
|
||||
version = "v0.8.0"
|
||||
|
||||
[[projects]]
|
||||
name = "github.com/pmezard/go-difflib"
|
||||
packages = ["difflib"]
|
||||
@ -360,6 +389,7 @@
|
||||
[[projects]]
|
||||
name = "k8s.io/helm"
|
||||
packages = [
|
||||
"cmd/helm/search",
|
||||
"pkg/chartutil",
|
||||
"pkg/getter",
|
||||
"pkg/helm/environment",
|
||||
@ -381,6 +411,6 @@
|
||||
[solve-meta]
|
||||
analyzer-name = "dep"
|
||||
analyzer-version = 1
|
||||
inputs-digest = "f2bc787303dc9f72125800ed44f5fefed9e832183419e563183e87be26534a1c"
|
||||
inputs-digest = "862941e7de65d953c0133ea4b290a079990f38c7cd6e2f1139ac78706d0912b3"
|
||||
solver-name = "gps-cdcl"
|
||||
solver-version = 1
|
||||
|
||||
@ -18,7 +18,7 @@
|
||||
# [[override]]
|
||||
# name = "github.com/x/y"
|
||||
# version = "2.4.0"
|
||||
ignored = ["github.com/vmware/harbor/tests*"]
|
||||
ignored = ["github.com/goharbor/harbor/tests*"]
|
||||
|
||||
[prune]
|
||||
go-tests = true
|
||||
@ -28,6 +28,10 @@ ignored = ["github.com/vmware/harbor/tests*"]
|
||||
name = "github.com/astaxie/beego"
|
||||
version = "=1.9.0"
|
||||
|
||||
[[constraint]]
|
||||
name = "github.com/casbin/casbin"
|
||||
version = "=1.7.0"
|
||||
|
||||
[[constraint]]
|
||||
name = "github.com/dghubble/sling"
|
||||
version = "=1.1.0"
|
||||
|
||||
138
src/common/ram/casbin.go
Normal file
138
src/common/ram/casbin.go
Normal file
@ -0,0 +1,138 @@
|
||||
// Copyright Project Harbor Authors
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package ram
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
|
||||
"github.com/casbin/casbin"
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
var (
|
||||
errNotImplemented = errors.New("Not implemented")
|
||||
)
|
||||
|
||||
// Syntax for models see https://casbin.org/docs/en/syntax-for-models
|
||||
const modelText = `
|
||||
# Request definition
|
||||
[request_definition]
|
||||
r = sub, obj, act
|
||||
|
||||
# Policy definition
|
||||
[policy_definition]
|
||||
p = sub, obj, act, eft
|
||||
|
||||
# Role definition
|
||||
[role_definition]
|
||||
g = _, _
|
||||
|
||||
# Policy effect
|
||||
[policy_effect]
|
||||
e = some(where (p.eft == allow)) && !some(where (p.eft == deny))
|
||||
|
||||
# Matchers
|
||||
[matchers]
|
||||
m = g(r.sub, p.sub) && keyMatch2(r.obj, p.obj) && (r.act == p.act || p.act == '*')
|
||||
`
|
||||
|
||||
type userAdapter struct {
|
||||
User
|
||||
}
|
||||
|
||||
func (a *userAdapter) getRolePolicyLines(role Role) []string {
|
||||
lines := []string{}
|
||||
|
||||
roleName := role.GetRoleName()
|
||||
// returns empty policy lines if role name is empty
|
||||
if roleName == "" {
|
||||
return lines
|
||||
}
|
||||
|
||||
for _, policy := range role.GetPolicies() {
|
||||
line := fmt.Sprintf("p, %s, %s, %s, %s", roleName, policy.Resource, policy.Action, policy.GetEffect())
|
||||
lines = append(lines, line)
|
||||
}
|
||||
|
||||
return lines
|
||||
}
|
||||
|
||||
func (a *userAdapter) getUserPolicyLines() []string {
|
||||
lines := []string{}
|
||||
|
||||
username := a.GetUserName()
|
||||
// returns empty policy lines if username is empty
|
||||
if username == "" {
|
||||
return lines
|
||||
}
|
||||
|
||||
for _, policy := range a.GetPolicies() {
|
||||
line := fmt.Sprintf("p, %s, %s, %s, %s", username, policy.Resource, policy.Action, policy.GetEffect())
|
||||
lines = append(lines, line)
|
||||
}
|
||||
|
||||
return lines
|
||||
}
|
||||
|
||||
func (a *userAdapter) getUserAllPolicyLines() []string {
|
||||
lines := []string{}
|
||||
|
||||
username := a.GetUserName()
|
||||
// returns empty policy lines if username is empty
|
||||
if username == "" {
|
||||
return lines
|
||||
}
|
||||
|
||||
lines = append(lines, a.getUserPolicyLines()...)
|
||||
|
||||
for _, role := range a.GetRoles() {
|
||||
lines = append(lines, a.getRolePolicyLines(role)...)
|
||||
lines = append(lines, fmt.Sprintf("g, %s, %s", username, role.GetRoleName()))
|
||||
}
|
||||
|
||||
return lines
|
||||
}
|
||||
|
||||
func (a *userAdapter) LoadPolicy(model model.Model) error {
|
||||
for _, line := range a.getUserAllPolicyLines() {
|
||||
persist.LoadPolicyLine(line, model)
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
func (a *userAdapter) SavePolicy(model model.Model) error {
|
||||
return errNotImplemented
|
||||
}
|
||||
|
||||
func (a *userAdapter) AddPolicy(sec string, ptype string, rule []string) error {
|
||||
return errNotImplemented
|
||||
}
|
||||
|
||||
func (a *userAdapter) RemovePolicy(sec string, ptype string, rule []string) error {
|
||||
return errNotImplemented
|
||||
}
|
||||
|
||||
func (a *userAdapter) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error {
|
||||
return errNotImplemented
|
||||
}
|
||||
|
||||
func enforcerForUser(user User) *casbin.Enforcer {
|
||||
m := model.Model{}
|
||||
m.LoadModelFromText(modelText)
|
||||
return casbin.NewEnforcer(m, &userAdapter{User: user})
|
||||
}
|
||||
113
src/common/ram/ram.go
Normal file
113
src/common/ram/ram.go
Normal file
@ -0,0 +1,113 @@
|
||||
// Copyright Project Harbor Authors
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package ram
|
||||
|
||||
import (
|
||||
"path"
|
||||
)
|
||||
|
||||
const (
|
||||
// EffectAllow allow effect
|
||||
EffectAllow = Effect("allow")
|
||||
// EffectDeny deny effect
|
||||
EffectDeny = Effect("deny")
|
||||
)
|
||||
|
||||
// Resource the type of resource
|
||||
type Resource string
|
||||
|
||||
func (res Resource) String() string {
|
||||
return string(res)
|
||||
}
|
||||
|
||||
// Subresource returns subresource
|
||||
func (res Resource) Subresource(resources ...Resource) Resource {
|
||||
elements := []string{res.String()}
|
||||
|
||||
for _, resource := range resources {
|
||||
elements = append(elements, resource.String())
|
||||
}
|
||||
|
||||
return Resource(path.Join(elements...))
|
||||
}
|
||||
|
||||
// Action the type of action
|
||||
type Action string
|
||||
|
||||
func (act Action) String() string {
|
||||
return string(act)
|
||||
}
|
||||
|
||||
// Effect the type of effect
|
||||
type Effect string
|
||||
|
||||
func (eff Effect) String() string {
|
||||
return string(eff)
|
||||
}
|
||||
|
||||
// Policy the type of policy
|
||||
type Policy struct {
|
||||
Resource
|
||||
Action
|
||||
Effect
|
||||
}
|
||||
|
||||
// GetEffect returns effect of resource, default is allow
|
||||
func (p *Policy) GetEffect() string {
|
||||
eft := p.Effect
|
||||
if eft == "" {
|
||||
eft = EffectAllow
|
||||
}
|
||||
|
||||
return eft.String()
|
||||
}
|
||||
|
||||
// Role the interface of ram role
|
||||
type Role interface {
|
||||
// GetRoleName returns the role identity, if empty string role's policies will be ignore
|
||||
GetRoleName() string
|
||||
GetPolicies() []*Policy
|
||||
}
|
||||
|
||||
// User the interface of ram user
|
||||
type User interface {
|
||||
// GetUserName returns the user identity, if empty string user's all policies will be ignore
|
||||
GetUserName() string
|
||||
GetPolicies() []*Policy
|
||||
GetRoles() []Role
|
||||
}
|
||||
|
||||
// BaseUser the type implement User interface whose policies are empty
|
||||
type BaseUser struct{}
|
||||
|
||||
// GetRoles returns roles of the user
|
||||
func (u *BaseUser) GetRoles() []Role {
|
||||
return nil
|
||||
}
|
||||
|
||||
// GetUserName returns user identity
|
||||
func (u *BaseUser) GetUserName() string {
|
||||
return ""
|
||||
}
|
||||
|
||||
// GetPolicies returns policies of the user
|
||||
func (u *BaseUser) GetPolicies() []*Policy {
|
||||
return nil
|
||||
}
|
||||
|
||||
// HasPermission returns whether the user has action permission on resource
|
||||
func HasPermission(user User, resource Resource, action Action) bool {
|
||||
return enforcerForUser(user).Enforce(user.GetUserName(), resource.String(), action.String())
|
||||
}
|
||||
357
src/common/ram/ram_test.go
Normal file
357
src/common/ram/ram_test.go
Normal file
@ -0,0 +1,357 @@
|
||||
// Copyright Project Harbor Authors
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package ram
|
||||
|
||||
import (
|
||||
"testing"
|
||||
)
|
||||
|
||||
type role struct {
|
||||
RoleName string
|
||||
}
|
||||
|
||||
func (r *role) GetRoleName() string {
|
||||
return r.RoleName
|
||||
}
|
||||
|
||||
func (r *role) GetPolicies() []*Policy {
|
||||
return []*Policy{
|
||||
{Resource: "/project", Action: "create"},
|
||||
{Resource: "/project", Action: "update"},
|
||||
}
|
||||
}
|
||||
|
||||
type userWithRoles struct {
|
||||
Username string
|
||||
RoleName string
|
||||
BaseUser
|
||||
}
|
||||
|
||||
func (u *userWithRoles) GetUserName() string {
|
||||
return u.Username
|
||||
}
|
||||
|
||||
func (u *userWithRoles) GetRoles() []Role {
|
||||
return []Role{
|
||||
&role{RoleName: u.RoleName},
|
||||
}
|
||||
}
|
||||
|
||||
type userWithoutRoles struct {
|
||||
Username string
|
||||
UserPolicies []*Policy
|
||||
BaseUser
|
||||
}
|
||||
|
||||
func (u *userWithoutRoles) GetUserName() string {
|
||||
return u.Username
|
||||
}
|
||||
|
||||
func (u *userWithoutRoles) GetPolicies() []*Policy {
|
||||
return u.UserPolicies
|
||||
}
|
||||
|
||||
func TestHasPermissionUserWithRoles(t *testing.T) {
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project create for project admin",
|
||||
args: args{
|
||||
&userWithRoles{Username: "project admin", RoleName: "projectAdmin"},
|
||||
"/project",
|
||||
"create",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project update for project admin",
|
||||
args: args{
|
||||
&userWithRoles{Username: "project admin", RoleName: "projectAdmin"},
|
||||
"/project",
|
||||
"update",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project delete for project admin",
|
||||
args: args{
|
||||
&userWithRoles{Username: "project admin", RoleName: "projectAdmin"},
|
||||
"/project",
|
||||
"delete",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestHasPermissionUserWithoutRoles(t *testing.T) {
|
||||
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project create for user without roles",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "project", Action: "create"}}},
|
||||
"/project",
|
||||
"create",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project delete test for user without roles",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "project", Action: "create"}}},
|
||||
"/project",
|
||||
"delete",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestHasPermissionUsernameEmpty(t *testing.T) {
|
||||
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project create for user without roles",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "", UserPolicies: []*Policy{{Resource: "project", Action: "create"}}},
|
||||
"/project",
|
||||
"create",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestHasPermissionRoleNameEmpty(t *testing.T) {
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project create for project admin",
|
||||
args: args{
|
||||
&userWithRoles{Username: "project admin", RoleName: ""},
|
||||
"/project",
|
||||
"create",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
{
|
||||
name: "project update for project admin",
|
||||
args: args{
|
||||
&userWithRoles{Username: "project admin", RoleName: ""},
|
||||
"/project",
|
||||
"update",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestHasPermissionResourceKeyMatch(t *testing.T) {
|
||||
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project member create for resource key match",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "/project/1/*", Action: "*"}}},
|
||||
"/project/1/member",
|
||||
"create",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project member create for resource key match",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "/project/:id/*", Action: "*"}}},
|
||||
"/project/1/member",
|
||||
"create",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project repository create test for resource key match",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "/project/1/*", Action: "create"}}},
|
||||
"/project/1/repository",
|
||||
"create",
|
||||
},
|
||||
want: true,
|
||||
},
|
||||
{
|
||||
name: "project repository delete test for resource key match",
|
||||
args: args{
|
||||
&userWithoutRoles{Username: "user1", UserPolicies: []*Policy{{Resource: "/project/1/*", Action: "create"}}},
|
||||
"/project/1/repository",
|
||||
"delete",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestHasPermissionPolicyDeny(t *testing.T) {
|
||||
|
||||
type args struct {
|
||||
user User
|
||||
resource Resource
|
||||
action Action
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
args args
|
||||
want bool
|
||||
}{
|
||||
{
|
||||
name: "project member create for resource deny",
|
||||
args: args{
|
||||
&userWithoutRoles{
|
||||
Username: "user1",
|
||||
UserPolicies: []*Policy{
|
||||
{Resource: "/project/1/*", Action: "*"},
|
||||
{Resource: "/project/1/member", Action: "create", Effect: EffectDeny},
|
||||
},
|
||||
},
|
||||
"/project/1/member",
|
||||
"create",
|
||||
},
|
||||
want: false,
|
||||
},
|
||||
}
|
||||
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := HasPermission(tt.args.user, tt.args.resource, tt.args.action); got != tt.want {
|
||||
t.Errorf("HasPermission() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
|
||||
func TestResource_Subresource(t *testing.T) {
|
||||
type args struct {
|
||||
resources []Resource
|
||||
}
|
||||
tests := []struct {
|
||||
name string
|
||||
res Resource
|
||||
args args
|
||||
want Resource
|
||||
}{
|
||||
{
|
||||
name: "subresource image",
|
||||
res: Resource("/project/1"),
|
||||
args: args{
|
||||
resources: []Resource{"image"},
|
||||
},
|
||||
want: Resource("/project/1/image"),
|
||||
},
|
||||
{
|
||||
name: "subresource image build-history",
|
||||
res: Resource("/project/1"),
|
||||
args: args{
|
||||
resources: []Resource{"image", "12", "build-history"},
|
||||
},
|
||||
want: Resource("/project/1/image/12/build-history"),
|
||||
},
|
||||
}
|
||||
for _, tt := range tests {
|
||||
t.Run(tt.name, func(t *testing.T) {
|
||||
if got := tt.res.Subresource(tt.args.resources...); got != tt.want {
|
||||
t.Errorf("Resource.Subresource() = %v, want %v", got, tt.want)
|
||||
}
|
||||
})
|
||||
}
|
||||
}
|
||||
28
src/vendor/github.com/Knetic/govaluate/.gitignore
generated
vendored
Normal file
28
src/vendor/github.com/Knetic/govaluate/.gitignore
generated
vendored
Normal file
@ -0,0 +1,28 @@
|
||||
# Compiled Object files, Static and Dynamic libs (Shared Objects)
|
||||
*.o
|
||||
*.a
|
||||
*.so
|
||||
|
||||
# Folders
|
||||
_obj
|
||||
_test
|
||||
|
||||
# Architecture specific extensions/prefixes
|
||||
*.[568vq]
|
||||
[568vq].out
|
||||
|
||||
*.cgo1.go
|
||||
*.cgo2.c
|
||||
_cgo_defun.c
|
||||
_cgo_gotypes.go
|
||||
_cgo_export.*
|
||||
|
||||
_testmain.go
|
||||
|
||||
*.exe
|
||||
*.test
|
||||
coverage.out
|
||||
|
||||
manual_test.go
|
||||
*.out
|
||||
*.err
|
||||
10
src/vendor/github.com/Knetic/govaluate/.travis.yml
generated
vendored
Normal file
10
src/vendor/github.com/Knetic/govaluate/.travis.yml
generated
vendored
Normal file
@ -0,0 +1,10 @@
|
||||
language: go
|
||||
|
||||
script: ./test.sh
|
||||
|
||||
go:
|
||||
- 1.2
|
||||
- 1.3
|
||||
- 1.4
|
||||
- 1.5
|
||||
- 1.6
|
||||
12
src/vendor/github.com/Knetic/govaluate/CONTRIBUTORS
generated
vendored
Normal file
12
src/vendor/github.com/Knetic/govaluate/CONTRIBUTORS
generated
vendored
Normal file
@ -0,0 +1,12 @@
|
||||
This library was authored by George Lester, and contains contributions from:
|
||||
|
||||
vjeantet (regex support)
|
||||
iasci (ternary operator)
|
||||
oxtoacart (parameter structures, deferred parameter retrieval)
|
||||
wmiller848 (bitwise operators)
|
||||
prashantv (optimization of bools)
|
||||
dpaolella (exposure of variables used in an expression)
|
||||
benpaxton (fix for missing type checks during literal elide process)
|
||||
abrander (panic-finding testing tool)
|
||||
xfennec (fix for dates being parsed in the current Location)
|
||||
bgaifullin (lifting restriction on complex/struct types)
|
||||
272
src/vendor/github.com/Knetic/govaluate/EvaluableExpression.go
generated
vendored
Normal file
272
src/vendor/github.com/Knetic/govaluate/EvaluableExpression.go
generated
vendored
Normal file
@ -0,0 +1,272 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
)
|
||||
|
||||
const isoDateFormat string = "2006-01-02T15:04:05.999999999Z0700"
|
||||
const shortCircuitHolder int = -1
|
||||
|
||||
var DUMMY_PARAMETERS = MapParameters(map[string]interface{}{})
|
||||
|
||||
/*
|
||||
EvaluableExpression represents a set of ExpressionTokens which, taken together,
|
||||
are an expression that can be evaluated down into a single value.
|
||||
*/
|
||||
type EvaluableExpression struct {
|
||||
|
||||
/*
|
||||
Represents the query format used to output dates. Typically only used when creating SQL or Mongo queries from an expression.
|
||||
Defaults to the complete ISO8601 format, including nanoseconds.
|
||||
*/
|
||||
QueryDateFormat string
|
||||
|
||||
/*
|
||||
Whether or not to safely check types when evaluating.
|
||||
If true, this library will return error messages when invalid types are used.
|
||||
If false, the library will panic when operators encounter types they can't use.
|
||||
|
||||
This is exclusively for users who need to squeeze every ounce of speed out of the library as they can,
|
||||
and you should only set this to false if you know exactly what you're doing.
|
||||
*/
|
||||
ChecksTypes bool
|
||||
|
||||
tokens []ExpressionToken
|
||||
evaluationStages *evaluationStage
|
||||
inputExpression string
|
||||
}
|
||||
|
||||
/*
|
||||
Parses a new EvaluableExpression from the given [expression] string.
|
||||
Returns an error if the given expression has invalid syntax.
|
||||
*/
|
||||
func NewEvaluableExpression(expression string) (*EvaluableExpression, error) {
|
||||
|
||||
functions := make(map[string]ExpressionFunction)
|
||||
return NewEvaluableExpressionWithFunctions(expression, functions)
|
||||
}
|
||||
|
||||
/*
|
||||
Similar to [NewEvaluableExpression], except that instead of a string, an already-tokenized expression is given.
|
||||
This is useful in cases where you may be generating an expression automatically, or using some other parser (e.g., to parse from a query language)
|
||||
*/
|
||||
func NewEvaluableExpressionFromTokens(tokens []ExpressionToken) (*EvaluableExpression, error) {
|
||||
|
||||
var ret *EvaluableExpression
|
||||
var err error
|
||||
|
||||
ret = new(EvaluableExpression)
|
||||
ret.QueryDateFormat = isoDateFormat
|
||||
|
||||
err = checkBalance(tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
err = checkExpressionSyntax(tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.tokens, err = optimizeTokens(tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.evaluationStages, err = planStages(ret.tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.ChecksTypes = true
|
||||
return ret, nil
|
||||
}
|
||||
|
||||
/*
|
||||
Similar to [NewEvaluableExpression], except enables the use of user-defined functions.
|
||||
Functions passed into this will be available to the expression.
|
||||
*/
|
||||
func NewEvaluableExpressionWithFunctions(expression string, functions map[string]ExpressionFunction) (*EvaluableExpression, error) {
|
||||
|
||||
var ret *EvaluableExpression
|
||||
var err error
|
||||
|
||||
ret = new(EvaluableExpression)
|
||||
ret.QueryDateFormat = isoDateFormat
|
||||
ret.inputExpression = expression
|
||||
|
||||
ret.tokens, err = parseTokens(expression, functions)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
err = checkBalance(ret.tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
err = checkExpressionSyntax(ret.tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.tokens, err = optimizeTokens(ret.tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.evaluationStages, err = planStages(ret.tokens)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
ret.ChecksTypes = true
|
||||
return ret, nil
|
||||
}
|
||||
|
||||
/*
|
||||
Same as `Eval`, but automatically wraps a map of parameters into a `govalute.Parameters` structure.
|
||||
*/
|
||||
func (this EvaluableExpression) Evaluate(parameters map[string]interface{}) (interface{}, error) {
|
||||
|
||||
if parameters == nil {
|
||||
return this.Eval(nil)
|
||||
}
|
||||
return this.Eval(MapParameters(parameters))
|
||||
}
|
||||
|
||||
/*
|
||||
Runs the entire expression using the given [parameters].
|
||||
e.g., If the expression contains a reference to the variable "foo", it will be taken from `parameters.Get("foo")`.
|
||||
|
||||
This function returns errors if the combination of expression and parameters cannot be run,
|
||||
such as if a variable in the expression is not present in [parameters].
|
||||
|
||||
In all non-error circumstances, this returns the single value result of the expression and parameters given.
|
||||
e.g., if the expression is "1 + 1", this will return 2.0.
|
||||
e.g., if the expression is "foo + 1" and parameters contains "foo" = 2, this will return 3.0
|
||||
*/
|
||||
func (this EvaluableExpression) Eval(parameters Parameters) (interface{}, error) {
|
||||
|
||||
if this.evaluationStages == nil {
|
||||
return nil, nil
|
||||
}
|
||||
|
||||
if parameters != nil {
|
||||
parameters = &sanitizedParameters{parameters}
|
||||
}
|
||||
return this.evaluateStage(this.evaluationStages, parameters)
|
||||
}
|
||||
|
||||
func (this EvaluableExpression) evaluateStage(stage *evaluationStage, parameters Parameters) (interface{}, error) {
|
||||
|
||||
var left, right interface{}
|
||||
var err error
|
||||
|
||||
if stage.leftStage != nil {
|
||||
left, err = this.evaluateStage(stage.leftStage, parameters)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
}
|
||||
|
||||
if stage.isShortCircuitable() {
|
||||
switch stage.symbol {
|
||||
case AND:
|
||||
if left == false {
|
||||
return false, nil
|
||||
}
|
||||
case OR:
|
||||
if left == true {
|
||||
return true, nil
|
||||
}
|
||||
case COALESCE:
|
||||
if left != nil {
|
||||
return left, nil
|
||||
}
|
||||
|
||||
case TERNARY_TRUE:
|
||||
if left == false {
|
||||
right = shortCircuitHolder
|
||||
}
|
||||
case TERNARY_FALSE:
|
||||
if left != nil {
|
||||
right = shortCircuitHolder
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
if right != shortCircuitHolder && stage.rightStage != nil {
|
||||
right, err = this.evaluateStage(stage.rightStage, parameters)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
}
|
||||
|
||||
if this.ChecksTypes {
|
||||
if stage.typeCheck == nil {
|
||||
|
||||
err = typeCheck(stage.leftTypeCheck, left, stage.symbol, stage.typeErrorFormat)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
err = typeCheck(stage.rightTypeCheck, right, stage.symbol, stage.typeErrorFormat)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
} else {
|
||||
// special case where the type check needs to know both sides to determine if the operator can handle it
|
||||
if !stage.typeCheck(left, right) {
|
||||
errorMsg := fmt.Sprintf(stage.typeErrorFormat, left, stage.symbol.String())
|
||||
return nil, errors.New(errorMsg)
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
return stage.operator(left, right, parameters)
|
||||
}
|
||||
|
||||
func typeCheck(check stageTypeCheck, value interface{}, symbol OperatorSymbol, format string) error {
|
||||
|
||||
if check == nil {
|
||||
return nil
|
||||
}
|
||||
|
||||
if check(value) {
|
||||
return nil
|
||||
}
|
||||
|
||||
errorMsg := fmt.Sprintf(format, value, symbol.String())
|
||||
return errors.New(errorMsg)
|
||||
}
|
||||
|
||||
/*
|
||||
Returns an array representing the ExpressionTokens that make up this expression.
|
||||
*/
|
||||
func (this EvaluableExpression) Tokens() []ExpressionToken {
|
||||
|
||||
return this.tokens
|
||||
}
|
||||
|
||||
/*
|
||||
Returns the original expression used to create this EvaluableExpression.
|
||||
*/
|
||||
func (this EvaluableExpression) String() string {
|
||||
|
||||
return this.inputExpression
|
||||
}
|
||||
|
||||
/*
|
||||
Returns an array representing the variables contained in this EvaluableExpression.
|
||||
*/
|
||||
func (this EvaluableExpression) Vars() []string {
|
||||
var varlist []string
|
||||
for _, val := range this.Tokens() {
|
||||
if val.Kind == VARIABLE {
|
||||
varlist = append(varlist, val.Value.(string))
|
||||
}
|
||||
}
|
||||
return varlist
|
||||
}
|
||||
167
src/vendor/github.com/Knetic/govaluate/EvaluableExpression_sql.go
generated
vendored
Normal file
167
src/vendor/github.com/Knetic/govaluate/EvaluableExpression_sql.go
generated
vendored
Normal file
@ -0,0 +1,167 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
"regexp"
|
||||
"time"
|
||||
)
|
||||
|
||||
/*
|
||||
Returns a string representing this expression as if it were written in SQL.
|
||||
This function assumes that all parameters exist within the same table, and that the table essentially represents
|
||||
a serialized object of some sort (e.g., hibernate).
|
||||
If your data model is more normalized, you may need to consider iterating through each actual token given by `Tokens()`
|
||||
to create your query.
|
||||
|
||||
Boolean values are considered to be "1" for true, "0" for false.
|
||||
|
||||
Times are formatted according to this.QueryDateFormat.
|
||||
*/
|
||||
func (this EvaluableExpression) ToSQLQuery() (string, error) {
|
||||
|
||||
var stream *tokenStream
|
||||
var transactions *expressionOutputStream
|
||||
var transaction string
|
||||
var err error
|
||||
|
||||
stream = newTokenStream(this.tokens)
|
||||
transactions = new(expressionOutputStream)
|
||||
|
||||
for stream.hasNext() {
|
||||
|
||||
transaction, err = this.findNextSQLString(stream, transactions)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
|
||||
transactions.add(transaction)
|
||||
}
|
||||
|
||||
return transactions.createString(" "), nil
|
||||
}
|
||||
|
||||
func (this EvaluableExpression) findNextSQLString(stream *tokenStream, transactions *expressionOutputStream) (string, error) {
|
||||
|
||||
var token ExpressionToken
|
||||
var ret string
|
||||
|
||||
token = stream.next()
|
||||
|
||||
switch token.Kind {
|
||||
|
||||
case STRING:
|
||||
ret = fmt.Sprintf("'%v'", token.Value)
|
||||
case PATTERN:
|
||||
ret = fmt.Sprintf("'%s'", token.Value.(*regexp.Regexp).String())
|
||||
case TIME:
|
||||
ret = fmt.Sprintf("'%s'", token.Value.(time.Time).Format(this.QueryDateFormat))
|
||||
|
||||
case LOGICALOP:
|
||||
switch logicalSymbols[token.Value.(string)] {
|
||||
|
||||
case AND:
|
||||
ret = "AND"
|
||||
case OR:
|
||||
ret = "OR"
|
||||
}
|
||||
|
||||
case BOOLEAN:
|
||||
if token.Value.(bool) {
|
||||
ret = "1"
|
||||
} else {
|
||||
ret = "0"
|
||||
}
|
||||
|
||||
case VARIABLE:
|
||||
ret = fmt.Sprintf("[%s]", token.Value.(string))
|
||||
|
||||
case NUMERIC:
|
||||
ret = fmt.Sprintf("%g", token.Value.(float64))
|
||||
|
||||
case COMPARATOR:
|
||||
switch comparatorSymbols[token.Value.(string)] {
|
||||
|
||||
case EQ:
|
||||
ret = "="
|
||||
case NEQ:
|
||||
ret = "<>"
|
||||
case REQ:
|
||||
ret = "RLIKE"
|
||||
case NREQ:
|
||||
ret = "NOT RLIKE"
|
||||
default:
|
||||
ret = fmt.Sprintf("%s", token.Value.(string))
|
||||
}
|
||||
|
||||
case TERNARY:
|
||||
|
||||
switch ternarySymbols[token.Value.(string)] {
|
||||
|
||||
case COALESCE:
|
||||
|
||||
left := transactions.rollback()
|
||||
right, err := this.findNextSQLString(stream, transactions)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
|
||||
ret = fmt.Sprintf("COALESCE(%v, %v)", left, right)
|
||||
case TERNARY_TRUE:
|
||||
fallthrough
|
||||
case TERNARY_FALSE:
|
||||
return "", errors.New("Ternary operators are unsupported in SQL output")
|
||||
}
|
||||
case PREFIX:
|
||||
switch prefixSymbols[token.Value.(string)] {
|
||||
|
||||
case INVERT:
|
||||
ret = fmt.Sprintf("NOT")
|
||||
default:
|
||||
|
||||
right, err := this.findNextSQLString(stream, transactions)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
|
||||
ret = fmt.Sprintf("%s%s", token.Value.(string), right)
|
||||
}
|
||||
case MODIFIER:
|
||||
|
||||
switch modifierSymbols[token.Value.(string)] {
|
||||
|
||||
case EXPONENT:
|
||||
|
||||
left := transactions.rollback()
|
||||
right, err := this.findNextSQLString(stream, transactions)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
|
||||
ret = fmt.Sprintf("POW(%s, %s)", left, right)
|
||||
case MODULUS:
|
||||
|
||||
left := transactions.rollback()
|
||||
right, err := this.findNextSQLString(stream, transactions)
|
||||
if err != nil {
|
||||
return "", err
|
||||
}
|
||||
|
||||
ret = fmt.Sprintf("MOD(%s, %s)", left, right)
|
||||
default:
|
||||
ret = fmt.Sprintf("%s", token.Value.(string))
|
||||
}
|
||||
case CLAUSE:
|
||||
ret = "("
|
||||
case CLAUSE_CLOSE:
|
||||
ret = ")"
|
||||
case SEPARATOR:
|
||||
ret = ","
|
||||
|
||||
default:
|
||||
errorMsg := fmt.Sprintf("Unrecognized query token '%s' of kind '%s'", token.Value, token.Kind)
|
||||
return "", errors.New(errorMsg)
|
||||
}
|
||||
|
||||
return ret, nil
|
||||
}
|
||||
9
src/vendor/github.com/Knetic/govaluate/ExpressionToken.go
generated
vendored
Normal file
9
src/vendor/github.com/Knetic/govaluate/ExpressionToken.go
generated
vendored
Normal file
@ -0,0 +1,9 @@
|
||||
package govaluate
|
||||
|
||||
/*
|
||||
Represents a single parsed token.
|
||||
*/
|
||||
type ExpressionToken struct {
|
||||
Kind TokenKind
|
||||
Value interface{}
|
||||
}
|
||||
21
src/vendor/github.com/Knetic/govaluate/LICENSE
generated
vendored
Normal file
21
src/vendor/github.com/Knetic/govaluate/LICENSE
generated
vendored
Normal file
@ -0,0 +1,21 @@
|
||||
The MIT License (MIT)
|
||||
|
||||
Copyright (c) 2014-2016 George Lester
|
||||
|
||||
Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
of this software and associated documentation files (the "Software"), to deal
|
||||
in the Software without restriction, including without limitation the rights
|
||||
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
copies of the Software, and to permit persons to whom the Software is
|
||||
furnished to do so, subject to the following conditions:
|
||||
|
||||
The above copyright notice and this permission notice shall be included in all
|
||||
copies or substantial portions of the Software.
|
||||
|
||||
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
SOFTWARE.
|
||||
176
src/vendor/github.com/Knetic/govaluate/MANUAL.md
generated
vendored
Normal file
176
src/vendor/github.com/Knetic/govaluate/MANUAL.md
generated
vendored
Normal file
@ -0,0 +1,176 @@
|
||||
govaluate
|
||||
====
|
||||
|
||||
This library contains quite a lot of functionality, this document is meant to be formal documentation on the operators and features of it.
|
||||
Some of this documentation may duplicate what's in README.md, but should never conflict.
|
||||
|
||||
# Types
|
||||
|
||||
This library only officially deals with four types; `float64`, `bool`, `string`, and arrays.
|
||||
|
||||
All numeric literals, with or without a radix, will be converted to `float64` for evaluation. For instance; in practice, there is no difference between the literals "1.0" and "1", they both end up as `float64`. This matters to users because if you intend to return numeric values from your expressions, then the returned value will be `float64`, not any other numeric type.
|
||||
|
||||
Any string _literal_ (not parameter) which is interpretable as a date will be converted to a `float64` representation of that date's unix time. Any `time.Time` parameters will not be operable with these date literals; such parameters will need to use the `time.Time.Unix()` method to get a numeric representation.
|
||||
|
||||
Arrays are untyped, and can be mixed-type. Internally they're all just `interface{}`. Only two operators can interact with arrays, `IN` and `,`. All other operators will refuse to operate on arrays.
|
||||
|
||||
# Operators
|
||||
|
||||
## Modifiers
|
||||
|
||||
### Addition, concatenation `+`
|
||||
|
||||
If either left or right sides of the `+` operator are a `string`, then this operator will perform string concatenation and return that result. If neither are string, then both must be numeric, and this will return a numeric result.
|
||||
|
||||
Any other case is invalid.
|
||||
|
||||
### Arithmetic `-` `*` `/` `**` `%`
|
||||
|
||||
`**` refers to "take to the power of". For instance, `3 ** 4` == 81.
|
||||
|
||||
* _Left side_: numeric
|
||||
* _Right side_: numeric
|
||||
* _Returns_: numeric
|
||||
|
||||
### Bitwise shifts, masks `>>` `<<` `|` `&` `^`
|
||||
|
||||
All of these operators convert their `float64` left and right sides to `int64`, perform their operation, and then convert back.
|
||||
Given how this library assumes numeric are represented (as `float64`), it is unlikely that this behavior will change, even though it may cause havoc with extremely large or small numbers.
|
||||
|
||||
* _Left side_: numeric
|
||||
* _Right side_: numeric
|
||||
* _Returns_: numeric
|
||||
|
||||
### Negation `-`
|
||||
|
||||
Prefix only. This can never have a left-hand value.
|
||||
|
||||
* _Right side_: numeric
|
||||
* _Returns_: numeric
|
||||
|
||||
### Inversion `!`
|
||||
|
||||
Prefix only. This can never have a left-hand value.
|
||||
|
||||
* _Right side_: bool
|
||||
* _Returns_: bool
|
||||
|
||||
### Bitwise NOT `~`
|
||||
|
||||
Prefix only. This can never have a left-hand value.
|
||||
|
||||
* _Right side_: numeric
|
||||
* _Returns_: numeric
|
||||
|
||||
## Logical Operators
|
||||
|
||||
For all logical operators, this library will short-circuit the operation if the left-hand side is sufficient to determine what to do. For instance, `true || expensiveOperation()` will not actually call `expensiveOperation()`, since it knows the left-hand side is `true`.
|
||||
|
||||
### Logical AND/OR `&&` `||`
|
||||
|
||||
* _Left side_: bool
|
||||
* _Right side_: bool
|
||||
* _Returns_: bool
|
||||
|
||||
### Ternary true `?`
|
||||
|
||||
Checks if the left side is `true`. If so, returns the right side. If the left side is `false`, returns `nil`.
|
||||
In practice, this is commonly used with the other ternary operator.
|
||||
|
||||
* _Left side_: bool
|
||||
* _Right side_: Any type.
|
||||
* _Returns_: Right side or `nil`
|
||||
|
||||
### Ternary false `:`
|
||||
|
||||
Checks if the left side is `nil`. If so, returns the right side. If the left side is non-nil, returns the left side.
|
||||
In practice, this is commonly used with the other ternary operator.
|
||||
|
||||
* _Left side_: Any type.
|
||||
* _Right side_: Any type.
|
||||
* _Returns_: Right side or `nil`
|
||||
|
||||
### Null coalescence `??`
|
||||
|
||||
Similar to the C# operator. If the left value is non-nil, it returns that. If not, then the right-value is returned.
|
||||
|
||||
* _Left side_: Any type.
|
||||
* _Right side_: Any type.
|
||||
* _Returns_: No specific type - whichever is passed to it.
|
||||
|
||||
## Comparators
|
||||
|
||||
### Numeric/lexicographic comparators `>` `<` `>=` `<=`
|
||||
|
||||
If both sides are numeric, this returns the usual greater/lesser behavior that would be expected.
|
||||
If both sides are string, this returns the lexicographic comparison of the strings. This uses Go's standard lexicographic compare.
|
||||
|
||||
* _Accepts_: Left and right side must either be both string, or both numeric.
|
||||
* _Returns_: bool
|
||||
|
||||
### Regex comparators `=~` `!~`
|
||||
|
||||
These use go's standard `regexp` flavor of regex. The left side is expected to be the candidate string, the right side is the pattern. `=~` returns whether or not the candidate string matches the regex pattern given on the right. `!~` is the inverted version of the same logic.
|
||||
|
||||
* _Left side_: string
|
||||
* _Right side_: string
|
||||
* _Returns_: bool
|
||||
|
||||
## Arrays
|
||||
|
||||
### Separator `,`
|
||||
|
||||
The separator, always paired with parenthesis, creates arrays. It must always have both a left and right-hand value, so for instance `(, 0)` and `(0,)` are invalid uses of it.
|
||||
|
||||
Again, this should always be used with parenthesis; like `(1, 2, 3, 4)`.
|
||||
|
||||
### Membership `IN`
|
||||
|
||||
The only operator with a text name, this operator checks the right-hand side array to see if it contains a value that is equal to the left-side value.
|
||||
Equality is determined by the use of the `==` operator, and this library doesn't check types between the values. Any two values, when cast to `interface{}`, and can still be checked for equality with `==` will act as expected.
|
||||
|
||||
Note that you can use a parameter for the array, but it must be an `[]interface{}`.
|
||||
|
||||
* _Left side_: Any type.
|
||||
* _Right side_: array
|
||||
* _Returns_: bool
|
||||
|
||||
# Parameters
|
||||
|
||||
Parameters must be passed in every time the expression is evaluated. Parameters can be of any type, but will not cause errors unless actually used in an erroneous way. There is no difference in behavior for any of the above operators for parameters - they are type checked when used.
|
||||
|
||||
All `int` and `float` values of any width will be converted to `float64` before use.
|
||||
|
||||
At no point is the parameter structure, or any value thereof, modified by this library.
|
||||
|
||||
## Alternates to maps
|
||||
|
||||
The default form of parameters as a map may not serve your use case. You may have parameters in some other structure, you may want to change the no-parameter-found behavior, or maybe even just have some debugging print statements invoked when a parameter is accessed.
|
||||
|
||||
To do this, define a type that implements the `govaluate.Parameters` interface. When you want to evaluate, instead call `EvaluableExpression.Eval` and pass your parameter structure.
|
||||
|
||||
# Functions
|
||||
|
||||
During expression parsing (_not_ evaluation), a map of functions can be given to `govaluate.NewEvaluableExpressionWithFunctions` (the lengthiest and finest of function names). The resultant expression will be able to invoke those functions during evaluation. Once parsed, an expression cannot have functions added or removed - a new expression will need to be created if you want to change the functions, or behavior of said functions.
|
||||
|
||||
Functions always take the form `<name>(<parameters>)`, including parens. Functions can have an empty list of parameters, like `<name>()`, but still must have parens.
|
||||
|
||||
If the expression contains something that looks like it ought to be a function (such as `foo()`), but no such function was given to it, it will error on parsing.
|
||||
|
||||
Functions must be of type `map[string]govaluate.ExpressionFunction`. `ExpressionFunction`, for brevity, has the following signature:
|
||||
|
||||
`func(args ...interface{}) (interface{}, error)`
|
||||
|
||||
Where `args` is whatever is passed to the function when called. If a non-nil error is returned from a function during evaluation, the evaluation stops and ultimately returns that error to the caller of `Evaluate()` or `Eval()`.
|
||||
|
||||
## Built-in functions
|
||||
|
||||
There aren't any builtin functions. The author is opposed to maintaining a standard library of functions to be used.
|
||||
|
||||
Every use case of this library is different, and even in simple use cases (such as parameters, see above) different users need different behavior, naming, or even functionality. The author prefers that users make their own decisions about what functions they need, and how they operate.
|
||||
|
||||
# Equality
|
||||
|
||||
The `==` and `!=` operators involve a moderately complex workflow. They use [`reflect.DeepEqual`](https://golang.org/pkg/reflect/#DeepEqual). This is for complicated reasons, but there are some types in Go that cannot be compared with the native `==` operator. Arrays, in particular, cannot be compared - Go will panic if you try. One might assume this could be handled with the type checking system in `govaluate`, but unfortunately without reflection there is no way to know if a variable is a slice/array. Worse, structs can be incomparable if they _contain incomparable types_.
|
||||
|
||||
It's all very complicated. Fortunately, Go includes the `reflect.DeepEqual` function to handle all the edge cases. Currently, `govaluate` uses that for all equality/inequality.
|
||||
306
src/vendor/github.com/Knetic/govaluate/OperatorSymbol.go
generated
vendored
Normal file
306
src/vendor/github.com/Knetic/govaluate/OperatorSymbol.go
generated
vendored
Normal file
@ -0,0 +1,306 @@
|
||||
package govaluate
|
||||
|
||||
/*
|
||||
Represents the valid symbols for operators.
|
||||
|
||||
*/
|
||||
type OperatorSymbol int
|
||||
|
||||
const (
|
||||
VALUE OperatorSymbol = iota
|
||||
LITERAL
|
||||
NOOP
|
||||
EQ
|
||||
NEQ
|
||||
GT
|
||||
LT
|
||||
GTE
|
||||
LTE
|
||||
REQ
|
||||
NREQ
|
||||
IN
|
||||
|
||||
AND
|
||||
OR
|
||||
|
||||
PLUS
|
||||
MINUS
|
||||
BITWISE_AND
|
||||
BITWISE_OR
|
||||
BITWISE_XOR
|
||||
BITWISE_LSHIFT
|
||||
BITWISE_RSHIFT
|
||||
MULTIPLY
|
||||
DIVIDE
|
||||
MODULUS
|
||||
EXPONENT
|
||||
|
||||
NEGATE
|
||||
INVERT
|
||||
BITWISE_NOT
|
||||
|
||||
TERNARY_TRUE
|
||||
TERNARY_FALSE
|
||||
COALESCE
|
||||
|
||||
FUNCTIONAL
|
||||
SEPARATE
|
||||
)
|
||||
|
||||
type operatorPrecedence int
|
||||
|
||||
const (
|
||||
noopPrecedence operatorPrecedence = iota
|
||||
valuePrecedence
|
||||
functionalPrecedence
|
||||
prefixPrecedence
|
||||
exponentialPrecedence
|
||||
additivePrecedence
|
||||
bitwisePrecedence
|
||||
bitwiseShiftPrecedence
|
||||
multiplicativePrecedence
|
||||
comparatorPrecedence
|
||||
ternaryPrecedence
|
||||
logicalAndPrecedence
|
||||
logicalOrPrecedence
|
||||
separatePrecedence
|
||||
)
|
||||
|
||||
func findOperatorPrecedenceForSymbol(symbol OperatorSymbol) operatorPrecedence {
|
||||
|
||||
switch symbol {
|
||||
case NOOP:
|
||||
return noopPrecedence
|
||||
case VALUE:
|
||||
return valuePrecedence
|
||||
case EQ:
|
||||
fallthrough
|
||||
case NEQ:
|
||||
fallthrough
|
||||
case GT:
|
||||
fallthrough
|
||||
case LT:
|
||||
fallthrough
|
||||
case GTE:
|
||||
fallthrough
|
||||
case LTE:
|
||||
fallthrough
|
||||
case REQ:
|
||||
fallthrough
|
||||
case NREQ:
|
||||
fallthrough
|
||||
case IN:
|
||||
return comparatorPrecedence
|
||||
case AND:
|
||||
return logicalAndPrecedence
|
||||
case OR:
|
||||
return logicalOrPrecedence
|
||||
case BITWISE_AND:
|
||||
fallthrough
|
||||
case BITWISE_OR:
|
||||
fallthrough
|
||||
case BITWISE_XOR:
|
||||
return bitwisePrecedence
|
||||
case BITWISE_LSHIFT:
|
||||
fallthrough
|
||||
case BITWISE_RSHIFT:
|
||||
return bitwiseShiftPrecedence
|
||||
case PLUS:
|
||||
fallthrough
|
||||
case MINUS:
|
||||
return additivePrecedence
|
||||
case MULTIPLY:
|
||||
fallthrough
|
||||
case DIVIDE:
|
||||
fallthrough
|
||||
case MODULUS:
|
||||
return multiplicativePrecedence
|
||||
case EXPONENT:
|
||||
return exponentialPrecedence
|
||||
case BITWISE_NOT:
|
||||
fallthrough
|
||||
case NEGATE:
|
||||
fallthrough
|
||||
case INVERT:
|
||||
return prefixPrecedence
|
||||
case COALESCE:
|
||||
fallthrough
|
||||
case TERNARY_TRUE:
|
||||
fallthrough
|
||||
case TERNARY_FALSE:
|
||||
return ternaryPrecedence
|
||||
case FUNCTIONAL:
|
||||
return functionalPrecedence
|
||||
case SEPARATE:
|
||||
return separatePrecedence
|
||||
}
|
||||
|
||||
return valuePrecedence
|
||||
}
|
||||
|
||||
/*
|
||||
Map of all valid comparators, and their string equivalents.
|
||||
Used during parsing of expressions to determine if a symbol is, in fact, a comparator.
|
||||
Also used during evaluation to determine exactly which comparator is being used.
|
||||
*/
|
||||
var comparatorSymbols = map[string]OperatorSymbol{
|
||||
"==": EQ,
|
||||
"!=": NEQ,
|
||||
">": GT,
|
||||
">=": GTE,
|
||||
"<": LT,
|
||||
"<=": LTE,
|
||||
"=~": REQ,
|
||||
"!~": NREQ,
|
||||
"in": IN,
|
||||
}
|
||||
|
||||
var logicalSymbols = map[string]OperatorSymbol{
|
||||
"&&": AND,
|
||||
"||": OR,
|
||||
}
|
||||
|
||||
var bitwiseSymbols = map[string]OperatorSymbol{
|
||||
"^": BITWISE_XOR,
|
||||
"&": BITWISE_AND,
|
||||
"|": BITWISE_OR,
|
||||
}
|
||||
|
||||
var bitwiseShiftSymbols = map[string]OperatorSymbol{
|
||||
">>": BITWISE_RSHIFT,
|
||||
"<<": BITWISE_LSHIFT,
|
||||
}
|
||||
|
||||
var additiveSymbols = map[string]OperatorSymbol{
|
||||
"+": PLUS,
|
||||
"-": MINUS,
|
||||
}
|
||||
|
||||
var multiplicativeSymbols = map[string]OperatorSymbol{
|
||||
"*": MULTIPLY,
|
||||
"/": DIVIDE,
|
||||
"%": MODULUS,
|
||||
}
|
||||
|
||||
var exponentialSymbolsS = map[string]OperatorSymbol{
|
||||
"**": EXPONENT,
|
||||
}
|
||||
|
||||
var prefixSymbols = map[string]OperatorSymbol{
|
||||
"-": NEGATE,
|
||||
"!": INVERT,
|
||||
"~": BITWISE_NOT,
|
||||
}
|
||||
|
||||
var ternarySymbols = map[string]OperatorSymbol{
|
||||
"?": TERNARY_TRUE,
|
||||
":": TERNARY_FALSE,
|
||||
"??": COALESCE,
|
||||
}
|
||||
|
||||
// this is defined separately from additiveSymbols et al because it's needed for parsing, not stage planning.
|
||||
var modifierSymbols = map[string]OperatorSymbol{
|
||||
"+": PLUS,
|
||||
"-": MINUS,
|
||||
"*": MULTIPLY,
|
||||
"/": DIVIDE,
|
||||
"%": MODULUS,
|
||||
"**": EXPONENT,
|
||||
"&": BITWISE_AND,
|
||||
"|": BITWISE_OR,
|
||||
"^": BITWISE_XOR,
|
||||
">>": BITWISE_RSHIFT,
|
||||
"<<": BITWISE_LSHIFT,
|
||||
}
|
||||
|
||||
var separatorSymbols = map[string]OperatorSymbol{
|
||||
",": SEPARATE,
|
||||
}
|
||||
|
||||
/*
|
||||
Returns true if this operator is contained by the given array of candidate symbols.
|
||||
False otherwise.
|
||||
*/
|
||||
func (this OperatorSymbol) IsModifierType(candidate []OperatorSymbol) bool {
|
||||
|
||||
for _, symbolType := range candidate {
|
||||
if this == symbolType {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
/*
|
||||
Generally used when formatting type check errors.
|
||||
We could store the stringified symbol somewhere else and not require a duplicated codeblock to translate
|
||||
OperatorSymbol to string, but that would require more memory, and another field somewhere.
|
||||
Adding operators is rare enough that we just stringify it here instead.
|
||||
*/
|
||||
func (this OperatorSymbol) String() string {
|
||||
|
||||
switch this {
|
||||
case NOOP:
|
||||
return "NOOP"
|
||||
case VALUE:
|
||||
return "VALUE"
|
||||
case EQ:
|
||||
return "="
|
||||
case NEQ:
|
||||
return "!="
|
||||
case GT:
|
||||
return ">"
|
||||
case LT:
|
||||
return "<"
|
||||
case GTE:
|
||||
return ">="
|
||||
case LTE:
|
||||
return "<="
|
||||
case REQ:
|
||||
return "=~"
|
||||
case NREQ:
|
||||
return "!~"
|
||||
case AND:
|
||||
return "&&"
|
||||
case OR:
|
||||
return "||"
|
||||
case IN:
|
||||
return "in"
|
||||
case BITWISE_AND:
|
||||
return "&"
|
||||
case BITWISE_OR:
|
||||
return "|"
|
||||
case BITWISE_XOR:
|
||||
return "^"
|
||||
case BITWISE_LSHIFT:
|
||||
return "<<"
|
||||
case BITWISE_RSHIFT:
|
||||
return ">>"
|
||||
case PLUS:
|
||||
return "+"
|
||||
case MINUS:
|
||||
return "-"
|
||||
case MULTIPLY:
|
||||
return "*"
|
||||
case DIVIDE:
|
||||
return "/"
|
||||
case MODULUS:
|
||||
return "%"
|
||||
case EXPONENT:
|
||||
return "**"
|
||||
case NEGATE:
|
||||
return "-"
|
||||
case INVERT:
|
||||
return "!"
|
||||
case BITWISE_NOT:
|
||||
return "~"
|
||||
case TERNARY_TRUE:
|
||||
return "?"
|
||||
case TERNARY_FALSE:
|
||||
return ":"
|
||||
case COALESCE:
|
||||
return "??"
|
||||
}
|
||||
return ""
|
||||
}
|
||||
210
src/vendor/github.com/Knetic/govaluate/README.md
generated
vendored
Normal file
210
src/vendor/github.com/Knetic/govaluate/README.md
generated
vendored
Normal file
@ -0,0 +1,210 @@
|
||||
govaluate
|
||||
====
|
||||
|
||||
[](https://travis-ci.org/Knetic/govaluate)
|
||||
[](https://godoc.org/github.com/Knetic/govaluate)
|
||||
|
||||
|
||||
Provides support for evaluating arbitrary C-like artithmetic/string expressions.
|
||||
|
||||
Why can't you just write these expressions in code?
|
||||
--
|
||||
|
||||
Sometimes, you can't know ahead-of-time what an expression will look like, or you want those expressions to be configurable.
|
||||
Perhaps you've got a set of data running through your application, and you want to allow your users to specify some validations to run on it before committing it to a database. Or maybe you've written a monitoring framework which is capable of gathering a bunch of metrics, then evaluating a few expressions to see if any metrics should be alerted upon, but the conditions for alerting are different for each monitor.
|
||||
|
||||
A lot of people wind up writing their own half-baked style of evaluation language that fits their needs, but isn't complete. Or they wind up baking the expression into the actual executable, even if they know it's subject to change. These strategies may work, but they take time to implement, time for users to learn, and induce technical debt as requirements change. This library is meant to cover all the normal C-like expressions, so that you don't have to reinvent one of the oldest wheels on a computer.
|
||||
|
||||
How do I use it?
|
||||
--
|
||||
|
||||
You create a new EvaluableExpression, then call "Evaluate" on it.
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("10 > 0");
|
||||
result, err := expression.Evaluate(nil);
|
||||
// result is now set to "true", the bool value.
|
||||
```
|
||||
|
||||
Cool, but how about with parameters?
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("foo > 0");
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
parameters["foo"] = -1;
|
||||
|
||||
result, err := expression.Evaluate(parameters);
|
||||
// result is now set to "false", the bool value.
|
||||
```
|
||||
|
||||
That's cool, but we can almost certainly have done all that in code. What about a complex use case that involves some math?
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("(requests_made * requests_succeeded / 100) >= 90");
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
parameters["requests_made"] = 100;
|
||||
parameters["requests_succeeded"] = 80;
|
||||
|
||||
result, err := expression.Evaluate(parameters);
|
||||
// result is now set to "false", the bool value.
|
||||
```
|
||||
|
||||
Or maybe you want to check the status of an alive check ("smoketest") page, which will be a string?
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("http_response_body == 'service is ok'");
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
parameters["http_response_body"] = "service is ok";
|
||||
|
||||
result, err := expression.Evaluate(parameters);
|
||||
// result is now set to "true", the bool value.
|
||||
```
|
||||
|
||||
These examples have all returned boolean values, but it's equally possible to return numeric ones.
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("(mem_used / total_mem) * 100");
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
parameters["total_mem"] = 1024;
|
||||
parameters["mem_used"] = 512;
|
||||
|
||||
result, err := expression.Evaluate(parameters);
|
||||
// result is now set to "50.0", the float64 value.
|
||||
```
|
||||
|
||||
You can also do date parsing, though the formats are somewhat limited. Stick to RF3339, ISO8061, unix date, or ruby date formats. If you're having trouble getting a date string to parse, check the list of formats actually used: [parsing.go:248](https://github.com/Knetic/govaluate/blob/0580e9b47a69125afa0e4ebd1cf93c49eb5a43ec/parsing.go#L258).
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("'2014-01-02' > '2014-01-01 23:59:59'");
|
||||
result, err := expression.Evaluate(nil);
|
||||
|
||||
// result is now set to true
|
||||
```
|
||||
|
||||
Expressions are parsed once, and can be re-used multiple times. Parsing is the compute-intensive phase of the process, so if you intend to use the same expression with different parameters, just parse it once. Like so;
|
||||
|
||||
```go
|
||||
expression, err := govaluate.NewEvaluableExpression("response_time <= 100");
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
|
||||
for {
|
||||
parameters["response_time"] = pingSomething();
|
||||
result, err := expression.Evaluate(parameters)
|
||||
}
|
||||
```
|
||||
|
||||
The normal C-standard order of operators is respected. When writing an expression, be sure that you either order the operators correctly, or use parenthesis to clarify which portions of an expression should be run first.
|
||||
|
||||
Escaping characters
|
||||
--
|
||||
|
||||
Sometimes you'll have parameters that have spaces, slashes, pluses, ampersands or some other character
|
||||
that this library interprets as something special. For example, the following expression will not
|
||||
act as one might expect:
|
||||
|
||||
"response-time < 100"
|
||||
|
||||
As written, the library will parse it as "[response] minus [time] is less than 100". In reality,
|
||||
"response-time" is meant to be one variable that just happens to have a dash in it.
|
||||
|
||||
There are two ways to work around this. First, you can escape the entire parameter name:
|
||||
|
||||
"[response-time] < 100"
|
||||
|
||||
Or you can use backslashes to escape only the minus sign.
|
||||
|
||||
"response\\-time < 100"
|
||||
|
||||
Backslashes can be used anywhere in an expression to escape the very next character. Square bracketed parameter names can be used instead of plain parameter names at any time.
|
||||
|
||||
Functions
|
||||
--
|
||||
|
||||
You may have cases where you want to call a function on a parameter during execution of the expression. Perhaps you want to aggregate some set of data, but don't know the exact aggregation you want to use until you're writing the expression itself. Or maybe you have a mathematical operation you want to perform, for which there is no operator; like `log` or `tan` or `sqrt`. For cases like this, you can provide a map of functions to `NewEvaluableExpressionWithFunctions`, which will then be able to use them during execution. For instance;
|
||||
|
||||
```go
|
||||
functions := map[string]govaluate.ExpressionFunction {
|
||||
"strlen": func(args ...interface{}) (interface{}, error) {
|
||||
length := len(args[0].(string))
|
||||
return (float64)(length), nil
|
||||
},
|
||||
}
|
||||
|
||||
expString := "strlen('someReallyLongInputString') <= 16"
|
||||
expression, _ := govaluate.NewEvaluableExpressionWithFunctions(expString, functions)
|
||||
|
||||
result, _ := expression.Evaluate(nil)
|
||||
// result is now "false", the boolean value
|
||||
```
|
||||
|
||||
Functions can accept any number of arguments, correctly handles nested functions, and arguments can be of any type (even if none of this library's operators support evaluation of that type). For instance, each of these usages of functions in an expression are valid (assuming that the appropriate functions and parameters are given):
|
||||
|
||||
```go
|
||||
"sqrt(x1 ** y1, x2 ** y2)"
|
||||
"max(someValue, abs(anotherValue), 10 * lastValue)"
|
||||
```
|
||||
|
||||
Functions cannot be passed as parameters, they must be known at the time when the expression is parsed, and are unchangeable after parsing.
|
||||
|
||||
What operators and types does this support?
|
||||
--
|
||||
|
||||
* Modifiers: `+` `-` `/` `*` `&` `|` `^` `**` `%` `>>` `<<`
|
||||
* Comparators: `>` `>=` `<` `<=` `==` `!=` `=~` `!~`
|
||||
* Logical ops: `||` `&&`
|
||||
* Numeric constants, as 64-bit floating point (`12345.678`)
|
||||
* String constants (single quotes: `'foobar'`)
|
||||
* Date constants (single quotes, using any permutation of RFC3339, ISO8601, ruby date, or unix date; date parsing is automatically tried with any string constant)
|
||||
* Boolean constants: `true` `false`
|
||||
* Parenthesis to control order of evaluation `(` `)`
|
||||
* Arrays (anything separated by `,` within parenthesis: `(1, 2, 'foo')`)
|
||||
* Prefixes: `!` `-` `~`
|
||||
* Ternary conditional: `?` `:`
|
||||
* Null coalescence: `??`
|
||||
|
||||
See [MANUAL.md](https://github.com/Knetic/govaluate/blob/master/MANUAL.md) for exacting details on what types each operator supports.
|
||||
|
||||
Types
|
||||
--
|
||||
|
||||
Some operators don't make sense when used with some types. For instance, what does it mean to get the modulo of a string? What happens if you check to see if two numbers are logically AND'ed together?
|
||||
|
||||
Everyone has a different intuition about the answers to these questions. To prevent confusion, this library will _refuse to operate_ upon types for which there is not an unambiguous meaning for the operation. See [MANUAL.md](https://github.com/Knetic/govaluate/blob/master/MANUAL.md) for details about what operators are valid for which types.
|
||||
|
||||
Benchmarks
|
||||
--
|
||||
|
||||
If you're concerned about the overhead of this library, a good range of benchmarks are built into this repo. You can run them with `go test -bench=.`. The library is built with an eye towards being quick, but has not been aggressively profiled and optimized. For most applications, though, it is completely fine.
|
||||
|
||||
For a very rough idea of performance, here are the results output from a benchmark run on a 3rd-gen Macbook Pro (Linux Mint 17.1).
|
||||
|
||||
```
|
||||
BenchmarkSingleParse-12 1000000 1382 ns/op
|
||||
BenchmarkSimpleParse-12 200000 10771 ns/op
|
||||
BenchmarkFullParse-12 30000 49383 ns/op
|
||||
BenchmarkEvaluationSingle-12 50000000 30.1 ns/op
|
||||
BenchmarkEvaluationNumericLiteral-12 10000000 119 ns/op
|
||||
BenchmarkEvaluationLiteralModifiers-12 10000000 236 ns/op
|
||||
BenchmarkEvaluationParameters-12 5000000 260 ns/op
|
||||
BenchmarkEvaluationParametersModifiers-12 3000000 547 ns/op
|
||||
BenchmarkComplexExpression-12 2000000 963 ns/op
|
||||
BenchmarkRegexExpression-12 100000 20357 ns/op
|
||||
BenchmarkConstantRegexExpression-12 1000000 1392 ns/op
|
||||
ok
|
||||
```
|
||||
|
||||
API Breaks
|
||||
--
|
||||
|
||||
While this library has very few cases which will ever result in an API break, it can (and [has](https://github.com/Knetic/govaluate/releases/tag/2.0.0)) happened. If you are using this in production, vendor the commit you've tested against, or use gopkg.in to redirect your import (e.g., `import "gopkg.in/Knetic/govaluate.v2"`). Master branch (while infrequent) _may_ at some point contain API breaking changes, and the author will have no way to communicate these to downstreams, other than creating a new major release.
|
||||
|
||||
Releases will explicitly state when an API break happens, and if they do not specify an API break it should be safe to upgrade.
|
||||
|
||||
License
|
||||
--
|
||||
|
||||
This project is licensed under the MIT general use license. You're free to integrate, fork, and play with this code as you feel fit without consulting the author, as long as you provide proper credit to the author in your works.
|
||||
72
src/vendor/github.com/Knetic/govaluate/TokenKind.go
generated
vendored
Normal file
72
src/vendor/github.com/Knetic/govaluate/TokenKind.go
generated
vendored
Normal file
@ -0,0 +1,72 @@
|
||||
package govaluate
|
||||
|
||||
/*
|
||||
Represents all valid types of tokens that a token can be.
|
||||
*/
|
||||
type TokenKind int
|
||||
|
||||
const (
|
||||
UNKNOWN TokenKind = iota
|
||||
|
||||
PREFIX
|
||||
NUMERIC
|
||||
BOOLEAN
|
||||
STRING
|
||||
PATTERN
|
||||
TIME
|
||||
VARIABLE
|
||||
FUNCTION
|
||||
SEPARATOR
|
||||
|
||||
COMPARATOR
|
||||
LOGICALOP
|
||||
MODIFIER
|
||||
|
||||
CLAUSE
|
||||
CLAUSE_CLOSE
|
||||
|
||||
TERNARY
|
||||
)
|
||||
|
||||
/*
|
||||
GetTokenKindString returns a string that describes the given TokenKind.
|
||||
e.g., when passed the NUMERIC TokenKind, this returns the string "NUMERIC".
|
||||
*/
|
||||
func (kind TokenKind) String() string {
|
||||
|
||||
switch kind {
|
||||
|
||||
case PREFIX:
|
||||
return "PREFIX"
|
||||
case NUMERIC:
|
||||
return "NUMERIC"
|
||||
case BOOLEAN:
|
||||
return "BOOLEAN"
|
||||
case STRING:
|
||||
return "STRING"
|
||||
case PATTERN:
|
||||
return "PATTERN"
|
||||
case TIME:
|
||||
return "TIME"
|
||||
case VARIABLE:
|
||||
return "VARIABLE"
|
||||
case FUNCTION:
|
||||
return "FUNCTION"
|
||||
case SEPARATOR:
|
||||
return "SEPARATOR"
|
||||
case COMPARATOR:
|
||||
return "COMPARATOR"
|
||||
case LOGICALOP:
|
||||
return "LOGICALOP"
|
||||
case MODIFIER:
|
||||
return "MODIFIER"
|
||||
case CLAUSE:
|
||||
return "CLAUSE"
|
||||
case CLAUSE_CLOSE:
|
||||
return "CLAUSE_CLOSE"
|
||||
case TERNARY:
|
||||
return "TERNARY"
|
||||
}
|
||||
|
||||
return "UNKNOWN"
|
||||
}
|
||||
359
src/vendor/github.com/Knetic/govaluate/evaluationStage.go
generated
vendored
Normal file
359
src/vendor/github.com/Knetic/govaluate/evaluationStage.go
generated
vendored
Normal file
@ -0,0 +1,359 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
"math"
|
||||
"regexp"
|
||||
"reflect"
|
||||
)
|
||||
|
||||
const (
|
||||
logicalErrorFormat string = "Value '%v' cannot be used with the logical operator '%v', it is not a bool"
|
||||
modifierErrorFormat string = "Value '%v' cannot be used with the modifier '%v', it is not a number"
|
||||
comparatorErrorFormat string = "Value '%v' cannot be used with the comparator '%v', it is not a number"
|
||||
ternaryErrorFormat string = "Value '%v' cannot be used with the ternary operator '%v', it is not a bool"
|
||||
prefixErrorFormat string = "Value '%v' cannot be used with the prefix '%v'"
|
||||
)
|
||||
|
||||
type evaluationOperator func(left interface{}, right interface{}, parameters Parameters) (interface{}, error)
|
||||
type stageTypeCheck func(value interface{}) bool
|
||||
type stageCombinedTypeCheck func(left interface{}, right interface{}) bool
|
||||
|
||||
type evaluationStage struct {
|
||||
symbol OperatorSymbol
|
||||
|
||||
leftStage, rightStage *evaluationStage
|
||||
|
||||
// the operation that will be used to evaluate this stage (such as adding [left] to [right] and return the result)
|
||||
operator evaluationOperator
|
||||
|
||||
// ensures that both left and right values are appropriate for this stage. Returns an error if they aren't operable.
|
||||
leftTypeCheck stageTypeCheck
|
||||
rightTypeCheck stageTypeCheck
|
||||
|
||||
// if specified, will override whatever is used in "leftTypeCheck" and "rightTypeCheck".
|
||||
// primarily used for specific operators that don't care which side a given type is on, but still requires one side to be of a given type
|
||||
// (like string concat)
|
||||
typeCheck stageCombinedTypeCheck
|
||||
|
||||
// regardless of which type check is used, this string format will be used as the error message for type errors
|
||||
typeErrorFormat string
|
||||
}
|
||||
|
||||
var (
|
||||
_true = interface{}(true)
|
||||
_false = interface{}(false)
|
||||
)
|
||||
|
||||
func (this *evaluationStage) swapWith(other *evaluationStage) {
|
||||
|
||||
temp := *other
|
||||
other.setToNonStage(*this)
|
||||
this.setToNonStage(temp)
|
||||
}
|
||||
|
||||
func (this *evaluationStage) setToNonStage(other evaluationStage) {
|
||||
|
||||
this.symbol = other.symbol
|
||||
this.operator = other.operator
|
||||
this.leftTypeCheck = other.leftTypeCheck
|
||||
this.rightTypeCheck = other.rightTypeCheck
|
||||
this.typeCheck = other.typeCheck
|
||||
this.typeErrorFormat = other.typeErrorFormat
|
||||
}
|
||||
|
||||
func (this *evaluationStage) isShortCircuitable() bool {
|
||||
|
||||
switch this.symbol {
|
||||
case AND:
|
||||
fallthrough
|
||||
case OR:
|
||||
fallthrough
|
||||
case TERNARY_TRUE:
|
||||
fallthrough
|
||||
case TERNARY_FALSE:
|
||||
fallthrough
|
||||
case COALESCE:
|
||||
return true
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
func noopStageRight(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return right, nil
|
||||
}
|
||||
|
||||
func addStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
// string concat if either are strings
|
||||
if isString(left) || isString(right) {
|
||||
return fmt.Sprintf("%v%v", left, right), nil
|
||||
}
|
||||
|
||||
return left.(float64) + right.(float64), nil
|
||||
}
|
||||
func subtractStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return left.(float64) - right.(float64), nil
|
||||
}
|
||||
func multiplyStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return left.(float64) * right.(float64), nil
|
||||
}
|
||||
func divideStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return left.(float64) / right.(float64), nil
|
||||
}
|
||||
func exponentStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return math.Pow(left.(float64), right.(float64)), nil
|
||||
}
|
||||
func modulusStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return math.Mod(left.(float64), right.(float64)), nil
|
||||
}
|
||||
func gteStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if isString(left) && isString(right) {
|
||||
return boolIface(left.(string) >= right.(string)), nil
|
||||
}
|
||||
return boolIface(left.(float64) >= right.(float64)), nil
|
||||
}
|
||||
func gtStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if isString(left) && isString(right) {
|
||||
return boolIface(left.(string) > right.(string)), nil
|
||||
}
|
||||
return boolIface(left.(float64) > right.(float64)), nil
|
||||
}
|
||||
func lteStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if isString(left) && isString(right) {
|
||||
return boolIface(left.(string) <= right.(string)), nil
|
||||
}
|
||||
return boolIface(left.(float64) <= right.(float64)), nil
|
||||
}
|
||||
func ltStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if isString(left) && isString(right) {
|
||||
return boolIface(left.(string) < right.(string)), nil
|
||||
}
|
||||
return boolIface(left.(float64) < right.(float64)), nil
|
||||
}
|
||||
func equalStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return boolIface(reflect.DeepEqual(left, right)), nil
|
||||
}
|
||||
func notEqualStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return boolIface(!reflect.DeepEqual(left, right)), nil
|
||||
}
|
||||
func andStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return boolIface(left.(bool) && right.(bool)), nil
|
||||
}
|
||||
func orStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return boolIface(left.(bool) || right.(bool)), nil
|
||||
}
|
||||
func negateStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return -right.(float64), nil
|
||||
}
|
||||
func invertStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return boolIface(!right.(bool)), nil
|
||||
}
|
||||
func bitwiseNotStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(^int64(right.(float64))), nil
|
||||
}
|
||||
func ternaryIfStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if left.(bool) {
|
||||
return right, nil
|
||||
}
|
||||
return nil, nil
|
||||
}
|
||||
func ternaryElseStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
if left != nil {
|
||||
return left, nil
|
||||
}
|
||||
return right, nil
|
||||
}
|
||||
|
||||
func regexStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
var pattern *regexp.Regexp
|
||||
var err error
|
||||
|
||||
switch right.(type) {
|
||||
case string:
|
||||
pattern, err = regexp.Compile(right.(string))
|
||||
if err != nil {
|
||||
return nil, errors.New(fmt.Sprintf("Unable to compile regexp pattern '%v': %v", right, err))
|
||||
}
|
||||
case *regexp.Regexp:
|
||||
pattern = right.(*regexp.Regexp)
|
||||
}
|
||||
|
||||
return pattern.Match([]byte(left.(string))), nil
|
||||
}
|
||||
|
||||
func notRegexStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
ret, err := regexStage(left, right, parameters)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
return !(ret.(bool)), nil
|
||||
}
|
||||
|
||||
func bitwiseOrStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(int64(left.(float64)) | int64(right.(float64))), nil
|
||||
}
|
||||
func bitwiseAndStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(int64(left.(float64)) & int64(right.(float64))), nil
|
||||
}
|
||||
func bitwiseXORStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(int64(left.(float64)) ^ int64(right.(float64))), nil
|
||||
}
|
||||
func leftShiftStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(uint64(left.(float64)) << uint64(right.(float64))), nil
|
||||
}
|
||||
func rightShiftStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return float64(uint64(left.(float64)) >> uint64(right.(float64))), nil
|
||||
}
|
||||
|
||||
func makeParameterStage(parameterName string) evaluationOperator {
|
||||
|
||||
return func(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
value, err := parameters.Get(parameterName)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
return value, nil
|
||||
}
|
||||
}
|
||||
|
||||
func makeLiteralStage(literal interface{}) evaluationOperator {
|
||||
return func(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
return literal, nil
|
||||
}
|
||||
}
|
||||
|
||||
func makeFunctionStage(function ExpressionFunction) evaluationOperator {
|
||||
|
||||
return func(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
if right == nil {
|
||||
return function()
|
||||
}
|
||||
|
||||
switch right.(type) {
|
||||
case []interface{}:
|
||||
return function(right.([]interface{})...)
|
||||
default:
|
||||
return function(right)
|
||||
}
|
||||
|
||||
}
|
||||
}
|
||||
|
||||
func separatorStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
var ret []interface{}
|
||||
|
||||
switch left.(type) {
|
||||
case []interface{}:
|
||||
ret = append(left.([]interface{}), right)
|
||||
default:
|
||||
ret = []interface{}{left, right}
|
||||
}
|
||||
|
||||
return ret, nil
|
||||
}
|
||||
|
||||
func inStage(left interface{}, right interface{}, parameters Parameters) (interface{}, error) {
|
||||
|
||||
for _, value := range right.([]interface{}) {
|
||||
if left == value {
|
||||
return true, nil
|
||||
}
|
||||
}
|
||||
return false, nil
|
||||
}
|
||||
|
||||
//
|
||||
|
||||
func isString(value interface{}) bool {
|
||||
|
||||
switch value.(type) {
|
||||
case string:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func isRegexOrString(value interface{}) bool {
|
||||
|
||||
switch value.(type) {
|
||||
case string:
|
||||
return true
|
||||
case *regexp.Regexp:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func isBool(value interface{}) bool {
|
||||
switch value.(type) {
|
||||
case bool:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func isFloat64(value interface{}) bool {
|
||||
switch value.(type) {
|
||||
case float64:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
/*
|
||||
Addition usually means between numbers, but can also mean string concat.
|
||||
String concat needs one (or both) of the sides to be a string.
|
||||
*/
|
||||
func additionTypeCheck(left interface{}, right interface{}) bool {
|
||||
|
||||
if isFloat64(left) && isFloat64(right) {
|
||||
return true
|
||||
}
|
||||
if !isString(left) && !isString(right) {
|
||||
return false
|
||||
}
|
||||
return true
|
||||
}
|
||||
|
||||
/*
|
||||
Comparison can either be between numbers, or lexicographic between two strings,
|
||||
but never between the two.
|
||||
*/
|
||||
func comparatorTypeCheck(left interface{}, right interface{}) bool {
|
||||
|
||||
if isFloat64(left) && isFloat64(right) {
|
||||
return true
|
||||
}
|
||||
if isString(left) && isString(right) {
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func isArray(value interface{}) bool {
|
||||
switch value.(type) {
|
||||
case []interface{}:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
/*
|
||||
Converting a boolean to an interface{} requires an allocation.
|
||||
We can use interned bools to avoid this cost.
|
||||
*/
|
||||
func boolIface(b bool) interface{} {
|
||||
if b {
|
||||
return _true
|
||||
}
|
||||
return _false
|
||||
}
|
||||
8
src/vendor/github.com/Knetic/govaluate/expressionFunctions.go
generated
vendored
Normal file
8
src/vendor/github.com/Knetic/govaluate/expressionFunctions.go
generated
vendored
Normal file
@ -0,0 +1,8 @@
|
||||
package govaluate
|
||||
|
||||
/*
|
||||
Represents a function that can be called from within an expression.
|
||||
This method must return an error if, for any reason, it is unable to produce exactly one unambiguous result.
|
||||
An error returned will halt execution of the expression.
|
||||
*/
|
||||
type ExpressionFunction func(arguments ...interface{}) (interface{}, error)
|
||||
46
src/vendor/github.com/Knetic/govaluate/expressionOutputStream.go
generated
vendored
Normal file
46
src/vendor/github.com/Knetic/govaluate/expressionOutputStream.go
generated
vendored
Normal file
@ -0,0 +1,46 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"bytes"
|
||||
)
|
||||
|
||||
/*
|
||||
Holds a series of "transactions" which represent each token as it is output by an outputter (such as ToSQLQuery()).
|
||||
Some outputs (such as SQL) require a function call or non-c-like syntax to represent an expression.
|
||||
To accomplish this, this struct keeps track of each translated token as it is output, and can return and rollback those transactions.
|
||||
*/
|
||||
type expressionOutputStream struct {
|
||||
transactions []string
|
||||
}
|
||||
|
||||
func (this *expressionOutputStream) add(transaction string) {
|
||||
this.transactions = append(this.transactions, transaction)
|
||||
}
|
||||
|
||||
func (this *expressionOutputStream) rollback() string {
|
||||
|
||||
index := len(this.transactions) - 1
|
||||
ret := this.transactions[index]
|
||||
|
||||
this.transactions = this.transactions[:index]
|
||||
return ret
|
||||
}
|
||||
|
||||
func (this *expressionOutputStream) createString(delimiter string) string {
|
||||
|
||||
var retBuffer bytes.Buffer
|
||||
var transaction string
|
||||
|
||||
penultimate := len(this.transactions) - 1
|
||||
|
||||
for i := 0; i < penultimate; i++ {
|
||||
|
||||
transaction = this.transactions[i]
|
||||
|
||||
retBuffer.WriteString(transaction)
|
||||
retBuffer.WriteString(delimiter)
|
||||
}
|
||||
retBuffer.WriteString(this.transactions[penultimate])
|
||||
|
||||
return retBuffer.String()
|
||||
}
|
||||
350
src/vendor/github.com/Knetic/govaluate/lexerState.go
generated
vendored
Normal file
350
src/vendor/github.com/Knetic/govaluate/lexerState.go
generated
vendored
Normal file
@ -0,0 +1,350 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
)
|
||||
|
||||
type lexerState struct {
|
||||
isEOF bool
|
||||
isNullable bool
|
||||
kind TokenKind
|
||||
validNextKinds []TokenKind
|
||||
}
|
||||
|
||||
// lexer states.
|
||||
// Constant for all purposes except compiler.
|
||||
var validLexerStates = []lexerState{
|
||||
|
||||
lexerState{
|
||||
kind: UNKNOWN,
|
||||
isEOF: false,
|
||||
isNullable: true,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
PATTERN,
|
||||
FUNCTION,
|
||||
STRING,
|
||||
TIME,
|
||||
CLAUSE,
|
||||
},
|
||||
},
|
||||
|
||||
lexerState{
|
||||
|
||||
kind: CLAUSE,
|
||||
isEOF: false,
|
||||
isNullable: true,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
PATTERN,
|
||||
FUNCTION,
|
||||
STRING,
|
||||
TIME,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
},
|
||||
},
|
||||
|
||||
lexerState{
|
||||
|
||||
kind: CLAUSE_CLOSE,
|
||||
isEOF: true,
|
||||
isNullable: true,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
COMPARATOR,
|
||||
MODIFIER,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
STRING,
|
||||
PATTERN,
|
||||
TIME,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
LOGICALOP,
|
||||
TERNARY,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
|
||||
lexerState{
|
||||
|
||||
kind: NUMERIC,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
TERNARY,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: BOOLEAN,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
TERNARY,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: STRING,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
TERNARY,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: TIME,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: PATTERN,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: VARIABLE,
|
||||
isEOF: true,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
MODIFIER,
|
||||
COMPARATOR,
|
||||
LOGICALOP,
|
||||
CLAUSE_CLOSE,
|
||||
TERNARY,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: MODIFIER,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
STRING,
|
||||
BOOLEAN,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: COMPARATOR,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
STRING,
|
||||
TIME,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
PATTERN,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: LOGICALOP,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
STRING,
|
||||
TIME,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: PREFIX,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
CLAUSE,
|
||||
CLAUSE_CLOSE,
|
||||
},
|
||||
},
|
||||
|
||||
lexerState{
|
||||
|
||||
kind: TERNARY,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
STRING,
|
||||
TIME,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
CLAUSE,
|
||||
SEPARATOR,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: FUNCTION,
|
||||
isEOF: false,
|
||||
isNullable: false,
|
||||
validNextKinds: []TokenKind{
|
||||
CLAUSE,
|
||||
},
|
||||
},
|
||||
lexerState{
|
||||
|
||||
kind: SEPARATOR,
|
||||
isEOF: false,
|
||||
isNullable: true,
|
||||
validNextKinds: []TokenKind{
|
||||
|
||||
PREFIX,
|
||||
NUMERIC,
|
||||
BOOLEAN,
|
||||
STRING,
|
||||
TIME,
|
||||
VARIABLE,
|
||||
FUNCTION,
|
||||
CLAUSE,
|
||||
},
|
||||
},
|
||||
}
|
||||
|
||||
func (this lexerState) canTransitionTo(kind TokenKind) bool {
|
||||
|
||||
for _, validKind := range this.validNextKinds {
|
||||
|
||||
if validKind == kind {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
func checkExpressionSyntax(tokens []ExpressionToken) error {
|
||||
|
||||
var state lexerState
|
||||
var lastToken ExpressionToken
|
||||
var err error
|
||||
|
||||
state = validLexerStates[0]
|
||||
|
||||
for _, token := range tokens {
|
||||
|
||||
if !state.canTransitionTo(token.Kind) {
|
||||
|
||||
// call out a specific error for tokens looking like they want to be functions.
|
||||
if lastToken.Kind == VARIABLE && token.Kind == CLAUSE {
|
||||
return errors.New("Undefined function " + lastToken.Value.(string))
|
||||
}
|
||||
|
||||
firstStateName := fmt.Sprintf("%s [%v]", state.kind.String(), lastToken.Value)
|
||||
nextStateName := fmt.Sprintf("%s [%v]", token.Kind.String(), token.Value)
|
||||
|
||||
return errors.New("Cannot transition token types from " + firstStateName + " to " + nextStateName)
|
||||
}
|
||||
|
||||
state, err = getLexerStateForToken(token.Kind)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
if !state.isNullable && token.Value == nil {
|
||||
|
||||
errorMsg := fmt.Sprintf("Token kind '%v' cannot have a nil value", token.Kind.String())
|
||||
return errors.New(errorMsg)
|
||||
}
|
||||
|
||||
lastToken = token
|
||||
}
|
||||
|
||||
if !state.isEOF {
|
||||
return errors.New("Unexpected end of expression")
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
func getLexerStateForToken(kind TokenKind) (lexerState, error) {
|
||||
|
||||
for _, possibleState := range validLexerStates {
|
||||
|
||||
if possibleState.kind == kind {
|
||||
return possibleState, nil
|
||||
}
|
||||
}
|
||||
|
||||
errorMsg := fmt.Sprintf("No lexer state found for token kind '%v'\n", kind.String())
|
||||
return validLexerStates[0], errors.New(errorMsg)
|
||||
}
|
||||
39
src/vendor/github.com/Knetic/govaluate/lexerStream.go
generated
vendored
Normal file
39
src/vendor/github.com/Knetic/govaluate/lexerStream.go
generated
vendored
Normal file
@ -0,0 +1,39 @@
|
||||
package govaluate
|
||||
|
||||
type lexerStream struct {
|
||||
source []rune
|
||||
position int
|
||||
length int
|
||||
}
|
||||
|
||||
func newLexerStream(source string) *lexerStream {
|
||||
|
||||
var ret *lexerStream
|
||||
var runes []rune
|
||||
|
||||
for _, character := range source {
|
||||
runes = append(runes, character)
|
||||
}
|
||||
|
||||
ret = new(lexerStream)
|
||||
ret.source = runes
|
||||
ret.length = len(runes)
|
||||
return ret
|
||||
}
|
||||
|
||||
func (this *lexerStream) readCharacter() rune {
|
||||
|
||||
var character rune
|
||||
|
||||
character = this.source[this.position]
|
||||
this.position += 1
|
||||
return character
|
||||
}
|
||||
|
||||
func (this *lexerStream) rewind(amount int) {
|
||||
this.position -= amount
|
||||
}
|
||||
|
||||
func (this lexerStream) canRead() bool {
|
||||
return this.position < this.length
|
||||
}
|
||||
32
src/vendor/github.com/Knetic/govaluate/parameters.go
generated
vendored
Normal file
32
src/vendor/github.com/Knetic/govaluate/parameters.go
generated
vendored
Normal file
@ -0,0 +1,32 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
)
|
||||
|
||||
/*
|
||||
Parameters is a collection of named parameters that can be used by an EvaluableExpression to retrieve parameters
|
||||
when an expression tries to use them.
|
||||
*/
|
||||
type Parameters interface {
|
||||
|
||||
/*
|
||||
Get gets the parameter of the given name, or an error if the parameter is unavailable.
|
||||
Failure to find the given parameter should be indicated by returning an error.
|
||||
*/
|
||||
Get(name string) (interface{}, error)
|
||||
}
|
||||
|
||||
type MapParameters map[string]interface{}
|
||||
|
||||
func (p MapParameters) Get(name string) (interface{}, error) {
|
||||
|
||||
value, found := p[name]
|
||||
|
||||
if !found {
|
||||
errorMessage := "No parameter '" + name + "' found."
|
||||
return nil, errors.New(errorMessage)
|
||||
}
|
||||
|
||||
return value, nil
|
||||
}
|
||||
450
src/vendor/github.com/Knetic/govaluate/parsing.go
generated
vendored
Normal file
450
src/vendor/github.com/Knetic/govaluate/parsing.go
generated
vendored
Normal file
@ -0,0 +1,450 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"bytes"
|
||||
"errors"
|
||||
"fmt"
|
||||
"regexp"
|
||||
"strconv"
|
||||
"time"
|
||||
"unicode"
|
||||
)
|
||||
|
||||
func parseTokens(expression string, functions map[string]ExpressionFunction) ([]ExpressionToken, error) {
|
||||
|
||||
var ret []ExpressionToken
|
||||
var token ExpressionToken
|
||||
var stream *lexerStream
|
||||
var state lexerState
|
||||
var err error
|
||||
var found bool
|
||||
|
||||
stream = newLexerStream(expression)
|
||||
state = validLexerStates[0]
|
||||
|
||||
for stream.canRead() {
|
||||
|
||||
token, err, found = readToken(stream, state, functions)
|
||||
|
||||
if err != nil {
|
||||
return ret, err
|
||||
}
|
||||
|
||||
if !found {
|
||||
break
|
||||
}
|
||||
|
||||
state, err = getLexerStateForToken(token.Kind)
|
||||
if err != nil {
|
||||
return ret, err
|
||||
}
|
||||
|
||||
// append this valid token
|
||||
ret = append(ret, token)
|
||||
}
|
||||
|
||||
err = checkBalance(ret)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
return ret, nil
|
||||
}
|
||||
|
||||
func readToken(stream *lexerStream, state lexerState, functions map[string]ExpressionFunction) (ExpressionToken, error, bool) {
|
||||
|
||||
var function ExpressionFunction
|
||||
var ret ExpressionToken
|
||||
var tokenValue interface{}
|
||||
var tokenTime time.Time
|
||||
var tokenString string
|
||||
var kind TokenKind
|
||||
var character rune
|
||||
var found bool
|
||||
var completed bool
|
||||
var err error
|
||||
|
||||
// numeric is 0-9, or .
|
||||
// string starts with '
|
||||
// variable is alphanumeric, always starts with a letter
|
||||
// bracket always means variable
|
||||
// symbols are anything non-alphanumeric
|
||||
// all others read into a buffer until they reach the end of the stream
|
||||
for stream.canRead() {
|
||||
|
||||
character = stream.readCharacter()
|
||||
|
||||
if unicode.IsSpace(character) {
|
||||
continue
|
||||
}
|
||||
|
||||
kind = UNKNOWN
|
||||
|
||||
// numeric constant
|
||||
if isNumeric(character) {
|
||||
|
||||
tokenString = readTokenUntilFalse(stream, isNumeric)
|
||||
tokenValue, err = strconv.ParseFloat(tokenString, 64)
|
||||
|
||||
if err != nil {
|
||||
errorMsg := fmt.Sprintf("Unable to parse numeric value '%v' to float64\n", tokenString)
|
||||
return ExpressionToken{}, errors.New(errorMsg), false
|
||||
}
|
||||
kind = NUMERIC
|
||||
break
|
||||
}
|
||||
|
||||
// comma, separator
|
||||
if character == ',' {
|
||||
|
||||
tokenValue = ","
|
||||
kind = SEPARATOR
|
||||
break
|
||||
}
|
||||
|
||||
// escaped variable
|
||||
if character == '[' {
|
||||
|
||||
tokenValue, completed = readUntilFalse(stream, true, false, true, isNotClosingBracket)
|
||||
kind = VARIABLE
|
||||
|
||||
if !completed {
|
||||
return ExpressionToken{}, errors.New("Unclosed parameter bracket"), false
|
||||
}
|
||||
|
||||
// above method normally rewinds us to the closing bracket, which we want to skip.
|
||||
stream.rewind(-1)
|
||||
break
|
||||
}
|
||||
|
||||
// regular variable - or function?
|
||||
if unicode.IsLetter(character) {
|
||||
|
||||
tokenString = readTokenUntilFalse(stream, isVariableName)
|
||||
|
||||
tokenValue = tokenString
|
||||
kind = VARIABLE
|
||||
|
||||
// boolean?
|
||||
if tokenValue == "true" {
|
||||
|
||||
kind = BOOLEAN
|
||||
tokenValue = true
|
||||
} else {
|
||||
|
||||
if tokenValue == "false" {
|
||||
|
||||
kind = BOOLEAN
|
||||
tokenValue = false
|
||||
}
|
||||
}
|
||||
|
||||
// textual operator?
|
||||
if tokenValue == "in" || tokenValue == "IN" {
|
||||
|
||||
// force lower case for consistency
|
||||
tokenValue = "in"
|
||||
kind = COMPARATOR
|
||||
}
|
||||
|
||||
// function?
|
||||
function, found = functions[tokenString]
|
||||
if found {
|
||||
kind = FUNCTION
|
||||
tokenValue = function
|
||||
}
|
||||
break
|
||||
}
|
||||
|
||||
if !isNotQuote(character) {
|
||||
tokenValue, completed = readUntilFalse(stream, true, false, true, isNotQuote)
|
||||
|
||||
if !completed {
|
||||
return ExpressionToken{}, errors.New("Unclosed string literal"), false
|
||||
}
|
||||
|
||||
// advance the stream one position, since reading until false assumes the terminator is a real token
|
||||
stream.rewind(-1)
|
||||
|
||||
// check to see if this can be parsed as a time.
|
||||
tokenTime, found = tryParseTime(tokenValue.(string))
|
||||
if found {
|
||||
kind = TIME
|
||||
tokenValue = tokenTime
|
||||
} else {
|
||||
kind = STRING
|
||||
}
|
||||
break
|
||||
}
|
||||
|
||||
if character == '(' {
|
||||
tokenValue = character
|
||||
kind = CLAUSE
|
||||
break
|
||||
}
|
||||
|
||||
if character == ')' {
|
||||
tokenValue = character
|
||||
kind = CLAUSE_CLOSE
|
||||
break
|
||||
}
|
||||
|
||||
// must be a known symbol
|
||||
tokenString = readTokenUntilFalse(stream, isNotAlphanumeric)
|
||||
tokenValue = tokenString
|
||||
|
||||
// quick hack for the case where "-" can mean "prefixed negation" or "minus", which are used
|
||||
// very differently.
|
||||
if state.canTransitionTo(PREFIX) {
|
||||
_, found = prefixSymbols[tokenString]
|
||||
if found {
|
||||
|
||||
kind = PREFIX
|
||||
break
|
||||
}
|
||||
}
|
||||
_, found = modifierSymbols[tokenString]
|
||||
if found {
|
||||
|
||||
kind = MODIFIER
|
||||
break
|
||||
}
|
||||
|
||||
_, found = logicalSymbols[tokenString]
|
||||
if found {
|
||||
|
||||
kind = LOGICALOP
|
||||
break
|
||||
}
|
||||
|
||||
_, found = comparatorSymbols[tokenString]
|
||||
if found {
|
||||
|
||||
kind = COMPARATOR
|
||||
break
|
||||
}
|
||||
|
||||
_, found = ternarySymbols[tokenString]
|
||||
if found {
|
||||
|
||||
kind = TERNARY
|
||||
break
|
||||
}
|
||||
|
||||
errorMessage := fmt.Sprintf("Invalid token: '%s'", tokenString)
|
||||
return ret, errors.New(errorMessage), false
|
||||
}
|
||||
|
||||
ret.Kind = kind
|
||||
ret.Value = tokenValue
|
||||
|
||||
return ret, nil, (kind != UNKNOWN)
|
||||
}
|
||||
|
||||
func readTokenUntilFalse(stream *lexerStream, condition func(rune) bool) string {
|
||||
|
||||
var ret string
|
||||
|
||||
stream.rewind(1)
|
||||
ret, _ = readUntilFalse(stream, false, true, true, condition)
|
||||
return ret
|
||||
}
|
||||
|
||||
/*
|
||||
Returns the string that was read until the given [condition] was false, or whitespace was broken.
|
||||
Returns false if the stream ended before whitespace was broken or condition was met.
|
||||
*/
|
||||
func readUntilFalse(stream *lexerStream, includeWhitespace bool, breakWhitespace bool, allowEscaping bool, condition func(rune) bool) (string, bool) {
|
||||
|
||||
var tokenBuffer bytes.Buffer
|
||||
var character rune
|
||||
var conditioned bool
|
||||
|
||||
conditioned = false
|
||||
|
||||
for stream.canRead() {
|
||||
|
||||
character = stream.readCharacter()
|
||||
|
||||
// Use backslashes to escape anything
|
||||
if allowEscaping && character == '\\' {
|
||||
|
||||
character = stream.readCharacter()
|
||||
tokenBuffer.WriteString(string(character))
|
||||
continue
|
||||
}
|
||||
|
||||
if unicode.IsSpace(character) {
|
||||
|
||||
if breakWhitespace && tokenBuffer.Len() > 0 {
|
||||
conditioned = true
|
||||
break
|
||||
}
|
||||
if !includeWhitespace {
|
||||
continue
|
||||
}
|
||||
}
|
||||
|
||||
if condition(character) {
|
||||
tokenBuffer.WriteString(string(character))
|
||||
} else {
|
||||
conditioned = true
|
||||
stream.rewind(1)
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
return tokenBuffer.String(), conditioned
|
||||
}
|
||||
|
||||
/*
|
||||
Checks to see if any optimizations can be performed on the given [tokens], which form a complete, valid expression.
|
||||
The returns slice will represent the optimized (or unmodified) list of tokens to use.
|
||||
*/
|
||||
func optimizeTokens(tokens []ExpressionToken) ([]ExpressionToken, error) {
|
||||
|
||||
var token ExpressionToken
|
||||
var symbol OperatorSymbol
|
||||
var err error
|
||||
var index int
|
||||
|
||||
for index, token = range tokens {
|
||||
|
||||
// if we find a regex operator, and the right-hand value is a constant, precompile and replace with a pattern.
|
||||
if token.Kind != COMPARATOR {
|
||||
continue
|
||||
}
|
||||
|
||||
symbol = comparatorSymbols[token.Value.(string)]
|
||||
if symbol != REQ && symbol != NREQ {
|
||||
continue
|
||||
}
|
||||
|
||||
index++
|
||||
token = tokens[index]
|
||||
if token.Kind == STRING {
|
||||
|
||||
token.Kind = PATTERN
|
||||
token.Value, err = regexp.Compile(token.Value.(string))
|
||||
|
||||
if err != nil {
|
||||
return tokens, err
|
||||
}
|
||||
|
||||
tokens[index] = token
|
||||
}
|
||||
}
|
||||
return tokens, nil
|
||||
}
|
||||
|
||||
/*
|
||||
Checks the balance of tokens which have multiple parts, such as parenthesis.
|
||||
*/
|
||||
func checkBalance(tokens []ExpressionToken) error {
|
||||
|
||||
var stream *tokenStream
|
||||
var token ExpressionToken
|
||||
var parens int
|
||||
|
||||
stream = newTokenStream(tokens)
|
||||
|
||||
for stream.hasNext() {
|
||||
|
||||
token = stream.next()
|
||||
if token.Kind == CLAUSE {
|
||||
parens++
|
||||
continue
|
||||
}
|
||||
if token.Kind == CLAUSE_CLOSE {
|
||||
parens--
|
||||
continue
|
||||
}
|
||||
}
|
||||
|
||||
if parens != 0 {
|
||||
return errors.New("Unbalanced parenthesis")
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
func isNumeric(character rune) bool {
|
||||
|
||||
return unicode.IsDigit(character) || character == '.'
|
||||
}
|
||||
|
||||
func isNotQuote(character rune) bool {
|
||||
|
||||
return character != '\'' && character != '"'
|
||||
}
|
||||
|
||||
func isNotAlphanumeric(character rune) bool {
|
||||
|
||||
return !(unicode.IsDigit(character) ||
|
||||
unicode.IsLetter(character) ||
|
||||
character == '(' ||
|
||||
character == ')' ||
|
||||
!isNotQuote(character))
|
||||
}
|
||||
|
||||
func isVariableName(character rune) bool {
|
||||
|
||||
return unicode.IsLetter(character) ||
|
||||
unicode.IsDigit(character) ||
|
||||
character == '_'
|
||||
}
|
||||
|
||||
func isNotClosingBracket(character rune) bool {
|
||||
|
||||
return character != ']'
|
||||
}
|
||||
|
||||
/*
|
||||
Attempts to parse the [candidate] as a Time.
|
||||
Tries a series of standardized date formats, returns the Time if one applies,
|
||||
otherwise returns false through the second return.
|
||||
*/
|
||||
func tryParseTime(candidate string) (time.Time, bool) {
|
||||
|
||||
var ret time.Time
|
||||
var found bool
|
||||
|
||||
timeFormats := [...]string{
|
||||
time.ANSIC,
|
||||
time.UnixDate,
|
||||
time.RubyDate,
|
||||
time.Kitchen,
|
||||
time.RFC3339,
|
||||
time.RFC3339Nano,
|
||||
"2006-01-02", // RFC 3339
|
||||
"2006-01-02 15:04", // RFC 3339 with minutes
|
||||
"2006-01-02 15:04:05", // RFC 3339 with seconds
|
||||
"2006-01-02 15:04:05-07:00", // RFC 3339 with seconds and timezone
|
||||
"2006-01-02T15Z0700", // ISO8601 with hour
|
||||
"2006-01-02T15:04Z0700", // ISO8601 with minutes
|
||||
"2006-01-02T15:04:05Z0700", // ISO8601 with seconds
|
||||
"2006-01-02T15:04:05.999999999Z0700", // ISO8601 with nanoseconds
|
||||
}
|
||||
|
||||
for _, format := range timeFormats {
|
||||
|
||||
ret, found = tryParseExactTime(candidate, format)
|
||||
if found {
|
||||
return ret, true
|
||||
}
|
||||
}
|
||||
|
||||
return time.Now(), false
|
||||
}
|
||||
|
||||
func tryParseExactTime(candidate string, format string) (time.Time, bool) {
|
||||
|
||||
var ret time.Time
|
||||
var err error
|
||||
|
||||
ret, err = time.ParseInLocation(format, candidate, time.Local)
|
||||
if err != nil {
|
||||
return time.Now(), false
|
||||
}
|
||||
|
||||
return ret, true
|
||||
}
|
||||
71
src/vendor/github.com/Knetic/govaluate/sanitizedParameters.go
generated
vendored
Normal file
71
src/vendor/github.com/Knetic/govaluate/sanitizedParameters.go
generated
vendored
Normal file
@ -0,0 +1,71 @@
|
||||
package govaluate
|
||||
|
||||
// sanitizedParameters is a wrapper for Parameters that does sanitization as
|
||||
// parameters are accessed.
|
||||
type sanitizedParameters struct {
|
||||
orig Parameters
|
||||
}
|
||||
|
||||
func (p sanitizedParameters) Get(key string) (interface{}, error) {
|
||||
value, err := p.orig.Get(key)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
// should be converted to fixed point?
|
||||
if isFixedPoint(value) {
|
||||
return castFixedPoint(value), nil
|
||||
}
|
||||
|
||||
return value, nil
|
||||
}
|
||||
|
||||
func isFixedPoint(value interface{}) bool {
|
||||
|
||||
switch value.(type) {
|
||||
case uint8:
|
||||
return true
|
||||
case uint16:
|
||||
return true
|
||||
case uint32:
|
||||
return true
|
||||
case uint64:
|
||||
return true
|
||||
case int8:
|
||||
return true
|
||||
case int16:
|
||||
return true
|
||||
case int32:
|
||||
return true
|
||||
case int64:
|
||||
return true
|
||||
case int:
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func castFixedPoint(value interface{}) float64 {
|
||||
switch value.(type) {
|
||||
case uint8:
|
||||
return float64(value.(uint8))
|
||||
case uint16:
|
||||
return float64(value.(uint16))
|
||||
case uint32:
|
||||
return float64(value.(uint32))
|
||||
case uint64:
|
||||
return float64(value.(uint64))
|
||||
case int8:
|
||||
return float64(value.(int8))
|
||||
case int16:
|
||||
return float64(value.(int16))
|
||||
case int32:
|
||||
return float64(value.(int32))
|
||||
case int64:
|
||||
return float64(value.(int64))
|
||||
case int:
|
||||
return float64(value.(int))
|
||||
}
|
||||
|
||||
return 0.0
|
||||
}
|
||||
675
src/vendor/github.com/Knetic/govaluate/stagePlanner.go
generated
vendored
Normal file
675
src/vendor/github.com/Knetic/govaluate/stagePlanner.go
generated
vendored
Normal file
@ -0,0 +1,675 @@
|
||||
package govaluate
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"time"
|
||||
"fmt"
|
||||
)
|
||||
|
||||
var stageSymbolMap = map[OperatorSymbol]evaluationOperator{
|
||||
EQ: equalStage,
|
||||
NEQ: notEqualStage,
|
||||
GT: gtStage,
|
||||
LT: ltStage,
|
||||
GTE: gteStage,
|
||||
LTE: lteStage,
|
||||
REQ: regexStage,
|
||||
NREQ: notRegexStage,
|
||||
AND: andStage,
|
||||
OR: orStage,
|
||||
IN: inStage,
|
||||
BITWISE_OR: bitwiseOrStage,
|
||||
BITWISE_AND: bitwiseAndStage,
|
||||
BITWISE_XOR: bitwiseXORStage,
|
||||
BITWISE_LSHIFT: leftShiftStage,
|
||||
BITWISE_RSHIFT: rightShiftStage,
|
||||
PLUS: addStage,
|
||||
MINUS: subtractStage,
|
||||
MULTIPLY: multiplyStage,
|
||||
DIVIDE: divideStage,
|
||||
MODULUS: modulusStage,
|
||||
EXPONENT: exponentStage,
|
||||
NEGATE: negateStage,
|
||||
INVERT: invertStage,
|
||||
BITWISE_NOT: bitwiseNotStage,
|
||||
TERNARY_TRUE: ternaryIfStage,
|
||||
TERNARY_FALSE: ternaryElseStage,
|
||||
COALESCE: ternaryElseStage,
|
||||
SEPARATE: separatorStage,
|
||||
}
|
||||
|
||||
/*
|
||||
A "precedent" is a function which will recursively parse new evaluateionStages from a given stream of tokens.
|
||||
It's called a `precedent` because it is expected to handle exactly what precedence of operator,
|
||||
and defer to other `precedent`s for other operators.
|
||||
*/
|
||||
type precedent func(stream *tokenStream) (*evaluationStage, error)
|
||||
|
||||
/*
|
||||
A convenience function for specifying the behavior of a `precedent`.
|
||||
Most `precedent` functions can be described by the same function, just with different type checks, symbols, and error formats.
|
||||
This struct is passed to `makePrecedentFromPlanner` to create a `precedent` function.
|
||||
*/
|
||||
type precedencePlanner struct {
|
||||
validSymbols map[string]OperatorSymbol
|
||||
validKinds []TokenKind
|
||||
|
||||
typeErrorFormat string
|
||||
|
||||
next precedent
|
||||
nextRight precedent
|
||||
}
|
||||
|
||||
var planPrefix precedent
|
||||
var planExponential precedent
|
||||
var planMultiplicative precedent
|
||||
var planAdditive precedent
|
||||
var planBitwise precedent
|
||||
var planShift precedent
|
||||
var planComparator precedent
|
||||
var planLogicalAnd precedent
|
||||
var planLogicalOr precedent
|
||||
var planTernary precedent
|
||||
var planSeparator precedent
|
||||
|
||||
func init() {
|
||||
|
||||
// all these stages can use the same code (in `planPrecedenceLevel`) to execute,
|
||||
// they simply need different type checks, symbols, and recursive precedents.
|
||||
// While not all precedent phases are listed here, most can be represented this way.
|
||||
planPrefix = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: prefixSymbols,
|
||||
validKinds: []TokenKind{PREFIX},
|
||||
typeErrorFormat: prefixErrorFormat,
|
||||
nextRight: planFunction,
|
||||
})
|
||||
planExponential = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: exponentialSymbolsS,
|
||||
validKinds: []TokenKind{MODIFIER},
|
||||
typeErrorFormat: modifierErrorFormat,
|
||||
next: planFunction,
|
||||
})
|
||||
planMultiplicative = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: multiplicativeSymbols,
|
||||
validKinds: []TokenKind{MODIFIER},
|
||||
typeErrorFormat: modifierErrorFormat,
|
||||
next: planExponential,
|
||||
})
|
||||
planAdditive = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: additiveSymbols,
|
||||
validKinds: []TokenKind{MODIFIER},
|
||||
typeErrorFormat: modifierErrorFormat,
|
||||
next: planMultiplicative,
|
||||
})
|
||||
planShift = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: bitwiseShiftSymbols,
|
||||
validKinds: []TokenKind{MODIFIER},
|
||||
typeErrorFormat: modifierErrorFormat,
|
||||
next: planAdditive,
|
||||
})
|
||||
planBitwise = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: bitwiseSymbols,
|
||||
validKinds: []TokenKind{MODIFIER},
|
||||
typeErrorFormat: modifierErrorFormat,
|
||||
next: planShift,
|
||||
})
|
||||
planComparator = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: comparatorSymbols,
|
||||
validKinds: []TokenKind{COMPARATOR},
|
||||
typeErrorFormat: comparatorErrorFormat,
|
||||
next: planBitwise,
|
||||
})
|
||||
planLogicalAnd = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: map[string]OperatorSymbol{"&&": AND},
|
||||
validKinds: []TokenKind{LOGICALOP},
|
||||
typeErrorFormat: logicalErrorFormat,
|
||||
next: planComparator,
|
||||
})
|
||||
planLogicalOr = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: map[string]OperatorSymbol{"||": OR},
|
||||
validKinds: []TokenKind{LOGICALOP},
|
||||
typeErrorFormat: logicalErrorFormat,
|
||||
next: planLogicalAnd,
|
||||
})
|
||||
planTernary = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: ternarySymbols,
|
||||
validKinds: []TokenKind{TERNARY},
|
||||
typeErrorFormat: ternaryErrorFormat,
|
||||
next: planLogicalOr,
|
||||
})
|
||||
planSeparator = makePrecedentFromPlanner(&precedencePlanner{
|
||||
validSymbols: separatorSymbols,
|
||||
validKinds: []TokenKind{SEPARATOR},
|
||||
next: planTernary,
|
||||
})
|
||||
}
|
||||
|
||||
/*
|
||||
Given a planner, creates a function which will evaluate a specific precedence level of operators,
|
||||
and link it to other `precedent`s which recurse to parse other precedence levels.
|
||||
*/
|
||||
func makePrecedentFromPlanner(planner *precedencePlanner) precedent {
|
||||
|
||||
var generated precedent
|
||||
var nextRight precedent
|
||||
|
||||
generated = func(stream *tokenStream) (*evaluationStage, error) {
|
||||
return planPrecedenceLevel(
|
||||
stream,
|
||||
planner.typeErrorFormat,
|
||||
planner.validSymbols,
|
||||
planner.validKinds,
|
||||
nextRight,
|
||||
planner.next,
|
||||
)
|
||||
}
|
||||
|
||||
if planner.nextRight != nil {
|
||||
nextRight = planner.nextRight
|
||||
} else {
|
||||
nextRight = generated
|
||||
}
|
||||
|
||||
return generated
|
||||
}
|
||||
|
||||
/*
|
||||
Creates a `evaluationStageList` object which represents an execution plan (or tree)
|
||||
which is used to completely evaluate a set of tokens at evaluation-time.
|
||||
The three stages of evaluation can be thought of as parsing strings to tokens, then tokens to a stage list, then evaluation with parameters.
|
||||
*/
|
||||
func planStages(tokens []ExpressionToken) (*evaluationStage, error) {
|
||||
|
||||
stream := newTokenStream(tokens)
|
||||
|
||||
stage, err := planTokens(stream)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
// while we're now fully-planned, we now need to re-order same-precedence operators.
|
||||
// this could probably be avoided with a different planning method
|
||||
reorderStages(stage)
|
||||
|
||||
stage = elideLiterals(stage)
|
||||
return stage, nil
|
||||
}
|
||||
|
||||
func planTokens(stream *tokenStream) (*evaluationStage, error) {
|
||||
|
||||
if !stream.hasNext() {
|
||||
return nil, nil
|
||||
}
|
||||
|
||||
return planSeparator(stream)
|
||||
}
|
||||
|
||||
/*
|
||||
The most usual method of parsing an evaluation stage for a given precedence.
|
||||
Most stages use the same logic
|
||||
*/
|
||||
func planPrecedenceLevel(
|
||||
stream *tokenStream,
|
||||
typeErrorFormat string,
|
||||
validSymbols map[string]OperatorSymbol,
|
||||
validKinds []TokenKind,
|
||||
rightPrecedent precedent,
|
||||
leftPrecedent precedent) (*evaluationStage, error) {
|
||||
|
||||
var token ExpressionToken
|
||||
var symbol OperatorSymbol
|
||||
var leftStage, rightStage *evaluationStage
|
||||
var checks typeChecks
|
||||
var err error
|
||||
var keyFound bool
|
||||
|
||||
if leftPrecedent != nil {
|
||||
|
||||
leftStage, err = leftPrecedent(stream)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
}
|
||||
|
||||
for stream.hasNext() {
|
||||
|
||||
token = stream.next()
|
||||
|
||||
if len(validKinds) > 0 {
|
||||
|
||||
keyFound = false
|
||||
for _, kind := range validKinds {
|
||||
if kind == token.Kind {
|
||||
keyFound = true
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if !keyFound {
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if validSymbols != nil {
|
||||
|
||||
if !isString(token.Value) {
|
||||
break
|
||||
}
|
||||
|
||||
symbol, keyFound = validSymbols[token.Value.(string)]
|
||||
if !keyFound {
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if rightPrecedent != nil {
|
||||
rightStage, err = rightPrecedent(stream)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
}
|
||||
|
||||
checks = findTypeChecks(symbol)
|
||||
|
||||
return &evaluationStage{
|
||||
|
||||
symbol: symbol,
|
||||
leftStage: leftStage,
|
||||
rightStage: rightStage,
|
||||
operator: stageSymbolMap[symbol],
|
||||
|
||||
leftTypeCheck: checks.left,
|
||||
rightTypeCheck: checks.right,
|
||||
typeCheck: checks.combined,
|
||||
typeErrorFormat: typeErrorFormat,
|
||||
}, nil
|
||||
}
|
||||
|
||||
stream.rewind()
|
||||
return leftStage, nil
|
||||
}
|
||||
|
||||
/*
|
||||
A special case where functions need to be of higher precedence than values, and need a special wrapped execution stage operator.
|
||||
*/
|
||||
func planFunction(stream *tokenStream) (*evaluationStage, error) {
|
||||
|
||||
var token ExpressionToken
|
||||
var rightStage *evaluationStage
|
||||
var err error
|
||||
|
||||
token = stream.next()
|
||||
|
||||
if token.Kind != FUNCTION {
|
||||
stream.rewind()
|
||||
return planValue(stream)
|
||||
}
|
||||
|
||||
rightStage, err = planValue(stream)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
return &evaluationStage{
|
||||
|
||||
symbol: FUNCTIONAL,
|
||||
rightStage: rightStage,
|
||||
operator: makeFunctionStage(token.Value.(ExpressionFunction)),
|
||||
typeErrorFormat: "Unable to run function '%v': %v",
|
||||
}, nil
|
||||
}
|
||||
|
||||
/*
|
||||
A truly special precedence function, this handles all the "lowest-case" errata of the process, including literals, parmeters,
|
||||
clauses, and prefixes.
|
||||
*/
|
||||
func planValue(stream *tokenStream) (*evaluationStage, error) {
|
||||
|
||||
var token ExpressionToken
|
||||
var symbol OperatorSymbol
|
||||
var ret *evaluationStage
|
||||
var operator evaluationOperator
|
||||
var err error
|
||||
|
||||
token = stream.next()
|
||||
|
||||
switch token.Kind {
|
||||
|
||||
case CLAUSE:
|
||||
|
||||
ret, err = planTokens(stream)
|
||||
if err != nil {
|
||||
return nil, err
|
||||
}
|
||||
|
||||
// advance past the CLAUSE_CLOSE token. We know that it's a CLAUSE_CLOSE, because at parse-time we check for unbalanced parens.
|
||||
stream.next()
|
||||
|
||||
// the stage we got represents all of the logic contained within the parens
|
||||
// but for technical reasons, we need to wrap this stage in a "noop" stage which breaks long chains of precedence.
|
||||
// see github #33.
|
||||
ret = &evaluationStage {
|
||||
rightStage: ret,
|
||||
operator: noopStageRight,
|
||||
symbol: NOOP,
|
||||
}
|
||||
|
||||
return ret, nil
|
||||
|
||||
case CLAUSE_CLOSE:
|
||||
|
||||
// when functions have empty params, this will be hit. In this case, we don't have any evaluation stage to do,
|
||||
// so we just return nil so that the stage planner continues on its way.
|
||||
stream.rewind()
|
||||
return nil, nil
|
||||
|
||||
case VARIABLE:
|
||||
operator = makeParameterStage(token.Value.(string))
|
||||
|
||||
case NUMERIC:
|
||||
fallthrough
|
||||
case STRING:
|
||||
fallthrough
|
||||
case PATTERN:
|
||||
fallthrough
|
||||
case BOOLEAN:
|
||||
symbol = LITERAL
|
||||
operator = makeLiteralStage(token.Value)
|
||||
case TIME:
|
||||
symbol = LITERAL
|
||||
operator = makeLiteralStage(float64(token.Value.(time.Time).Unix()))
|
||||
|
||||
case PREFIX:
|
||||
stream.rewind()
|
||||
return planPrefix(stream)
|
||||
}
|
||||
|
||||
if operator == nil {
|
||||
errorMsg := fmt.Sprintf("Unable to plan token kind: '%s', value: '%v'", token.Kind.String(), token.Value)
|
||||
return nil, errors.New(errorMsg)
|
||||
}
|
||||
|
||||
return &evaluationStage{
|
||||
symbol: symbol,
|
||||
operator: operator,
|
||||
}, nil
|
||||
}
|
||||
|
||||
/*
|
||||
Convenience function to pass a triplet of typechecks between `findTypeChecks` and `planPrecedenceLevel`.
|
||||
Each of these members may be nil, which indicates that type does not matter for that value.
|
||||
*/
|
||||
type typeChecks struct {
|
||||
left stageTypeCheck
|
||||
right stageTypeCheck
|
||||
combined stageCombinedTypeCheck
|
||||
}
|
||||
|
||||
/*
|
||||
Maps a given [symbol] to a set of typechecks to be used during runtime.
|
||||
*/
|
||||
func findTypeChecks(symbol OperatorSymbol) typeChecks {
|
||||
|
||||
switch symbol {
|
||||
case GT:
|
||||
fallthrough
|
||||
case LT:
|
||||
fallthrough
|
||||
case GTE:
|
||||
fallthrough
|
||||
case LTE:
|
||||
return typeChecks{
|
||||
combined: comparatorTypeCheck,
|
||||
}
|
||||
case REQ:
|
||||
fallthrough
|
||||
case NREQ:
|
||||
return typeChecks{
|
||||
left: isString,
|
||||
right: isRegexOrString,
|
||||
}
|
||||
case AND:
|
||||
fallthrough
|
||||
case OR:
|
||||
return typeChecks{
|
||||
left: isBool,
|
||||
right: isBool,
|
||||
}
|
||||
case IN:
|
||||
return typeChecks{
|
||||
right: isArray,
|
||||
}
|
||||
case BITWISE_LSHIFT:
|
||||
fallthrough
|
||||
case BITWISE_RSHIFT:
|
||||
fallthrough
|
||||
case BITWISE_OR:
|
||||
fallthrough
|
||||
case BITWISE_AND:
|
||||
fallthrough
|
||||
case BITWISE_XOR:
|
||||
return typeChecks{
|
||||
left: isFloat64,
|
||||
right: isFloat64,
|
||||
}
|
||||
case PLUS:
|
||||
return typeChecks{
|
||||
combined: additionTypeCheck,
|
||||
}
|
||||
case MINUS:
|
||||
fallthrough
|
||||
case MULTIPLY:
|
||||
fallthrough
|
||||
case DIVIDE:
|
||||
fallthrough
|
||||
case MODULUS:
|
||||
fallthrough
|
||||
case EXPONENT:
|
||||
return typeChecks{
|
||||
left: isFloat64,
|
||||
right: isFloat64,
|
||||
}
|
||||
case NEGATE:
|
||||
return typeChecks{
|
||||
right: isFloat64,
|
||||
}
|
||||
case INVERT:
|
||||
return typeChecks{
|
||||
right: isBool,
|
||||
}
|
||||
case BITWISE_NOT:
|
||||
return typeChecks{
|
||||
right: isFloat64,
|
||||
}
|
||||
case TERNARY_TRUE:
|
||||
return typeChecks{
|
||||
left: isBool,
|
||||
}
|
||||
|
||||
// unchecked cases
|
||||
case EQ:
|
||||
fallthrough
|
||||
case NEQ:
|
||||
return typeChecks{}
|
||||
case TERNARY_FALSE:
|
||||
fallthrough
|
||||
case COALESCE:
|
||||
fallthrough
|
||||
default:
|
||||
return typeChecks{}
|
||||
}
|
||||
}
|
||||
|
||||
/*
|
||||
During stage planning, stages of equal precedence are parsed such that they'll be evaluated in reverse order.
|
||||
For commutative operators like "+" or "-", it's no big deal. But for order-specific operators, it ruins the expected result.
|
||||
*/
|
||||
func reorderStages(rootStage *evaluationStage) {
|
||||
|
||||
// traverse every rightStage until we find multiples in a row of the same precedence.
|
||||
var identicalPrecedences []*evaluationStage
|
||||
var currentStage, nextStage *evaluationStage
|
||||
var precedence, currentPrecedence operatorPrecedence
|
||||
|
||||
nextStage = rootStage
|
||||
precedence = findOperatorPrecedenceForSymbol(rootStage.symbol)
|
||||
|
||||
for nextStage != nil {
|
||||
|
||||
currentStage = nextStage
|
||||
nextStage = currentStage.rightStage
|
||||
|
||||
// left depth first, since this entire method only looks for precedences down the right side of the tree
|
||||
if currentStage.leftStage != nil {
|
||||
reorderStages(currentStage.leftStage)
|
||||
}
|
||||
|
||||
currentPrecedence = findOperatorPrecedenceForSymbol(currentStage.symbol)
|
||||
|
||||
if currentPrecedence == precedence {
|
||||
identicalPrecedences = append(identicalPrecedences, currentStage)
|
||||
continue
|
||||
}
|
||||
|
||||
// precedence break.
|
||||
// See how many in a row we had, and reorder if there's more than one.
|
||||
if len(identicalPrecedences) > 1 {
|
||||
mirrorStageSubtree(identicalPrecedences)
|
||||
}
|
||||
|
||||
identicalPrecedences = []*evaluationStage{currentStage}
|
||||
precedence = currentPrecedence
|
||||
}
|
||||
|
||||
if len(identicalPrecedences) > 1 {
|
||||
mirrorStageSubtree(identicalPrecedences)
|
||||
}
|
||||
}
|
||||
|
||||
/*
|
||||
Performs a "mirror" on a subtree of stages.
|
||||
This mirror functionally inverts the order of execution for all members of the [stages] list.
|
||||
That list is assumed to be a root-to-leaf (ordered) list of evaluation stages, where each is a right-hand stage of the last.
|
||||
*/
|
||||
func mirrorStageSubtree(stages []*evaluationStage) {
|
||||
|
||||
var rootStage, inverseStage, carryStage, frontStage *evaluationStage
|
||||
|
||||
stagesLength := len(stages)
|
||||
|
||||
// reverse all right/left
|
||||
for _, frontStage = range stages {
|
||||
|
||||
carryStage = frontStage.rightStage
|
||||
frontStage.rightStage = frontStage.leftStage
|
||||
frontStage.leftStage = carryStage
|
||||
}
|
||||
|
||||
// end left swaps with root right
|
||||
rootStage = stages[0]
|
||||
frontStage = stages[stagesLength-1]
|
||||
|
||||
carryStage = frontStage.leftStage
|
||||
frontStage.leftStage = rootStage.rightStage
|
||||
rootStage.rightStage = carryStage
|
||||
|
||||
// for all non-root non-end stages, right is swapped with inverse stage right in list
|
||||
for i := 0; i < (stagesLength-2)/2+1; i++ {
|
||||
|
||||
frontStage = stages[i+1]
|
||||
inverseStage = stages[stagesLength-i-1]
|
||||
|
||||
carryStage = frontStage.rightStage
|
||||
frontStage.rightStage = inverseStage.rightStage
|
||||
inverseStage.rightStage = carryStage
|
||||
}
|
||||
|
||||
// swap all other information with inverse stages
|
||||
for i := 0; i < stagesLength/2; i++ {
|
||||
|
||||
frontStage = stages[i]
|
||||
inverseStage = stages[stagesLength-i-1]
|
||||
frontStage.swapWith(inverseStage)
|
||||
}
|
||||
}
|
||||
|
||||
/*
|
||||
Recurses through all operators in the entire tree, eliding operators where both sides are literals.
|
||||
*/
|
||||
func elideLiterals(root *evaluationStage) *evaluationStage {
|
||||
|
||||
if root.leftStage != nil {
|
||||
root.leftStage = elideLiterals(root.leftStage)
|
||||
}
|
||||
|
||||
if root.rightStage != nil {
|
||||
root.rightStage = elideLiterals(root.rightStage)
|
||||
}
|
||||
|
||||
return elideStage(root)
|
||||
}
|
||||
|
||||
/*
|
||||
Elides a specific stage, if possible.
|
||||
Returns the unmodified [root] stage if it cannot or should not be elided.
|
||||
Otherwise, returns a new stage representing the condensed value from the elided stages.
|
||||
*/
|
||||
func elideStage(root *evaluationStage) *evaluationStage {
|
||||
|
||||
var leftValue, rightValue, result interface{}
|
||||
var err error
|
||||
|
||||
// right side must be a non-nil value. Left side must be nil or a value.
|
||||
if root.rightStage == nil ||
|
||||
root.rightStage.symbol != LITERAL ||
|
||||
root.leftStage == nil ||
|
||||
root.leftStage.symbol != LITERAL {
|
||||
return root
|
||||
}
|
||||
|
||||
// don't elide some operators
|
||||
switch root.symbol {
|
||||
case SEPARATE:
|
||||
fallthrough
|
||||
case IN:
|
||||
return root
|
||||
}
|
||||
|
||||
// both sides are values, get their actual values.
|
||||
// errors should be near-impossible here. If we encounter them, just abort this optimization.
|
||||
leftValue, err = root.leftStage.operator(nil, nil, nil)
|
||||
if err != nil {
|
||||
return root
|
||||
}
|
||||
|
||||
rightValue, err = root.rightStage.operator(nil, nil, nil)
|
||||
if err != nil {
|
||||
return root
|
||||
}
|
||||
|
||||
// typcheck, since the grammar checker is a bit loose with which operator symbols go together.
|
||||
err = typeCheck(root.leftTypeCheck, leftValue, root.symbol, root.typeErrorFormat)
|
||||
if err != nil {
|
||||
return root
|
||||
}
|
||||
|
||||
err = typeCheck(root.rightTypeCheck, rightValue, root.symbol, root.typeErrorFormat)
|
||||
if err != nil {
|
||||
return root
|
||||
}
|
||||
|
||||
if root.typeCheck != nil && !root.typeCheck(leftValue, rightValue) {
|
||||
return root
|
||||
}
|
||||
|
||||
// pre-calculate, and return a new stage representing the result.
|
||||
result, err = root.operator(leftValue, rightValue, nil)
|
||||
if err != nil {
|
||||
return root
|
||||
}
|
||||
|
||||
return &evaluationStage {
|
||||
symbol: LITERAL,
|
||||
operator: makeLiteralStage(result),
|
||||
}
|
||||
}
|
||||
32
src/vendor/github.com/Knetic/govaluate/test.sh
generated
vendored
Executable file
32
src/vendor/github.com/Knetic/govaluate/test.sh
generated
vendored
Executable file
@ -0,0 +1,32 @@
|
||||
#!/bin/bash
|
||||
|
||||
# Script that runs tests, code coverage, and benchmarks all at once.
|
||||
# Builds a symlink in /tmp, mostly to avoid messing with GOPATH at the user's shell level.
|
||||
|
||||
TEMPORARY_PATH="/tmp/govaluate_test"
|
||||
SRC_PATH="${TEMPORARY_PATH}/src"
|
||||
FULL_PATH="${TEMPORARY_PATH}/src/govaluate"
|
||||
|
||||
# set up temporary directory
|
||||
rm -rf "${FULL_PATH}"
|
||||
mkdir -p "${SRC_PATH}"
|
||||
|
||||
ln -s $(pwd) "${FULL_PATH}"
|
||||
export GOPATH="${TEMPORARY_PATH}"
|
||||
|
||||
pushd "${TEMPORARY_PATH}/src/govaluate"
|
||||
|
||||
# run the actual tests.
|
||||
export GOVALUATE_TORTURE_TEST="true"
|
||||
go test -bench=. -benchmem -coverprofile coverage.out
|
||||
status=$?
|
||||
|
||||
if [ "${status}" != 0 ];
|
||||
then
|
||||
exit $status
|
||||
fi
|
||||
|
||||
# coverage
|
||||
go tool cover -func=coverage.out
|
||||
|
||||
popd
|
||||
36
src/vendor/github.com/Knetic/govaluate/tokenStream.go
generated
vendored
Normal file
36
src/vendor/github.com/Knetic/govaluate/tokenStream.go
generated
vendored
Normal file
@ -0,0 +1,36 @@
|
||||
package govaluate
|
||||
|
||||
type tokenStream struct {
|
||||
tokens []ExpressionToken
|
||||
index int
|
||||
tokenLength int
|
||||
}
|
||||
|
||||
func newTokenStream(tokens []ExpressionToken) *tokenStream {
|
||||
|
||||
var ret *tokenStream
|
||||
|
||||
ret = new(tokenStream)
|
||||
ret.tokens = tokens
|
||||
ret.tokenLength = len(tokens)
|
||||
return ret
|
||||
}
|
||||
|
||||
func (this *tokenStream) rewind() {
|
||||
this.index -= 1
|
||||
}
|
||||
|
||||
func (this *tokenStream) next() ExpressionToken {
|
||||
|
||||
var token ExpressionToken
|
||||
|
||||
token = this.tokens[this.index]
|
||||
|
||||
this.index += 1
|
||||
return token
|
||||
}
|
||||
|
||||
func (this tokenStream) hasNext() bool {
|
||||
|
||||
return this.index < this.tokenLength
|
||||
}
|
||||
27
src/vendor/github.com/casbin/casbin/.gitignore
generated
vendored
Normal file
27
src/vendor/github.com/casbin/casbin/.gitignore
generated
vendored
Normal file
@ -0,0 +1,27 @@
|
||||
# Compiled Object files, Static and Dynamic libs (Shared Objects)
|
||||
*.o
|
||||
*.a
|
||||
*.so
|
||||
|
||||
# Folders
|
||||
_obj
|
||||
_test
|
||||
|
||||
# Architecture specific extensions/prefixes
|
||||
*.[568vq]
|
||||
[568vq].out
|
||||
|
||||
*.cgo1.go
|
||||
*.cgo2.c
|
||||
_cgo_defun.c
|
||||
_cgo_gotypes.go
|
||||
_cgo_export.*
|
||||
|
||||
_testmain.go
|
||||
|
||||
*.exe
|
||||
*.test
|
||||
*.prof
|
||||
|
||||
.idea/
|
||||
*.iml
|
||||
12
src/vendor/github.com/casbin/casbin/.travis.yml
generated
vendored
Normal file
12
src/vendor/github.com/casbin/casbin/.travis.yml
generated
vendored
Normal file
@ -0,0 +1,12 @@
|
||||
language: go
|
||||
|
||||
sudo: false
|
||||
|
||||
go:
|
||||
- tip
|
||||
|
||||
before_install:
|
||||
- go get github.com/mattn/goveralls
|
||||
|
||||
script:
|
||||
- $HOME/gopath/bin/goveralls -service=travis-ci
|
||||
201
src/vendor/github.com/casbin/casbin/LICENSE
generated
vendored
Normal file
201
src/vendor/github.com/casbin/casbin/LICENSE
generated
vendored
Normal file
@ -0,0 +1,201 @@
|
||||
Apache License
|
||||
Version 2.0, January 2004
|
||||
http://www.apache.org/licenses/
|
||||
|
||||
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
|
||||
|
||||
1. Definitions.
|
||||
|
||||
"License" shall mean the terms and conditions for use, reproduction,
|
||||
and distribution as defined by Sections 1 through 9 of this document.
|
||||
|
||||
"Licensor" shall mean the copyright owner or entity authorized by
|
||||
the copyright owner that is granting the License.
|
||||
|
||||
"Legal Entity" shall mean the union of the acting entity and all
|
||||
other entities that control, are controlled by, or are under common
|
||||
control with that entity. For the purposes of this definition,
|
||||
"control" means (i) the power, direct or indirect, to cause the
|
||||
direction or management of such entity, whether by contract or
|
||||
otherwise, or (ii) ownership of fifty percent (50%) or more of the
|
||||
outstanding shares, or (iii) beneficial ownership of such entity.
|
||||
|
||||
"You" (or "Your") shall mean an individual or Legal Entity
|
||||
exercising permissions granted by this License.
|
||||
|
||||
"Source" form shall mean the preferred form for making modifications,
|
||||
including but not limited to software source code, documentation
|
||||
source, and configuration files.
|
||||
|
||||
"Object" form shall mean any form resulting from mechanical
|
||||
transformation or translation of a Source form, including but
|
||||
not limited to compiled object code, generated documentation,
|
||||
and conversions to other media types.
|
||||
|
||||
"Work" shall mean the work of authorship, whether in Source or
|
||||
Object form, made available under the License, as indicated by a
|
||||
copyright notice that is included in or attached to the work
|
||||
(an example is provided in the Appendix below).
|
||||
|
||||
"Derivative Works" shall mean any work, whether in Source or Object
|
||||
form, that is based on (or derived from) the Work and for which the
|
||||
editorial revisions, annotations, elaborations, or other modifications
|
||||
represent, as a whole, an original work of authorship. For the purposes
|
||||
of this License, Derivative Works shall not include works that remain
|
||||
separable from, or merely link (or bind by name) to the interfaces of,
|
||||
the Work and Derivative Works thereof.
|
||||
|
||||
"Contribution" shall mean any work of authorship, including
|
||||
the original version of the Work and any modifications or additions
|
||||
to that Work or Derivative Works thereof, that is intentionally
|
||||
submitted to Licensor for inclusion in the Work by the copyright owner
|
||||
or by an individual or Legal Entity authorized to submit on behalf of
|
||||
the copyright owner. For the purposes of this definition, "submitted"
|
||||
means any form of electronic, verbal, or written communication sent
|
||||
to the Licensor or its representatives, including but not limited to
|
||||
communication on electronic mailing lists, source code control systems,
|
||||
and issue tracking systems that are managed by, or on behalf of, the
|
||||
Licensor for the purpose of discussing and improving the Work, but
|
||||
excluding communication that is conspicuously marked or otherwise
|
||||
designated in writing by the copyright owner as "Not a Contribution."
|
||||
|
||||
"Contributor" shall mean Licensor and any individual or Legal Entity
|
||||
on behalf of whom a Contribution has been received by Licensor and
|
||||
subsequently incorporated within the Work.
|
||||
|
||||
2. Grant of Copyright License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
copyright license to reproduce, prepare Derivative Works of,
|
||||
publicly display, publicly perform, sublicense, and distribute the
|
||||
Work and such Derivative Works in Source or Object form.
|
||||
|
||||
3. Grant of Patent License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
(except as stated in this section) patent license to make, have made,
|
||||
use, offer to sell, sell, import, and otherwise transfer the Work,
|
||||
where such license applies only to those patent claims licensable
|
||||
by such Contributor that are necessarily infringed by their
|
||||
Contribution(s) alone or by combination of their Contribution(s)
|
||||
with the Work to which such Contribution(s) was submitted. If You
|
||||
institute patent litigation against any entity (including a
|
||||
cross-claim or counterclaim in a lawsuit) alleging that the Work
|
||||
or a Contribution incorporated within the Work constitutes direct
|
||||
or contributory patent infringement, then any patent licenses
|
||||
granted to You under this License for that Work shall terminate
|
||||
as of the date such litigation is filed.
|
||||
|
||||
4. Redistribution. You may reproduce and distribute copies of the
|
||||
Work or Derivative Works thereof in any medium, with or without
|
||||
modifications, and in Source or Object form, provided that You
|
||||
meet the following conditions:
|
||||
|
||||
(a) You must give any other recipients of the Work or
|
||||
Derivative Works a copy of this License; and
|
||||
|
||||
(b) You must cause any modified files to carry prominent notices
|
||||
stating that You changed the files; and
|
||||
|
||||
(c) You must retain, in the Source form of any Derivative Works
|
||||
that You distribute, all copyright, patent, trademark, and
|
||||
attribution notices from the Source form of the Work,
|
||||
excluding those notices that do not pertain to any part of
|
||||
the Derivative Works; and
|
||||
|
||||
(d) If the Work includes a "NOTICE" text file as part of its
|
||||
distribution, then any Derivative Works that You distribute must
|
||||
include a readable copy of the attribution notices contained
|
||||
within such NOTICE file, excluding those notices that do not
|
||||
pertain to any part of the Derivative Works, in at least one
|
||||
of the following places: within a NOTICE text file distributed
|
||||
as part of the Derivative Works; within the Source form or
|
||||
documentation, if provided along with the Derivative Works; or,
|
||||
within a display generated by the Derivative Works, if and
|
||||
wherever such third-party notices normally appear. The contents
|
||||
of the NOTICE file are for informational purposes only and
|
||||
do not modify the License. You may add Your own attribution
|
||||
notices within Derivative Works that You distribute, alongside
|
||||
or as an addendum to the NOTICE text from the Work, provided
|
||||
that such additional attribution notices cannot be construed
|
||||
as modifying the License.
|
||||
|
||||
You may add Your own copyright statement to Your modifications and
|
||||
may provide additional or different license terms and conditions
|
||||
for use, reproduction, or distribution of Your modifications, or
|
||||
for any such Derivative Works as a whole, provided Your use,
|
||||
reproduction, and distribution of the Work otherwise complies with
|
||||
the conditions stated in this License.
|
||||
|
||||
5. Submission of Contributions. Unless You explicitly state otherwise,
|
||||
any Contribution intentionally submitted for inclusion in the Work
|
||||
by You to the Licensor shall be under the terms and conditions of
|
||||
this License, without any additional terms or conditions.
|
||||
Notwithstanding the above, nothing herein shall supersede or modify
|
||||
the terms of any separate license agreement you may have executed
|
||||
with Licensor regarding such Contributions.
|
||||
|
||||
6. Trademarks. This License does not grant permission to use the trade
|
||||
names, trademarks, service marks, or product names of the Licensor,
|
||||
except as required for reasonable and customary use in describing the
|
||||
origin of the Work and reproducing the content of the NOTICE file.
|
||||
|
||||
7. Disclaimer of Warranty. Unless required by applicable law or
|
||||
agreed to in writing, Licensor provides the Work (and each
|
||||
Contributor provides its Contributions) on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
|
||||
implied, including, without limitation, any warranties or conditions
|
||||
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
|
||||
PARTICULAR PURPOSE. You are solely responsible for determining the
|
||||
appropriateness of using or redistributing the Work and assume any
|
||||
risks associated with Your exercise of permissions under this License.
|
||||
|
||||
8. Limitation of Liability. In no event and under no legal theory,
|
||||
whether in tort (including negligence), contract, or otherwise,
|
||||
unless required by applicable law (such as deliberate and grossly
|
||||
negligent acts) or agreed to in writing, shall any Contributor be
|
||||
liable to You for damages, including any direct, indirect, special,
|
||||
incidental, or consequential damages of any character arising as a
|
||||
result of this License or out of the use or inability to use the
|
||||
Work (including but not limited to damages for loss of goodwill,
|
||||
work stoppage, computer failure or malfunction, or any and all
|
||||
other commercial damages or losses), even if such Contributor
|
||||
has been advised of the possibility of such damages.
|
||||
|
||||
9. Accepting Warranty or Additional Liability. While redistributing
|
||||
the Work or Derivative Works thereof, You may choose to offer,
|
||||
and charge a fee for, acceptance of support, warranty, indemnity,
|
||||
or other liability obligations and/or rights consistent with this
|
||||
License. However, in accepting such obligations, You may act only
|
||||
on Your own behalf and on Your sole responsibility, not on behalf
|
||||
of any other Contributor, and only if You agree to indemnify,
|
||||
defend, and hold each Contributor harmless for any liability
|
||||
incurred by, or claims asserted against, such Contributor by reason
|
||||
of your accepting any such warranty or additional liability.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
APPENDIX: How to apply the Apache License to your work.
|
||||
|
||||
To apply the Apache License to your work, attach the following
|
||||
boilerplate notice, with the fields enclosed by brackets "{}"
|
||||
replaced with your own identifying information. (Don't include
|
||||
the brackets!) The text should be enclosed in the appropriate
|
||||
comment syntax for the file format. We also recommend that a
|
||||
file or class name and description of purpose be included on the
|
||||
same "printed page" as the copyright notice for easier
|
||||
identification within third-party archives.
|
||||
|
||||
Copyright {yyyy} {name of copyright owner}
|
||||
|
||||
Licensed under the Apache License, Version 2.0 (the "License");
|
||||
you may not use this file except in compliance with the License.
|
||||
You may obtain a copy of the License at
|
||||
|
||||
http://www.apache.org/licenses/LICENSE-2.0
|
||||
|
||||
Unless required by applicable law or agreed to in writing, software
|
||||
distributed under the License is distributed on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
See the License for the specific language governing permissions and
|
||||
limitations under the License.
|
||||
372
src/vendor/github.com/casbin/casbin/README.md
generated
vendored
Normal file
372
src/vendor/github.com/casbin/casbin/README.md
generated
vendored
Normal file
@ -0,0 +1,372 @@
|
||||
Casbin
|
||||
====
|
||||
|
||||
[](https://goreportcard.com/report/github.com/casbin/casbin)
|
||||
[](https://travis-ci.org/casbin/casbin)
|
||||
[](https://coveralls.io/github/casbin/casbin?branch=master)
|
||||
[](https://godoc.org/github.com/casbin/casbin)
|
||||
[](https://github.com/casbin/casbin/releases/latest)
|
||||
[](https://gitter.im/casbin/lobby)
|
||||
[](http://www.patreon.com/yangluo)
|
||||
[](https://sourcegraph.com/github.com/casbin/casbin?badge)
|
||||
|
||||
**News**: still worry about how to write the correct Casbin policy? ``Casbin online editor`` is coming to help! Try it at: http://casbin.org/editor/
|
||||
|
||||

|
||||
|
||||
Casbin is a powerful and efficient open-source access control library for Golang projects. It provides support for enforcing authorization based on various [access control models](https://en.wikipedia.org/wiki/Computer_security_model).
|
||||
|
||||
## All the languages supported by Casbin:
|
||||
|
||||
[](https://github.com/casbin/casbin) | [](https://github.com/casbin/jcasbin) | [](https://github.com/casbin/node-casbin) | [](https://github.com/php-casbin/php-casbin)
|
||||
----|----|----|----
|
||||
[Casbin](https://github.com/casbin/casbin) | [jCasbin](https://github.com/casbin/jcasbin) | [node-Casbin](https://github.com/casbin/node-casbin) | [PHP-Casbin](https://github.com/php-casbin/php-casbin)
|
||||
production-ready | production-ready | production-ready | production-ready
|
||||
|
||||
## Table of contents
|
||||
|
||||
- [Supported models](#supported-models)
|
||||
- [How it works?](#how-it-works)
|
||||
- [Features](#features)
|
||||
- [Installation](#installation)
|
||||
- [Documentation](#documentation)
|
||||
- [Online editor](#online-editor)
|
||||
- [Tutorials](#tutorials)
|
||||
- [Get started](#get-started)
|
||||
- [Policy management](#policy-management)
|
||||
- [Policy persistence](#policy-persistence)
|
||||
- [Policy consistence between multiple nodes](#policy-consistence-between-multiple-nodes)
|
||||
- [Role manager](#role-manager)
|
||||
- [Multi-threading](#multi-threading)
|
||||
- [Benchmarks](#benchmarks)
|
||||
- [Examples](#examples)
|
||||
- [How to use Casbin as a service?](#how-to-use-casbin-as-a-service)
|
||||
- [Our adopters](#our-adopters)
|
||||
|
||||
## Supported models
|
||||
|
||||
1. [**ACL (Access Control List)**](https://en.wikipedia.org/wiki/Access_control_list)
|
||||
2. **ACL with [superuser](https://en.wikipedia.org/wiki/Superuser)**
|
||||
3. **ACL without users**: especially useful for systems that don't have authentication or user log-ins.
|
||||
3. **ACL without resources**: some scenarios may target for a type of resources instead of an individual resource by using permissions like ``write-article``, ``read-log``. It doesn't control the access to a specific article or log.
|
||||
4. **[RBAC (Role-Based Access Control)](https://en.wikipedia.org/wiki/Role-based_access_control)**
|
||||
5. **RBAC with resource roles**: both users and resources can have roles (or groups) at the same time.
|
||||
6. **RBAC with domains/tenants**: users can have different role sets for different domains/tenants.
|
||||
7. **[ABAC (Attribute-Based Access Control)](https://en.wikipedia.org/wiki/Attribute-Based_Access_Control)**: syntax sugar like ``resource.Owner`` can be used to get the attribute for a resource.
|
||||
8. **[RESTful](https://en.wikipedia.org/wiki/Representational_state_transfer)**: supports paths like ``/res/*``, ``/res/:id`` and HTTP methods like ``GET``, ``POST``, ``PUT``, ``DELETE``.
|
||||
9. **Deny-override**: both allow and deny authorizations are supported, deny overrides the allow.
|
||||
10. **Priority**: the policy rules can be prioritized like firewall rules.
|
||||
|
||||
## How it works?
|
||||
|
||||
In Casbin, an access control model is abstracted into a CONF file based on the **PERM metamodel (Policy, Effect, Request, Matchers)**. So switching or upgrading the authorization mechanism for a project is just as simple as modifying a configuration. You can customize your own access control model by combining the available models. For example, you can get RBAC roles and ABAC attributes together inside one model and share one set of policy rules.
|
||||
|
||||
The most basic and simplest model in Casbin is ACL. ACL's model CONF is:
|
||||
|
||||
```ini
|
||||
# Request definition
|
||||
[request_definition]
|
||||
r = sub, obj, act
|
||||
|
||||
# Policy definition
|
||||
[policy_definition]
|
||||
p = sub, obj, act
|
||||
|
||||
# Policy effect
|
||||
[policy_effect]
|
||||
e = some(where (p.eft == allow))
|
||||
|
||||
# Matchers
|
||||
[matchers]
|
||||
m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
|
||||
|
||||
```
|
||||
|
||||
An example policy for ACL model is like:
|
||||
|
||||
```
|
||||
p, alice, data1, read
|
||||
p, bob, data2, write
|
||||
```
|
||||
|
||||
It means:
|
||||
|
||||
- alice can read data1
|
||||
- bob can write data2
|
||||
|
||||
We also support multi-line mode by appending '\\' in the end:
|
||||
|
||||
```ini
|
||||
# Matchers
|
||||
[matchers]
|
||||
m = r.sub == p.sub && r.obj == p.obj \
|
||||
&& r.act == p.act
|
||||
```
|
||||
|
||||
Further more, if you are using ABAC, you can try operator `in` like following in Casbin **golang** edition (jCasbin and Node-Casbin are not supported yet):
|
||||
|
||||
```ini
|
||||
# Matchers
|
||||
[matchers]
|
||||
m = r.obj == p.obj && r.act == p.act || r.obj in ('data2', 'data3')
|
||||
```
|
||||
|
||||
But you **SHOULD** make sure that the length of the array is **MORE** than **1**, otherwise there will cause it to panic.
|
||||
|
||||
For more operators, you may take a look at [govaluate](https://github.com/Knetic/govaluate)
|
||||
|
||||
## Features
|
||||
|
||||
What Casbin does:
|
||||
|
||||
1. enforce the policy in the classic ``{subject, object, action}`` form or a customized form as you defined, both allow and deny authorizations are supported.
|
||||
2. handle the storage of the access control model and its policy.
|
||||
3. manage the role-user mappings and role-role mappings (aka role hierarchy in RBAC).
|
||||
4. support built-in superuser like ``root`` or ``administrator``. A superuser can do anything without explict permissions.
|
||||
5. multiple built-in operators to support the rule matching. For example, ``keyMatch`` can map a resource key ``/foo/bar`` to the pattern ``/foo*``.
|
||||
|
||||
What Casbin does NOT do:
|
||||
|
||||
1. authentication (aka verify ``username`` and ``password`` when a user logs in)
|
||||
2. manage the list of users or roles. I believe it's more convenient for the project itself to manage these entities. Users usually have their passwords, and Casbin is not designed as a password container. However, Casbin stores the user-role mapping for the RBAC scenario.
|
||||
|
||||
## Installation
|
||||
|
||||
```
|
||||
go get github.com/casbin/casbin
|
||||
```
|
||||
|
||||
## Documentation
|
||||
|
||||
https://casbin.org/docs/en/overview
|
||||
|
||||
## Online editor
|
||||
|
||||
You can also use the online editor (http://casbin.org/editor/) to write your Casbin model and policy in your web browser. It provides functionality such as ``syntax highlighting`` and ``code completion``, just like an IDE for a programming language.
|
||||
|
||||
## Tutorials
|
||||
|
||||
https://casbin.org/docs/en/tutorials
|
||||
|
||||
## Get started
|
||||
|
||||
1. New a Casbin enforcer with a model file and a policy file:
|
||||
|
||||
```go
|
||||
e := casbin.NewEnforcer("path/to/model.conf", "path/to/policy.csv")
|
||||
```
|
||||
|
||||
Note: you can also initialize an enforcer with policy in DB instead of file, see [Persistence](#persistence) section for details.
|
||||
|
||||
2. Add an enforcement hook into your code right before the access happens:
|
||||
|
||||
```go
|
||||
sub := "alice" // the user that wants to access a resource.
|
||||
obj := "data1" // the resource that is going to be accessed.
|
||||
act := "read" // the operation that the user performs on the resource.
|
||||
|
||||
if e.Enforce(sub, obj, act) == true {
|
||||
// permit alice to read data1
|
||||
} else {
|
||||
// deny the request, show an error
|
||||
}
|
||||
```
|
||||
|
||||
3. Besides the static policy file, Casbin also provides API for permission management at run-time. For example, You can get all the roles assigned to a user as below:
|
||||
|
||||
```go
|
||||
roles := e.GetRoles("alice")
|
||||
```
|
||||
|
||||
See [Policy management APIs](#policy-management) for more usage.
|
||||
|
||||
4. Please refer to the ``_test.go`` files for more usage.
|
||||
|
||||
## Policy management
|
||||
|
||||
Casbin provides two sets of APIs to manage permissions:
|
||||
|
||||
- [Management API](https://github.com/casbin/casbin/blob/master/management_api.go): the primitive API that provides full support for Casbin policy management. See [here](https://github.com/casbin/casbin/blob/master/management_api_test.go) for examples.
|
||||
- [RBAC API](https://github.com/casbin/casbin/blob/master/rbac_api.go): a more friendly API for RBAC. This API is a subset of Management API. The RBAC users could use this API to simplify the code. See [here](https://github.com/casbin/casbin/blob/master/rbac_api_test.go) for examples.
|
||||
|
||||
We also provide a web-based UI for model management and policy management:
|
||||
|
||||
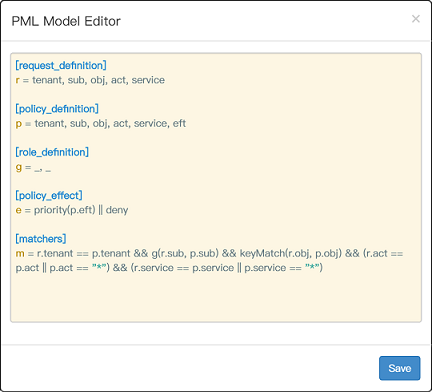
|
||||
|
||||
|
||||
|
||||
## Policy persistence
|
||||
|
||||
In Casbin, the policy storage is implemented as an adapter (aka middleware for Casbin). To keep light-weight, we don't put adapter code in the main library (except the default file adapter). A complete list of Casbin adapters is provided as below. Any 3rd-party contribution on a new adapter is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Adapter | Type | Author | Description
|
||||
----|------|----|----
|
||||
[File Adapter (built-in)](https://casbin.org/docs/en/policy-storage#file-adapter-built-in) | File | Casbin | Persistence for [.CSV (Comma-Separated Values)](https://en.wikipedia.org/wiki/Comma-separated_values) files
|
||||
[Filtered File Adapter (built-in)](https://github.com/casbin/casbin#policy-enforcement-at-scale) | File | [@faceless-saint](https://github.com/faceless-saint) | Persistence for [.CSV (Comma-Separated Values)](https://en.wikipedia.org/wiki/Comma-separated_values) files with policy subset loading support
|
||||
[Xorm Adapter](https://github.com/casbin/xorm-adapter) | ORM | Casbin | MySQL, PostgreSQL, TiDB, SQLite, SQL Server, Oracle are supported by [Xorm](https://github.com/go-xorm/xorm/)
|
||||
[Gorm Adapter](https://github.com/casbin/gorm-adapter) | ORM | Casbin | MySQL, PostgreSQL, Sqlite3, SQL Server are supported by [Gorm](https://github.com/jinzhu/gorm/)
|
||||
[Beego ORM Adapter](https://github.com/casbin/beego-orm-adapter) | ORM | Casbin | MySQL, PostgreSQL, Sqlite3 are supported by [Beego ORM](https://beego.me/docs/mvc/model/overview.md)
|
||||
[MongoDB Adapter](https://github.com/casbin/mongodb-adapter) | NoSQL | Casbin | Persistence for [MongoDB](https://www.mongodb.com)
|
||||
[Cassandra Adapter](https://github.com/casbin/cassandra-adapter) | NoSQL | Casbin | Persistence for [Apache Cassandra DB](http://cassandra.apache.org)
|
||||
[Consul Adapter](https://github.com/ankitm123/consul-adapter) | KV store | [@ankitm123](https://github.com/ankitm123) | Persistence for [HashiCorp Consul](https://www.consul.io/)
|
||||
[Redis Adapter](https://github.com/casbin/redis-adapter) | KV store | Casbin | Persistence for [Redis](https://redis.io/)
|
||||
[Protobuf Adapter](https://github.com/casbin/protobuf-adapter) | Stream | Casbin | Persistence for [Google Protocol Buffers](https://developers.google.com/protocol-buffers/)
|
||||
[JSON Adapter](https://github.com/casbin/json-adapter) | String | Casbin | Persistence for [JSON](https://www.json.org/)
|
||||
[String Adapter](https://github.com/qiangmzsx/string-adapter) | String | [@qiangmzsx](https://github.com/qiangmzsx) | Persistence for String
|
||||
[RQLite Adapter](https://github.com/edomosystems/rqlite-adapter) | SQL | [EDOMO Systems](https://github.com/edomosystems) | Persistence for [RQLite](https://github.com/rqlite/rqlite/)
|
||||
[PostgreSQL Adapter](https://github.com/going/casbin-postgres-adapter) | SQL | [Going](https://github.com/going) | Persistence for [PostgreSQL](https://www.postgresql.org/)
|
||||
[RethinkDB Adapter](https://github.com/adityapandey9/rethinkdb-adapter) | NoSQL | [@adityapandey9](https://github.com/adityapandey9) | Persistence for [RethinkDB](https://rethinkdb.com/)
|
||||
[DynamoDB Adapter](https://github.com/HOOQTV/dynacasbin) | NoSQL | [HOOQ](https://github.com/HOOQTV) | Persistence for [Amazon DynamoDB](https://aws.amazon.com/dynamodb/)
|
||||
[Minio/AWS S3 Adapter](https://github.com/Soluto/casbin-minio-adapter) | Object storage | [Soluto](https://github.com/Soluto) | Persistence for [Minio](https://github.com/minio/minio) and [Amazon S3](https://aws.amazon.com/s3/)
|
||||
[Bolt Adapter](https://github.com/wirepair/bolt-adapter) | KV store | [@wirepair](https://github.com/wirepair) | Persistence for [Bolt](https://github.com/boltdb/bolt)
|
||||
|
||||
For details of adapters, please refer to the documentation: https://casbin.org/docs/en/policy-storage
|
||||
|
||||
## Policy enforcement at scale
|
||||
|
||||
Some adapters support filtered policy management. This means that the policy loaded by Casbin is a subset of the policy in storage based on a given filter. This allows for efficient policy enforcement in large, multi-tenant environments when parsing the entire policy becomes a performance bottleneck.
|
||||
|
||||
To use filtered policies with a supported adapter, simply call the `LoadFilteredPolicy` method. The valid format for the filter parameter depends on the adapter used. To prevent accidental data loss, the `SavePolicy` method is disabled when a filtered policy is loaded.
|
||||
|
||||
For example, the following code snippet uses the built-in filtered file adapter and the RBAC model with domains. In this case, the filter limits the policy to a single domain. Any policy lines for domains other than `"domain1"` are omitted from the loaded policy:
|
||||
|
||||
```go
|
||||
import (
|
||||
"github.com/casbin/casbin"
|
||||
)
|
||||
|
||||
enforcer := casbin.NewEnforcer()
|
||||
|
||||
adapter := fileadapter.NewFilteredAdapter("examples/rbac_with_domains_policy.csv")
|
||||
enforcer.InitWithAdapter("examples/rbac_with_domains_model.conf", adapter)
|
||||
|
||||
filter := &fileadapter.Filter{
|
||||
P: []string{"", "domain1"},
|
||||
G: []string{"", "", "domain1"},
|
||||
}
|
||||
enforcer.LoadFilteredPolicy(filter)
|
||||
|
||||
// The loaded policy now only contains the entries pertaining to "domain1".
|
||||
```
|
||||
|
||||
## Policy consistence between multiple nodes
|
||||
|
||||
We support to use distributed messaging systems like [etcd](https://github.com/coreos/etcd) to keep consistence between multiple Casbin enforcer instances. So our users can concurrently use multiple Casbin enforcers to handle large number of permission checking requests.
|
||||
|
||||
Similar to policy storage adapters, we don't put watcher code in the main library. Any support for a new messaging system should be implemented as a watcher. A complete list of Casbin watchers is provided as below. Any 3rd-party contribution on a new watcher is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Watcher | Type | Author | Description
|
||||
----|------|----|----
|
||||
[Etcd Watcher](https://github.com/casbin/etcd-watcher) | KV store | Casbin | Watcher for [etcd](https://github.com/coreos/etcd)
|
||||
[NATS Watcher](https://github.com/Soluto/casbin-nats-watcher) | Messaging system | [Soluto](https://github.com/Soluto) | Watcher for [NATS](https://nats.io/)
|
||||
[ZooKeeper Watcher](https://github.com/grepsr/casbin-zk-watcher) | KV store | [Grepsr](https://github.com/grepsr) | Watcher for [Apache ZooKeeper](https://zookeeper.apache.org/)
|
||||
[Redis Watcher](https://github.com/billcobbler/casbin-redis-watcher) | KV store | [@billcobbler](https://github.com/billcobbler) | Watcher for [Redis](http://redis.io/)
|
||||
|
||||
## Role manager
|
||||
|
||||
The role manager is used to manage the RBAC role hierarchy (user-role mapping) in Casbin. A role manager can retrieve the role data from Casbin policy rules or external sources such as LDAP, Okta, Auth0, Azure AD, etc. We support different implementations of a role manager. To keep light-weight, we don't put role manager code in the main library (except the default role manager). A complete list of Casbin role managers is provided as below. Any 3rd-party contribution on a new role manager is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Role manager | Author | Description
|
||||
----|----|----
|
||||
[Default Role Manager (built-in)](https://github.com/casbin/casbin/blob/master/rbac/default-role-manager/role_manager.go) | Casbin | Supports role hierarchy stored in Casbin policy
|
||||
[Session Role Manager](https://github.com/casbin/session-role-manager) | [EDOMO Systems](https://github.com/edomosystems) | Supports role hierarchy stored in Casbin policy, with time-range-based sessions
|
||||
[Okta Role Manager](https://github.com/casbin/okta-role-manager) | Casbin | Supports role hierarchy stored in [Okta](https://www.okta.com/)
|
||||
[Auth0 Role Manager](https://github.com/casbin/auth0-role-manager) | Casbin | Supports role hierarchy stored in [Auth0](https://auth0.com/)'s [Authorization Extension](https://auth0.com/docs/extensions/authorization-extension/v2)
|
||||
|
||||
For developers: all role managers must implement the [RoleManager](https://github.com/casbin/casbin/blob/master/rbac/role_manager.go) interface. [Session Role Manager](https://github.com/casbin/session-role-manager) can be used as a reference implementation.
|
||||
|
||||
## Multi-threading
|
||||
|
||||
If you use Casbin in a multi-threading manner, you can use the synchronized wrapper of the Casbin enforcer: https://github.com/casbin/casbin/blob/master/enforcer_synced.go.
|
||||
|
||||
It also supports the ``AutoLoad`` feature, which means the Casbin enforcer will automatically load the latest policy rules from DB if it has changed. Call ``StartAutoLoadPolicy()`` to start automatically loading policy periodically and call ``StopAutoLoadPolicy()`` to stop it.
|
||||
|
||||
## Benchmarks
|
||||
|
||||
The overhead of policy enforcement is benchmarked in [model_b_test.go](https://github.com/casbin/casbin/blob/master/model_b_test.go). The testbed is:
|
||||
|
||||
```
|
||||
Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz, 2601 Mhz, 4 Core(s), 8 Logical Processor(s)
|
||||
```
|
||||
|
||||
The benchmarking result of ``go test -bench=. -benchmem`` is as follows (op = an ``Enforce()`` call, ms = millisecond, KB = kilo bytes):
|
||||
|
||||
Test case | Size | Time overhead | Memory overhead
|
||||
----|------|------|----
|
||||
ACL | 2 rules (2 users) | 0.015493 ms/op | 5.649 KB
|
||||
RBAC | 5 rules (2 users, 1 role) | 0.021738 ms/op | 7.522 KB
|
||||
RBAC (small) | 1100 rules (1000 users, 100 roles) | 0.164309 ms/op | 80.620 KB
|
||||
RBAC (medium) | 11000 rules (10000 users, 1000 roles) | 2.258262 ms/op | 765.152 KB
|
||||
RBAC (large) | 110000 rules (100000 users, 10000 roles) | 23.916776 ms/op | 7.606 MB
|
||||
RBAC with resource roles | 6 rules (2 users, 2 roles) | 0.021146 ms/op | 7.906 KB
|
||||
RBAC with domains/tenants | 6 rules (2 users, 1 role, 2 domains) | 0.032696 ms/op | 10.755 KB
|
||||
ABAC | 0 rule (0 user) | 0.007510 ms/op | 2.328 KB
|
||||
RESTful | 5 rules (3 users) | 0.045398 ms/op | 91.774 KB
|
||||
Deny-override | 6 rules (2 users, 1 role) | 0.023281 ms/op | 8.370 KB
|
||||
Priority | 9 rules (2 users, 2 roles) | 0.016389 ms/op | 5.313 KB
|
||||
|
||||
## Examples
|
||||
|
||||
Model | Model file | Policy file
|
||||
----|------|----
|
||||
ACL | [basic_model.conf](https://github.com/casbin/casbin/blob/master/examples/basic_model.conf) | [basic_policy.csv](https://github.com/casbin/casbin/blob/master/examples/basic_policy.csv)
|
||||
ACL with superuser | [basic_model_with_root.conf](https://github.com/casbin/casbin/blob/master/examples/basic_with_root_model.conf) | [basic_policy.csv](https://github.com/casbin/casbin/blob/master/examples/basic_policy.csv)
|
||||
ACL without users | [basic_model_without_users.conf](https://github.com/casbin/casbin/blob/master/examples/basic_without_users_model.conf) | [basic_policy_without_users.csv](https://github.com/casbin/casbin/blob/master/examples/basic_without_users_policy.csv)
|
||||
ACL without resources | [basic_model_without_resources.conf](https://github.com/casbin/casbin/blob/master/examples/basic_without_resources_model.conf) | [basic_policy_without_resources.csv](https://github.com/casbin/casbin/blob/master/examples/basic_without_resources_policy.csv)
|
||||
RBAC | [rbac_model.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_model.conf) | [rbac_policy.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_policy.csv)
|
||||
RBAC with resource roles | [rbac_model_with_resource_roles.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_resource_roles_model.conf) | [rbac_policy_with_resource_roles.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_resource_roles_policy.csv)
|
||||
RBAC with domains/tenants | [rbac_model_with_domains.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_domains_model.conf) | [rbac_policy_with_domains.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_domains_policy.csv)
|
||||
ABAC | [abac_model.conf](https://github.com/casbin/casbin/blob/master/examples/abac_model.conf) | N/A
|
||||
RESTful | [keymatch_model.conf](https://github.com/casbin/casbin/blob/master/examples/keymatch_model.conf) | [keymatch_policy.csv](https://github.com/casbin/casbin/blob/master/examples/keymatch_policy.csv)
|
||||
Deny-override | [rbac_model_with_deny.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_deny_model.conf) | [rbac_policy_with_deny.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_deny_policy.csv)
|
||||
Priority | [priority_model.conf](https://github.com/casbin/casbin/blob/master/examples/priority_model.conf) | [priority_policy.csv](https://github.com/casbin/casbin/blob/master/examples/priority_policy.csv)
|
||||
|
||||
## How to use Casbin as a service?
|
||||
|
||||
- [Casbin Server](https://github.com/casbin/casbin-server): The official ``Casbin as a Service`` solution based on [gRPC](https://grpc.io/), both Management API and RBAC API are provided.
|
||||
- [Go-Simple-API-Gateway](https://github.com/Soontao/go-simple-api-gateway): A simple API gateway written by golang, supports for authentication and authorization.
|
||||
- [middleware-acl](https://github.com/luk4z7/middleware-acl): RESTful access control middleware based on Casbin.
|
||||
|
||||
## Our adopters
|
||||
|
||||
### Web frameworks
|
||||
|
||||
- [Beego](https://github.com/astaxie/beego): An open-source, high-performance web framework for Go, via built-in plugin: [plugins/authz](https://github.com/astaxie/beego/blob/master/plugins/authz)
|
||||
- [Caddy](https://github.com/mholt/caddy): Fast, cross-platform HTTP/2 web server with automatic HTTPS, via plugin: [caddy-authz](https://github.com/casbin/caddy-authz)
|
||||
- [Gin](https://github.com/gin-gonic/gin): A HTTP web framework featuring a Martini-like API with much better performance, via plugin: [authz](https://github.com/gin-contrib/authz)
|
||||
- [Revel](https://github.com/revel/revel): A high productivity, full-stack web framework for the Go language, via plugin: [auth/casbin](https://github.com/revel/modules/tree/master/auth/casbin)
|
||||
- [Echo](https://github.com/labstack/echo): High performance, minimalist Go web framework, via plugin: [echo-authz](https://github.com/labstack/echo-contrib/tree/master/casbin) (thanks to [@xqbumu](https://github.com/xqbumu))
|
||||
- [Iris](https://github.com/kataras/iris): The fastest web framework for Go in (THIS) Earth. HTTP/2 Ready-To-GO, via plugin: [casbin](https://github.com/iris-contrib/middleware/tree/master/casbin) (thanks to [@hiveminded](https://github.com/hiveminded))
|
||||
- [Negroni](https://github.com/urfave/negroni): Idiomatic HTTP Middleware for Golang, via plugin: [negroni-authz](https://github.com/casbin/negroni-authz)
|
||||
- [Tango](https://github.com/lunny/tango): Micro & pluggable web framework for Go, via plugin: [authz](https://github.com/tango-contrib/authz)
|
||||
- [Chi](https://github.com/pressly/chi): A lightweight, idiomatic and composable router for building HTTP services, via plugin: [chi-authz](https://github.com/casbin/chi-authz)
|
||||
- [Macaron](https://github.com/go-macaron/macaron): A high productive and modular web framework in Go, via plugin: [authz](https://github.com/go-macaron/authz)
|
||||
- [DotWeb](https://github.com/devfeel/dotweb): Simple and easy go web micro framework, via plugin: [authz](https://github.com/devfeel/middleware/tree/master/authz)
|
||||
- [Baa](https://github.com/go-baa/baa): An express Go web framework with routing, middleware, dependency injection and http context, via plugin: [authz](https://github.com/baa-middleware/authz)
|
||||
|
||||
### Others
|
||||
|
||||
- [Intel RMD](https://github.com/intel/rmd): Intel's resource management daemon, via direct integration, see: [model](https://github.com/intel/rmd/blob/master/etc/rmd/acl/url/model.conf), [policy rules](https://github.com/intel/rmd/blob/master/etc/rmd/acl/url/policy.csv)
|
||||
- [VMware Dispatch](https://github.com/vmware/dispatch): A framework for deploying and managing serverless style applications, via direct integration, see: [model (in code)](https://github.com/vmware/dispatch/blob/master/pkg/identity-manager/handlers.go#L46-L55), [policy rules (in code)](https://github.com/vmware/dispatch/blob/master/pkg/identity-manager/handlers_test.go#L35-L45)
|
||||
- [Banzai Pipeline](https://github.com/banzaicloud/pipeline): [Banzai Cloud](https://github.com/banzaicloud)'s RESTful API to provision or reuse managed Kubernetes clusters in the cloud, via direct integration, see: [model (in code)](https://github.com/banzaicloud/pipeline/blob/master/auth/authz.go#L15-L30), [policy rules (in code)](https://github.com/banzaicloud/pipeline/blob/master/auth/authz.go#L84-L93)
|
||||
- [Docker](https://github.com/docker/docker): The world's leading software container platform, via plugin: [casbin-authz-plugin](https://github.com/casbin/casbin-authz-plugin) ([recommended by Docker](https://docs.docker.com/engine/extend/legacy_plugins/#authorization-plugins))
|
||||
- [Gobis](https://github.com/orange-cloudfoundry/gobis): [Orange](https://github.com/orange-cloudfoundry)'s lightweight API Gateway written in go, via plugin: [casbin](https://github.com/orange-cloudfoundry/gobis-middlewares/tree/master/casbin), see [model (in code)](https://github.com/orange-cloudfoundry/gobis-middlewares/blob/master/casbin/model.go#L52-L65), [policy rules (from request)](https://github.com/orange-cloudfoundry/gobis-middlewares/blob/master/casbin/adapter.go#L46-L64)
|
||||
- [Skydive](https://github.com/skydive-project/skydive): An open source real-time network topology and protocols analyzer, via direct integration, see: [model (in code)](https://github.com/skydive-project/skydive/blob/master/config/config.go#L136-L140), [policy rules](https://github.com/skydive-project/skydive/blob/master/rbac/policy.csv)
|
||||
- [Zenpress](https://github.com/insionng/zenpress): A CMS system written in Golang, via direct integration, see: [model](https://github.com/insionng/zenpress/blob/master/content/config/rbac_model.conf), [policy rules (in Gorm)](https://github.com/insionng/zenpress/blob/master/model/user.go#L53-L77)
|
||||
- [Argo CD](https://github.com/argoproj/argo-cd): GitOps continuous delivery for Kubernetes, via direct integration, see: [model](https://github.com/argoproj/argo-cd/blob/master/util/rbac/model.conf), [policy rules](https://github.com/argoproj/argo-cd/blob/master/util/rbac/builtin-policy.csv)
|
||||
- [Muxi Cloud](https://github.com/muxiyun/Mae): PaaS of Muxi Cloud, an easier way to manage Kubernetes cluster, via direct integration, see: [model](https://github.com/muxiyun/Mae/blob/master/conf/casbinmodel.conf), [policy rules (in code)](https://github.com/muxiyun/Mae/blob/master/pkg/casbin/initPolicy.go#L21-L95)
|
||||
- [EngineerCMS](https://github.com/3xxx/EngineerCMS): A CMS to manage knowledge for engineers, via direct integration, see: [model](https://github.com/3xxx/EngineerCMS/blob/master/conf/rbac_model.conf), [policy rules (in SQLite)](https://github.com/3xxx/EngineerCMS/blob/master/database/engineer.db)
|
||||
- [Cyber Auth API](https://github.com/CyberlifeCN/cyber-auth-api): A Golang authentication API project, via direct integration, see: [model](https://github.com/CyberlifeCN/cyber-auth-api/blob/master/conf/authz_model.conf), [policy rules](https://github.com/CyberlifeCN/cyber-auth-api/blob/master/conf/authz_policy.csv)
|
||||
- [IRIS Community](https://github.com/irisnet/iris-community): Website for IRIS Community Activities, via direct integration, see: [model](https://github.com/irisnet/iris-community/blob/master/authz/authz_model.conf), [policy rules](https://github.com/irisnet/iris-community/blob/master/authz/authz_policy.csv)
|
||||
- [Metadata DB](https://github.com/Bnei-Baruch/mdb): BB archive metadata database, via direct integration, see: [model](https://github.com/Bnei-Baruch/mdb/blob/master/data/permissions_model.conf), [policy rules](https://github.com/Bnei-Baruch/mdb/blob/master/data/permissions_policy.csv)
|
||||
|
||||
## License
|
||||
|
||||
This project is licensed under the [Apache 2.0 license](LICENSE).
|
||||
|
||||
## Contact
|
||||
|
||||
If you have any issues or feature requests, please contact us. PR is welcomed.
|
||||
- https://github.com/casbin/casbin/issues
|
||||
- hsluoyz@gmail.com
|
||||
- Tencent QQ group: [546057381](//shang.qq.com/wpa/qunwpa?idkey=8ac8b91fc97ace3d383d0035f7aa06f7d670fd8e8d4837347354a31c18fac885)
|
||||
BIN
src/vendor/github.com/casbin/casbin/casbin-logo.png
generated
vendored
Normal file
BIN
src/vendor/github.com/casbin/casbin/casbin-logo.png
generated
vendored
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 34 KiB |
266
src/vendor/github.com/casbin/casbin/config/config.go
generated
vendored
Normal file
266
src/vendor/github.com/casbin/casbin/config/config.go
generated
vendored
Normal file
@ -0,0 +1,266 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package config
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"bytes"
|
||||
"errors"
|
||||
"fmt"
|
||||
"io"
|
||||
"os"
|
||||
"strconv"
|
||||
"strings"
|
||||
"sync"
|
||||
)
|
||||
|
||||
var (
|
||||
// DEFAULT_SECTION specifies the name of a section if no name provided
|
||||
DEFAULT_SECTION = "default"
|
||||
// DEFAULT_COMMENT defines what character(s) indicate a comment `#`
|
||||
DEFAULT_COMMENT = []byte{'#'}
|
||||
// DEFAULT_COMMENT_SEM defines what alternate character(s) indicate a comment `;`
|
||||
DEFAULT_COMMENT_SEM = []byte{';'}
|
||||
// DEFAULT_MULTI_LINE_SEPARATOR defines what character indicates a multi-line content
|
||||
DEFAULT_MULTI_LINE_SEPARATOR = []byte{'\\'}
|
||||
)
|
||||
|
||||
// ConfigInterface defines the behavior of a Config implemenation
|
||||
type ConfigInterface interface {
|
||||
String(key string) string
|
||||
Strings(key string) []string
|
||||
Bool(key string) (bool, error)
|
||||
Int(key string) (int, error)
|
||||
Int64(key string) (int64, error)
|
||||
Float64(key string) (float64, error)
|
||||
Set(key string, value string) error
|
||||
}
|
||||
|
||||
// Config represents an implementation of the ConfigInterface
|
||||
type Config struct {
|
||||
// map is not safe.
|
||||
sync.RWMutex
|
||||
// Section:key=value
|
||||
data map[string]map[string]string
|
||||
}
|
||||
|
||||
// NewConfig create an empty configuration representation from file.
|
||||
func NewConfig(confName string) (ConfigInterface, error) {
|
||||
c := &Config{
|
||||
data: make(map[string]map[string]string),
|
||||
}
|
||||
err := c.parse(confName)
|
||||
return c, err
|
||||
}
|
||||
|
||||
// NewConfigFromText create an empty configuration representation from text.
|
||||
func NewConfigFromText(text string) (ConfigInterface, error) {
|
||||
c := &Config{
|
||||
data: make(map[string]map[string]string),
|
||||
}
|
||||
err := c.parseBuffer(bufio.NewReader(strings.NewReader(text)))
|
||||
return c, err
|
||||
}
|
||||
|
||||
// AddConfig adds a new section->key:value to the configuration.
|
||||
func (c *Config) AddConfig(section string, option string, value string) bool {
|
||||
if section == "" {
|
||||
section = DEFAULT_SECTION
|
||||
}
|
||||
|
||||
if _, ok := c.data[section]; !ok {
|
||||
c.data[section] = make(map[string]string)
|
||||
}
|
||||
|
||||
_, ok := c.data[section][option]
|
||||
c.data[section][option] = value
|
||||
|
||||
return !ok
|
||||
}
|
||||
|
||||
func (c *Config) parse(fname string) (err error) {
|
||||
c.Lock()
|
||||
f, err := os.Open(fname)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer c.Unlock()
|
||||
defer f.Close()
|
||||
|
||||
buf := bufio.NewReader(f)
|
||||
return c.parseBuffer(buf)
|
||||
}
|
||||
|
||||
func (c *Config) parseBuffer(buf *bufio.Reader) error {
|
||||
var section string
|
||||
var lineNum int
|
||||
var buffer bytes.Buffer
|
||||
var canWrite bool
|
||||
for {
|
||||
if canWrite {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
} else {
|
||||
canWrite = false
|
||||
}
|
||||
}
|
||||
lineNum++
|
||||
line, _, err := buf.ReadLine()
|
||||
if err == io.EOF {
|
||||
// force write when buffer is not flushed yet
|
||||
if buffer.Len() > 0 {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
}
|
||||
}
|
||||
break
|
||||
} else if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
line = bytes.TrimSpace(line)
|
||||
switch {
|
||||
case bytes.Equal(line, []byte{}), bytes.HasPrefix(line, DEFAULT_COMMENT_SEM),
|
||||
bytes.HasPrefix(line, DEFAULT_COMMENT):
|
||||
canWrite = true
|
||||
continue
|
||||
case bytes.HasPrefix(line, []byte{'['}) && bytes.HasSuffix(line, []byte{']'}):
|
||||
// force write when buffer is not flushed yet
|
||||
if buffer.Len() > 0 {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
}
|
||||
canWrite = false
|
||||
}
|
||||
section = string(line[1 : len(line)-1])
|
||||
default:
|
||||
var p []byte
|
||||
if bytes.HasSuffix(line, DEFAULT_MULTI_LINE_SEPARATOR) {
|
||||
p = bytes.TrimSpace(line[:len(line)-1])
|
||||
} else {
|
||||
p = line
|
||||
canWrite = true
|
||||
}
|
||||
|
||||
if _, err := buffer.Write(p); err != nil {
|
||||
return err
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
func (c *Config) write(section string, lineNum int, b *bytes.Buffer) error {
|
||||
if b.Len() <= 0 {
|
||||
return nil
|
||||
}
|
||||
|
||||
optionVal := bytes.SplitN(b.Bytes(), []byte{'='}, 2)
|
||||
if len(optionVal) != 2 {
|
||||
return fmt.Errorf("parse the content error : line %d , %s = ? ", lineNum, optionVal[0])
|
||||
}
|
||||
option := bytes.TrimSpace(optionVal[0])
|
||||
value := bytes.TrimSpace(optionVal[1])
|
||||
c.AddConfig(section, string(option), string(value))
|
||||
|
||||
// flush buffer after adding
|
||||
b.Reset()
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
// Bool lookups up the value using the provided key and converts the value to a bool
|
||||
func (c *Config) Bool(key string) (bool, error) {
|
||||
return strconv.ParseBool(c.get(key))
|
||||
}
|
||||
|
||||
// Int lookups up the value using the provided key and converts the value to a int
|
||||
func (c *Config) Int(key string) (int, error) {
|
||||
return strconv.Atoi(c.get(key))
|
||||
}
|
||||
|
||||
// Int64 lookups up the value using the provided key and converts the value to a int64
|
||||
func (c *Config) Int64(key string) (int64, error) {
|
||||
return strconv.ParseInt(c.get(key), 10, 64)
|
||||
}
|
||||
|
||||
// Float64 lookups up the value using the provided key and converts the value to a float64
|
||||
func (c *Config) Float64(key string) (float64, error) {
|
||||
return strconv.ParseFloat(c.get(key), 64)
|
||||
}
|
||||
|
||||
// String lookups up the value using the provided key and converts the value to a string
|
||||
func (c *Config) String(key string) string {
|
||||
return c.get(key)
|
||||
}
|
||||
|
||||
// Strings lookups up the value using the provided key and converts the value to an array of string
|
||||
// by splitting the string by comma
|
||||
func (c *Config) Strings(key string) []string {
|
||||
v := c.get(key)
|
||||
if v == "" {
|
||||
return nil
|
||||
}
|
||||
return strings.Split(v, ",")
|
||||
}
|
||||
|
||||
// Set sets the value for the specific key in the Config
|
||||
func (c *Config) Set(key string, value string) error {
|
||||
c.Lock()
|
||||
defer c.Unlock()
|
||||
if len(key) == 0 {
|
||||
return errors.New("key is empty")
|
||||
}
|
||||
|
||||
var (
|
||||
section string
|
||||
option string
|
||||
)
|
||||
|
||||
keys := strings.Split(strings.ToLower(key), "::")
|
||||
if len(keys) >= 2 {
|
||||
section = keys[0]
|
||||
option = keys[1]
|
||||
} else {
|
||||
option = keys[0]
|
||||
}
|
||||
|
||||
c.AddConfig(section, option, value)
|
||||
return nil
|
||||
}
|
||||
|
||||
// section.key or key
|
||||
func (c *Config) get(key string) string {
|
||||
var (
|
||||
section string
|
||||
option string
|
||||
)
|
||||
|
||||
keys := strings.Split(strings.ToLower(key), "::")
|
||||
if len(keys) >= 2 {
|
||||
section = keys[0]
|
||||
option = keys[1]
|
||||
} else {
|
||||
section = DEFAULT_SECTION
|
||||
option = keys[0]
|
||||
}
|
||||
|
||||
if value, ok := c.data[section][option]; ok {
|
||||
return value
|
||||
}
|
||||
|
||||
return ""
|
||||
}
|
||||
75
src/vendor/github.com/casbin/casbin/effect/default_effector.go
generated
vendored
Normal file
75
src/vendor/github.com/casbin/casbin/effect/default_effector.go
generated
vendored
Normal file
@ -0,0 +1,75 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package effect
|
||||
|
||||
import "github.com/pkg/errors"
|
||||
|
||||
// DefaultEffector is default effector for Casbin.
|
||||
type DefaultEffector struct {
|
||||
}
|
||||
|
||||
// NewDefaultEffector is the constructor for DefaultEffector.
|
||||
func NewDefaultEffector() *DefaultEffector {
|
||||
e := DefaultEffector{}
|
||||
return &e
|
||||
}
|
||||
|
||||
// MergeEffects merges all matching results collected by the enforcer into a single decision.
|
||||
func (e *DefaultEffector) MergeEffects(expr string, effects []Effect, results []float64) (bool, error) {
|
||||
result := false
|
||||
if expr == "some(where (p_eft == allow))" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "!some(where (p_eft == deny))" {
|
||||
result = true
|
||||
for _, eft := range effects {
|
||||
if eft == Deny {
|
||||
result = false
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "some(where (p_eft == allow)) && !some(where (p_eft == deny))" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
} else if eft == Deny {
|
||||
result = false
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "priority(p_eft) || deny" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft != Indeterminate {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
} else {
|
||||
result = false
|
||||
}
|
||||
break
|
||||
}
|
||||
}
|
||||
} else {
|
||||
return false, errors.New("unsupported effect")
|
||||
}
|
||||
|
||||
return result, nil
|
||||
}
|
||||
31
src/vendor/github.com/casbin/casbin/effect/effector.go
generated
vendored
Normal file
31
src/vendor/github.com/casbin/casbin/effect/effector.go
generated
vendored
Normal file
@ -0,0 +1,31 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package effect
|
||||
|
||||
// Effect is the result for a policy rule.
|
||||
type Effect int
|
||||
|
||||
// Values for policy effect.
|
||||
const (
|
||||
Allow Effect = iota
|
||||
Indeterminate
|
||||
Deny
|
||||
)
|
||||
|
||||
// Effector is the interface for Casbin effectors.
|
||||
type Effector interface {
|
||||
// MergeEffects merges all matching results collected by the enforcer into a single decision.
|
||||
MergeEffects(expr string, effects []Effect, results []float64) (bool, error)
|
||||
}
|
||||
428
src/vendor/github.com/casbin/casbin/enforcer.go
generated
vendored
Normal file
428
src/vendor/github.com/casbin/casbin/enforcer.go
generated
vendored
Normal file
@ -0,0 +1,428 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
|
||||
"github.com/Knetic/govaluate"
|
||||
"github.com/casbin/casbin/effect"
|
||||
"github.com/casbin/casbin/log"
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
"github.com/casbin/casbin/persist/file-adapter"
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/rbac/default-role-manager"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Enforcer is the main interface for authorization enforcement and policy management.
|
||||
type Enforcer struct {
|
||||
modelPath string
|
||||
model model.Model
|
||||
fm model.FunctionMap
|
||||
eft effect.Effector
|
||||
|
||||
adapter persist.Adapter
|
||||
watcher persist.Watcher
|
||||
rm rbac.RoleManager
|
||||
|
||||
enabled bool
|
||||
autoSave bool
|
||||
autoBuildRoleLinks bool
|
||||
}
|
||||
|
||||
// NewEnforcer creates an enforcer via file or DB.
|
||||
// File:
|
||||
// e := casbin.NewEnforcer("path/to/basic_model.conf", "path/to/basic_policy.csv")
|
||||
// MySQL DB:
|
||||
// a := mysqladapter.NewDBAdapter("mysql", "mysql_username:mysql_password@tcp(127.0.0.1:3306)/")
|
||||
// e := casbin.NewEnforcer("path/to/basic_model.conf", a)
|
||||
func NewEnforcer(params ...interface{}) *Enforcer {
|
||||
e := &Enforcer{}
|
||||
|
||||
parsedParamLen := 0
|
||||
if len(params) >= 1 {
|
||||
enableLog, ok := params[len(params)-1].(bool)
|
||||
if ok {
|
||||
e.EnableLog(enableLog)
|
||||
|
||||
parsedParamLen++
|
||||
}
|
||||
}
|
||||
|
||||
if len(params)-parsedParamLen == 2 {
|
||||
switch p0 := params[0].(type) {
|
||||
case string:
|
||||
switch p1 := params[1].(type) {
|
||||
case string:
|
||||
e.InitWithFile(p0, p1)
|
||||
default:
|
||||
e.InitWithAdapter(p0, p1.(persist.Adapter))
|
||||
}
|
||||
default:
|
||||
switch params[1].(type) {
|
||||
case string:
|
||||
panic("Invalid parameters for enforcer.")
|
||||
default:
|
||||
e.InitWithModelAndAdapter(p0.(model.Model), params[1].(persist.Adapter))
|
||||
}
|
||||
}
|
||||
} else if len(params)-parsedParamLen == 1 {
|
||||
switch p0 := params[0].(type) {
|
||||
case string:
|
||||
e.InitWithFile(p0, "")
|
||||
default:
|
||||
e.InitWithModelAndAdapter(p0.(model.Model), nil)
|
||||
}
|
||||
} else if len(params)-parsedParamLen == 0 {
|
||||
e.InitWithFile("", "")
|
||||
} else {
|
||||
panic("Invalid parameters for enforcer.")
|
||||
}
|
||||
|
||||
return e
|
||||
}
|
||||
|
||||
// InitWithFile initializes an enforcer with a model file and a policy file.
|
||||
func (e *Enforcer) InitWithFile(modelPath string, policyPath string) {
|
||||
a := fileadapter.NewAdapter(policyPath)
|
||||
e.InitWithAdapter(modelPath, a)
|
||||
}
|
||||
|
||||
// InitWithAdapter initializes an enforcer with a database adapter.
|
||||
func (e *Enforcer) InitWithAdapter(modelPath string, adapter persist.Adapter) {
|
||||
m := NewModel(modelPath, "")
|
||||
e.InitWithModelAndAdapter(m, adapter)
|
||||
|
||||
e.modelPath = modelPath
|
||||
}
|
||||
|
||||
// InitWithModelAndAdapter initializes an enforcer with a model and a database adapter.
|
||||
func (e *Enforcer) InitWithModelAndAdapter(m model.Model, adapter persist.Adapter) {
|
||||
e.adapter = adapter
|
||||
|
||||
e.model = m
|
||||
e.model.PrintModel()
|
||||
e.fm = model.LoadFunctionMap()
|
||||
|
||||
e.initialize()
|
||||
|
||||
if e.adapter != nil {
|
||||
// error intentionally ignored
|
||||
e.LoadPolicy()
|
||||
}
|
||||
}
|
||||
|
||||
func (e *Enforcer) initialize() {
|
||||
e.rm = defaultrolemanager.NewRoleManager(10)
|
||||
e.eft = effect.NewDefaultEffector()
|
||||
e.watcher = nil
|
||||
|
||||
e.enabled = true
|
||||
e.autoSave = true
|
||||
e.autoBuildRoleLinks = true
|
||||
}
|
||||
|
||||
// NewModel creates a model.
|
||||
func NewModel(text ...string) model.Model {
|
||||
m := make(model.Model)
|
||||
|
||||
if len(text) == 2 {
|
||||
if text[0] != "" {
|
||||
m.LoadModel(text[0])
|
||||
}
|
||||
} else if len(text) == 1 {
|
||||
m.LoadModelFromText(text[0])
|
||||
} else if len(text) != 0 {
|
||||
panic("Invalid parameters for model.")
|
||||
}
|
||||
|
||||
return m
|
||||
}
|
||||
|
||||
// LoadModel reloads the model from the model CONF file.
|
||||
// Because the policy is attached to a model, so the policy is invalidated and needs to be reloaded by calling LoadPolicy().
|
||||
func (e *Enforcer) LoadModel() {
|
||||
e.model = NewModel()
|
||||
e.model.LoadModel(e.modelPath)
|
||||
e.model.PrintModel()
|
||||
e.fm = model.LoadFunctionMap()
|
||||
}
|
||||
|
||||
// GetModel gets the current model.
|
||||
func (e *Enforcer) GetModel() model.Model {
|
||||
return e.model
|
||||
}
|
||||
|
||||
// SetModel sets the current model.
|
||||
func (e *Enforcer) SetModel(m model.Model) {
|
||||
e.model = m
|
||||
e.fm = model.LoadFunctionMap()
|
||||
}
|
||||
|
||||
// GetAdapter gets the current adapter.
|
||||
func (e *Enforcer) GetAdapter() persist.Adapter {
|
||||
return e.adapter
|
||||
}
|
||||
|
||||
// SetAdapter sets the current adapter.
|
||||
func (e *Enforcer) SetAdapter(adapter persist.Adapter) {
|
||||
e.adapter = adapter
|
||||
}
|
||||
|
||||
// SetWatcher sets the current watcher.
|
||||
func (e *Enforcer) SetWatcher(watcher persist.Watcher) {
|
||||
e.watcher = watcher
|
||||
// error intentionally ignored
|
||||
watcher.SetUpdateCallback(func(string) { e.LoadPolicy() })
|
||||
}
|
||||
|
||||
// SetRoleManager sets the current role manager.
|
||||
func (e *Enforcer) SetRoleManager(rm rbac.RoleManager) {
|
||||
e.rm = rm
|
||||
}
|
||||
|
||||
// SetEffector sets the current effector.
|
||||
func (e *Enforcer) SetEffector(eft effect.Effector) {
|
||||
e.eft = eft
|
||||
}
|
||||
|
||||
// ClearPolicy clears all policy.
|
||||
func (e *Enforcer) ClearPolicy() {
|
||||
e.model.ClearPolicy()
|
||||
}
|
||||
|
||||
// LoadPolicy reloads the policy from file/database.
|
||||
func (e *Enforcer) LoadPolicy() error {
|
||||
e.model.ClearPolicy()
|
||||
if err := e.adapter.LoadPolicy(e.model); err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
e.model.PrintPolicy()
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// LoadFilteredPolicy reloads a filtered policy from file/database.
|
||||
func (e *Enforcer) LoadFilteredPolicy(filter interface{}) error {
|
||||
e.model.ClearPolicy()
|
||||
|
||||
var filteredAdapter persist.FilteredAdapter
|
||||
|
||||
// Attempt to cast the Adapter as a FilteredAdapter
|
||||
switch adapter := e.adapter.(type) {
|
||||
case persist.FilteredAdapter:
|
||||
filteredAdapter = adapter
|
||||
default:
|
||||
return errors.New("filtered policies are not supported by this adapter")
|
||||
}
|
||||
if err := filteredAdapter.LoadFilteredPolicy(e.model, filter); err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
e.model.PrintPolicy()
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
func (e *Enforcer) IsFiltered() bool {
|
||||
filteredAdapter, ok := e.adapter.(persist.FilteredAdapter)
|
||||
if !ok {
|
||||
return false
|
||||
}
|
||||
return filteredAdapter.IsFiltered()
|
||||
}
|
||||
|
||||
// SavePolicy saves the current policy (usually after changed with Casbin API) back to file/database.
|
||||
func (e *Enforcer) SavePolicy() error {
|
||||
if e.IsFiltered() {
|
||||
return errors.New("cannot save a filtered policy")
|
||||
}
|
||||
if err := e.adapter.SavePolicy(e.model); err != nil {
|
||||
return err
|
||||
}
|
||||
if e.watcher != nil {
|
||||
return e.watcher.Update()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// EnableEnforce changes the enforcing state of Casbin, when Casbin is disabled, all access will be allowed by the Enforce() function.
|
||||
func (e *Enforcer) EnableEnforce(enable bool) {
|
||||
e.enabled = enable
|
||||
}
|
||||
|
||||
// EnableLog changes whether Casbin will log messages to the Logger.
|
||||
func (e *Enforcer) EnableLog(enable bool) {
|
||||
log.GetLogger().EnableLog(enable)
|
||||
}
|
||||
|
||||
// EnableAutoSave controls whether to save a policy rule automatically to the adapter when it is added or removed.
|
||||
func (e *Enforcer) EnableAutoSave(autoSave bool) {
|
||||
e.autoSave = autoSave
|
||||
}
|
||||
|
||||
// EnableAutoBuildRoleLinks controls whether to rebuild the role inheritance relations when a role is added or deleted.
|
||||
func (e *Enforcer) EnableAutoBuildRoleLinks(autoBuildRoleLinks bool) {
|
||||
e.autoBuildRoleLinks = autoBuildRoleLinks
|
||||
}
|
||||
|
||||
// BuildRoleLinks manually rebuild the role inheritance relations.
|
||||
func (e *Enforcer) BuildRoleLinks() {
|
||||
// error intentionally ignored
|
||||
e.rm.Clear()
|
||||
e.model.BuildRoleLinks(e.rm)
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
func (e *Enforcer) Enforce(rvals ...interface{}) bool {
|
||||
if !e.enabled {
|
||||
return true
|
||||
}
|
||||
|
||||
functions := make(map[string]govaluate.ExpressionFunction)
|
||||
for key, function := range e.fm {
|
||||
functions[key] = function
|
||||
}
|
||||
if _, ok := e.model["g"]; ok {
|
||||
for key, ast := range e.model["g"] {
|
||||
rm := ast.RM
|
||||
functions[key] = util.GenerateGFunction(rm)
|
||||
}
|
||||
}
|
||||
|
||||
expString := e.model["m"]["m"].Value
|
||||
expression, err := govaluate.NewEvaluableExpressionWithFunctions(expString, functions)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
var policyEffects []effect.Effect
|
||||
var matcherResults []float64
|
||||
if policyLen := len(e.model["p"]["p"].Policy); policyLen != 0 {
|
||||
policyEffects = make([]effect.Effect, policyLen)
|
||||
matcherResults = make([]float64, policyLen)
|
||||
|
||||
for i, pvals := range e.model["p"]["p"].Policy {
|
||||
// log.LogPrint("Policy Rule: ", pvals)
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
for j, token := range e.model["r"]["r"].Tokens {
|
||||
parameters[token] = rvals[j]
|
||||
}
|
||||
for j, token := range e.model["p"]["p"].Tokens {
|
||||
parameters[token] = pvals[j]
|
||||
}
|
||||
|
||||
result, err := expression.Evaluate(parameters)
|
||||
// log.LogPrint("Result: ", result)
|
||||
|
||||
if err != nil {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
panic(err)
|
||||
}
|
||||
|
||||
switch result := result.(type) {
|
||||
case bool:
|
||||
if !result {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
continue
|
||||
}
|
||||
case float64:
|
||||
if result == 0 {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
continue
|
||||
} else {
|
||||
matcherResults[i] = result
|
||||
}
|
||||
default:
|
||||
panic(errors.New("matcher result should be bool, int or float"))
|
||||
}
|
||||
|
||||
if eft, ok := parameters["p_eft"]; ok {
|
||||
if eft == "allow" {
|
||||
policyEffects[i] = effect.Allow
|
||||
} else if eft == "deny" {
|
||||
policyEffects[i] = effect.Deny
|
||||
} else {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
}
|
||||
} else {
|
||||
policyEffects[i] = effect.Allow
|
||||
}
|
||||
|
||||
if e.model["e"]["e"].Value == "priority(p_eft) || deny" {
|
||||
break
|
||||
}
|
||||
|
||||
}
|
||||
} else {
|
||||
policyEffects = make([]effect.Effect, 1)
|
||||
matcherResults = make([]float64, 1)
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
for j, token := range e.model["r"]["r"].Tokens {
|
||||
parameters[token] = rvals[j]
|
||||
}
|
||||
for _, token := range e.model["p"]["p"].Tokens {
|
||||
parameters[token] = ""
|
||||
}
|
||||
|
||||
result, err := expression.Evaluate(parameters)
|
||||
// log.LogPrint("Result: ", result)
|
||||
|
||||
if err != nil {
|
||||
policyEffects[0] = effect.Indeterminate
|
||||
panic(err)
|
||||
}
|
||||
|
||||
if result.(bool) {
|
||||
policyEffects[0] = effect.Allow
|
||||
} else {
|
||||
policyEffects[0] = effect.Indeterminate
|
||||
}
|
||||
}
|
||||
|
||||
// log.LogPrint("Rule Results: ", policyEffects)
|
||||
|
||||
result, err := e.eft.MergeEffects(e.model["e"]["e"].Value, policyEffects, matcherResults)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
// Log request.
|
||||
if log.GetLogger().IsEnabled() {
|
||||
reqStr := "Request: "
|
||||
for i, rval := range rvals {
|
||||
if i != len(rvals)-1 {
|
||||
reqStr += fmt.Sprintf("%v, ", rval)
|
||||
} else {
|
||||
reqStr += fmt.Sprintf("%v", rval)
|
||||
}
|
||||
}
|
||||
reqStr += fmt.Sprintf(" ---> %t", result)
|
||||
log.LogPrint(reqStr)
|
||||
}
|
||||
|
||||
return result
|
||||
}
|
||||
74
src/vendor/github.com/casbin/casbin/enforcer_cached.go
generated
vendored
Normal file
74
src/vendor/github.com/casbin/casbin/enforcer_cached.go
generated
vendored
Normal file
@ -0,0 +1,74 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"sync"
|
||||
)
|
||||
|
||||
// CachedEnforcer wraps Enforcer and provides decision cache
|
||||
type CachedEnforcer struct {
|
||||
*Enforcer
|
||||
m map[string]bool
|
||||
enableCache bool
|
||||
locker *sync.Mutex
|
||||
}
|
||||
|
||||
// NewCachedEnforcer creates a cached enforcer via file or DB.
|
||||
func NewCachedEnforcer(params ...interface{}) *CachedEnforcer {
|
||||
e := &CachedEnforcer{}
|
||||
e.Enforcer = NewEnforcer(params...)
|
||||
e.enableCache = true
|
||||
e.m = make(map[string]bool)
|
||||
e.locker = new(sync.Mutex)
|
||||
return e
|
||||
}
|
||||
|
||||
// EnableCache determines whether to enable cache on Enforce(). When enableCache is enabled, cached result (true | false) will be returned for previous decisions.
|
||||
func (e *CachedEnforcer) EnableCache(enableCache bool) {
|
||||
e.enableCache = enableCache
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
// if rvals is not string , ingore the cache
|
||||
func (e *CachedEnforcer) Enforce(rvals ...interface{}) bool {
|
||||
if !e.enableCache {
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
|
||||
key := ""
|
||||
for _, rval := range rvals {
|
||||
if val, ok := rval.(string); ok {
|
||||
key += val + "$$"
|
||||
} else {
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
}
|
||||
|
||||
e.locker.Lock()
|
||||
defer e.locker.Unlock()
|
||||
if _, ok := e.m[key]; ok {
|
||||
return e.m[key]
|
||||
} else {
|
||||
res := e.Enforcer.Enforce(rvals...)
|
||||
e.m[key] = res
|
||||
return res
|
||||
}
|
||||
}
|
||||
|
||||
// InvalidateCache deletes all the existing cached decisions.
|
||||
func (e *CachedEnforcer) InvalidateCache() {
|
||||
e.m = make(map[string]bool)
|
||||
}
|
||||
102
src/vendor/github.com/casbin/casbin/enforcer_safe.go
generated
vendored
Normal file
102
src/vendor/github.com/casbin/casbin/enforcer_safe.go
generated
vendored
Normal file
@ -0,0 +1,102 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
)
|
||||
|
||||
// NewEnforcerSafe calls NewEnforcer in a safe way, returns error instead of causing panic.
|
||||
func NewEnforcerSafe(params ...interface{}) (e *Enforcer, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
e = nil
|
||||
}
|
||||
}()
|
||||
|
||||
e = NewEnforcer(params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// LoadModelSafe calls LoadModel in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) LoadModelSafe() (err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
}
|
||||
}()
|
||||
|
||||
e.LoadModel()
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// EnforceSafe calls Enforce in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) EnforceSafe(rvals ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.Enforce(rvals...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// AddPolicySafe calls AddPolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) AddPolicySafe(params ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.AddNamedPolicy("p", params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// RemovePolicySafe calls RemovePolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) RemovePolicySafe(params ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.RemoveNamedPolicy("p", params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicySafe calls RemoveFilteredPolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) RemoveFilteredPolicySafe(fieldIndex int, fieldValues ...string) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.RemoveFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
223
src/vendor/github.com/casbin/casbin/enforcer_synced.go
generated
vendored
Normal file
223
src/vendor/github.com/casbin/casbin/enforcer_synced.go
generated
vendored
Normal file
@ -0,0 +1,223 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"log"
|
||||
"sync"
|
||||
"time"
|
||||
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// SyncedEnforcer wraps Enforcer and provides synchronized access
|
||||
type SyncedEnforcer struct {
|
||||
*Enforcer
|
||||
m sync.RWMutex
|
||||
autoLoad bool
|
||||
}
|
||||
|
||||
// NewSyncedEnforcer creates a synchronized enforcer via file or DB.
|
||||
func NewSyncedEnforcer(params ...interface{}) *SyncedEnforcer {
|
||||
e := &SyncedEnforcer{}
|
||||
e.Enforcer = NewEnforcer(params...)
|
||||
e.autoLoad = false
|
||||
return e
|
||||
}
|
||||
|
||||
// StartAutoLoadPolicy starts a go routine that will every specified duration call LoadPolicy
|
||||
func (e *SyncedEnforcer) StartAutoLoadPolicy(d time.Duration) {
|
||||
e.autoLoad = true
|
||||
go func() {
|
||||
n := 1
|
||||
log.Print("Start automatically load policy")
|
||||
for {
|
||||
if !e.autoLoad {
|
||||
log.Print("Stop automatically load policy")
|
||||
break
|
||||
}
|
||||
|
||||
// error intentionally ignored
|
||||
e.LoadPolicy()
|
||||
// Uncomment this line to see when the policy is loaded.
|
||||
// log.Print("Load policy for time: ", n)
|
||||
n++
|
||||
time.Sleep(d)
|
||||
}
|
||||
}()
|
||||
}
|
||||
|
||||
// StopAutoLoadPolicy causes the go routine to exit.
|
||||
func (e *SyncedEnforcer) StopAutoLoadPolicy() {
|
||||
e.autoLoad = false
|
||||
}
|
||||
|
||||
// SetWatcher sets the current watcher.
|
||||
func (e *SyncedEnforcer) SetWatcher(watcher persist.Watcher) {
|
||||
e.watcher = watcher
|
||||
// error intentionally ignored
|
||||
watcher.SetUpdateCallback(func(string) { e.LoadPolicy() })
|
||||
}
|
||||
|
||||
// ClearPolicy clears all policy.
|
||||
func (e *SyncedEnforcer) ClearPolicy() {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
e.Enforcer.ClearPolicy()
|
||||
}
|
||||
|
||||
// LoadPolicy reloads the policy from file/database.
|
||||
func (e *SyncedEnforcer) LoadPolicy() error {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.LoadPolicy()
|
||||
}
|
||||
|
||||
// SavePolicy saves the current policy (usually after changed with Casbin API) back to file/database.
|
||||
func (e *SyncedEnforcer) SavePolicy() error {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.SavePolicy()
|
||||
}
|
||||
|
||||
// BuildRoleLinks manually rebuild the role inheritance relations.
|
||||
func (e *SyncedEnforcer) BuildRoleLinks() {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
e.Enforcer.BuildRoleLinks()
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
func (e *SyncedEnforcer) Enforce(rvals ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
|
||||
// GetAllSubjects gets the list of subjects that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllSubjects() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllSubjects()
|
||||
}
|
||||
|
||||
// GetAllObjects gets the list of objects that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllObjects() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllObjects()
|
||||
}
|
||||
|
||||
// GetAllActions gets the list of actions that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllActions() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllActions()
|
||||
}
|
||||
|
||||
// GetAllRoles gets the list of roles that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllRoles() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllRoles()
|
||||
}
|
||||
|
||||
// GetPolicy gets all the authorization rules in the policy.
|
||||
func (e *SyncedEnforcer) GetPolicy() [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetPolicy()
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets all the authorization rules in the policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) GetFilteredPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetFilteredPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *SyncedEnforcer) GetGroupingPolicy() [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetGroupingPolicy()
|
||||
}
|
||||
|
||||
// GetFilteredGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) GetFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetFilteredGroupingPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasPolicy determines whether an authorization rule exists.
|
||||
func (e *SyncedEnforcer) HasPolicy(params ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.HasPolicy(params...)
|
||||
}
|
||||
|
||||
// AddPolicy adds an authorization rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *SyncedEnforcer) AddPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddPolicy(params...)
|
||||
}
|
||||
|
||||
// RemovePolicy removes an authorization rule from the current policy.
|
||||
func (e *SyncedEnforcer) RemovePolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemovePolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes an authorization rule from the current policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) RemoveFilteredPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveFilteredPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasGroupingPolicy determines whether a role inheritance rule exists.
|
||||
func (e *SyncedEnforcer) HasGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.HasGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// AddGroupingPolicy adds a role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *SyncedEnforcer) AddGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveGroupingPolicy removes a role inheritance rule from the current policy.
|
||||
func (e *SyncedEnforcer) RemoveGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredGroupingPolicy removes a role inheritance rule from the current policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) RemoveFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveFilteredGroupingPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
85
src/vendor/github.com/casbin/casbin/internal_api.go
generated
vendored
Normal file
85
src/vendor/github.com/casbin/casbin/internal_api.go
generated
vendored
Normal file
@ -0,0 +1,85 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
const (
|
||||
notImplemented = "not implemented"
|
||||
)
|
||||
|
||||
// addPolicy adds a rule to the current policy.
|
||||
func (e *Enforcer) addPolicy(sec string, ptype string, rule []string) bool {
|
||||
ruleAdded := e.model.AddPolicy(sec, ptype, rule)
|
||||
if !ruleAdded {
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.AddPolicy(sec, ptype, rule); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// removePolicy removes a rule from the current policy.
|
||||
func (e *Enforcer) removePolicy(sec string, ptype string, rule []string) bool {
|
||||
ruleRemoved := e.model.RemovePolicy(sec, ptype, rule)
|
||||
if !ruleRemoved {
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.RemovePolicy(sec, ptype, rule); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// removeFilteredPolicy removes rules based on field filters from the current policy.
|
||||
func (e *Enforcer) removeFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
ruleRemoved := e.model.RemoveFilteredPolicy(sec, ptype, fieldIndex, fieldValues...)
|
||||
if !ruleRemoved {
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.RemoveFilteredPolicy(sec, ptype, fieldIndex, fieldValues...); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
42
src/vendor/github.com/casbin/casbin/log/default_logger.go
generated
vendored
Normal file
42
src/vendor/github.com/casbin/casbin/log/default_logger.go
generated
vendored
Normal file
@ -0,0 +1,42 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package log
|
||||
|
||||
import "log"
|
||||
|
||||
// DefaultLogger is the implementation for a Logger using golang log.
|
||||
type DefaultLogger struct {
|
||||
enable bool
|
||||
}
|
||||
|
||||
func (l *DefaultLogger) EnableLog(enable bool) {
|
||||
l.enable = enable
|
||||
}
|
||||
|
||||
func (l *DefaultLogger) IsEnabled() bool {
|
||||
return l.enable
|
||||
}
|
||||
|
||||
func (l *DefaultLogger) Print(v ...interface{}) {
|
||||
if l.enable {
|
||||
log.Print(v...)
|
||||
}
|
||||
}
|
||||
|
||||
func (l *DefaultLogger) Printf(format string, v ...interface{}) {
|
||||
if l.enable {
|
||||
log.Printf(format, v...)
|
||||
}
|
||||
}
|
||||
37
src/vendor/github.com/casbin/casbin/log/log_util.go
generated
vendored
Normal file
37
src/vendor/github.com/casbin/casbin/log/log_util.go
generated
vendored
Normal file
@ -0,0 +1,37 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package log
|
||||
|
||||
var logger Logger = &DefaultLogger{}
|
||||
|
||||
// SetLogger sets the current logger.
|
||||
func SetLogger(l Logger) {
|
||||
logger = l
|
||||
}
|
||||
|
||||
// GetLogger returns the current logger.
|
||||
func GetLogger() Logger {
|
||||
return logger
|
||||
}
|
||||
|
||||
// LogPrint prints the log.
|
||||
func LogPrint(v ...interface{}) {
|
||||
logger.Print(v...)
|
||||
}
|
||||
|
||||
// LogPrintf prints the log with the format.
|
||||
func LogPrintf(format string, v ...interface{}) {
|
||||
logger.Printf(format, v...)
|
||||
}
|
||||
30
src/vendor/github.com/casbin/casbin/log/logger.go
generated
vendored
Normal file
30
src/vendor/github.com/casbin/casbin/log/logger.go
generated
vendored
Normal file
@ -0,0 +1,30 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package log
|
||||
|
||||
// Logger is the logging interface implementation.
|
||||
type Logger interface {
|
||||
//EnableLog controls whether print the message.
|
||||
EnableLog(bool)
|
||||
|
||||
//IsEnabled returns if logger is enabled.
|
||||
IsEnabled() bool
|
||||
|
||||
//Print formats using the default formats for its operands and logs the message.
|
||||
Print(...interface{})
|
||||
|
||||
//Printf formats according to a format specifier and logs the message.
|
||||
Printf(string, ...interface{})
|
||||
}
|
||||
265
src/vendor/github.com/casbin/casbin/management_api.go
generated
vendored
Normal file
265
src/vendor/github.com/casbin/casbin/management_api.go
generated
vendored
Normal file
@ -0,0 +1,265 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetAllSubjects gets the list of subjects that show up in the current policy.
|
||||
func (e *Enforcer) GetAllSubjects() []string {
|
||||
return e.GetAllNamedSubjects("p")
|
||||
}
|
||||
|
||||
// GetAllNamedSubjects gets the list of subjects that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedSubjects(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 0)
|
||||
}
|
||||
|
||||
// GetAllObjects gets the list of objects that show up in the current policy.
|
||||
func (e *Enforcer) GetAllObjects() []string {
|
||||
return e.GetAllNamedObjects("p")
|
||||
}
|
||||
|
||||
// GetAllNamedObjects gets the list of objects that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedObjects(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 1)
|
||||
}
|
||||
|
||||
// GetAllActions gets the list of actions that show up in the current policy.
|
||||
func (e *Enforcer) GetAllActions() []string {
|
||||
return e.GetAllNamedActions("p")
|
||||
}
|
||||
|
||||
// GetAllNamedActions gets the list of actions that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedActions(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 2)
|
||||
}
|
||||
|
||||
// GetAllRoles gets the list of roles that show up in the current policy.
|
||||
func (e *Enforcer) GetAllRoles() []string {
|
||||
return e.GetAllNamedRoles("g")
|
||||
}
|
||||
|
||||
// GetAllNamedRoles gets the list of roles that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedRoles(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("g", ptype, 1)
|
||||
}
|
||||
|
||||
// GetPolicy gets all the authorization rules in the policy.
|
||||
func (e *Enforcer) GetPolicy() [][]string {
|
||||
return e.GetNamedPolicy("p")
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets all the authorization rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.GetFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetNamedPolicy gets all the authorization rules in the named policy.
|
||||
func (e *Enforcer) GetNamedPolicy(ptype string) [][]string {
|
||||
return e.model.GetPolicy("p", ptype)
|
||||
}
|
||||
|
||||
// GetFilteredNamedPolicy gets all the authorization rules in the named policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredNamedPolicy(ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.model.GetFilteredPolicy("p", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *Enforcer) GetGroupingPolicy() [][]string {
|
||||
return e.GetNamedGroupingPolicy("g")
|
||||
}
|
||||
|
||||
// GetFilteredGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.GetFilteredNamedGroupingPolicy("g", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetNamedGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *Enforcer) GetNamedGroupingPolicy(ptype string) [][]string {
|
||||
return e.model.GetPolicy("g", ptype)
|
||||
}
|
||||
|
||||
// GetFilteredNamedGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredNamedGroupingPolicy(ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.model.GetFilteredPolicy("g", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasPolicy determines whether an authorization rule exists.
|
||||
func (e *Enforcer) HasPolicy(params ...interface{}) bool {
|
||||
return e.HasNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// HasNamedPolicy determines whether a named authorization rule exists.
|
||||
func (e *Enforcer) HasNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
return e.model.HasPolicy("p", ptype, strSlice)
|
||||
}
|
||||
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
return e.model.HasPolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
// AddPolicy adds an authorization rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddPolicy(params ...interface{}) bool {
|
||||
return e.AddNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// AddNamedPolicy adds an authorization rule to the current named policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleAdded bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleAdded = e.addPolicy("p", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleAdded = e.addPolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// RemovePolicy removes an authorization rule from the current policy.
|
||||
func (e *Enforcer) RemovePolicy(params ...interface{}) bool {
|
||||
return e.RemoveNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes an authorization rule from the current policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
return e.RemoveFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// RemoveNamedPolicy removes an authorization rule from the current named policy.
|
||||
func (e *Enforcer) RemoveNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleRemoved bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleRemoved = e.removePolicy("p", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleRemoved = e.removePolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// RemoveFilteredNamedPolicy removes an authorization rule from the current named policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredNamedPolicy(ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
return e.removeFilteredPolicy("p", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasGroupingPolicy determines whether a role inheritance rule exists.
|
||||
func (e *Enforcer) HasGroupingPolicy(params ...interface{}) bool {
|
||||
return e.HasNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// HasNamedGroupingPolicy determines whether a named role inheritance rule exists.
|
||||
func (e *Enforcer) HasNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
return e.model.HasPolicy("g", ptype, strSlice)
|
||||
}
|
||||
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
return e.model.HasPolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
// AddGroupingPolicy adds a role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddGroupingPolicy(params ...interface{}) bool {
|
||||
return e.AddNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// AddNamedGroupingPolicy adds a named role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleAdded bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleAdded = e.addPolicy("g", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleAdded = e.addPolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// RemoveGroupingPolicy removes a role inheritance rule from the current policy.
|
||||
func (e *Enforcer) RemoveGroupingPolicy(params ...interface{}) bool {
|
||||
return e.RemoveNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredGroupingPolicy removes a role inheritance rule from the current policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
return e.RemoveFilteredNamedGroupingPolicy("g", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// RemoveNamedGroupingPolicy removes a role inheritance rule from the current named policy.
|
||||
func (e *Enforcer) RemoveNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleRemoved bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleRemoved = e.removePolicy("g", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleRemoved = e.removePolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// RemoveFilteredNamedGroupingPolicy removes a role inheritance rule from the current named policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredNamedGroupingPolicy(ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
ruleRemoved := e.removeFilteredPolicy("g", ptype, fieldIndex, fieldValues...)
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// AddFunction adds a customized function.
|
||||
func (e *Enforcer) AddFunction(name string, function func(args ...interface{}) (interface{}, error)) {
|
||||
e.fm.AddFunction(name, function)
|
||||
}
|
||||
60
src/vendor/github.com/casbin/casbin/model/assertion.go
generated
vendored
Normal file
60
src/vendor/github.com/casbin/casbin/model/assertion.go
generated
vendored
Normal file
@ -0,0 +1,60 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/log"
|
||||
"github.com/casbin/casbin/rbac"
|
||||
)
|
||||
|
||||
// Assertion represents an expression in a section of the model.
|
||||
// For example: r = sub, obj, act
|
||||
type Assertion struct {
|
||||
Key string
|
||||
Value string
|
||||
Tokens []string
|
||||
Policy [][]string
|
||||
RM rbac.RoleManager
|
||||
}
|
||||
|
||||
func (ast *Assertion) buildRoleLinks(rm rbac.RoleManager) {
|
||||
ast.RM = rm
|
||||
count := strings.Count(ast.Value, "_")
|
||||
for _, rule := range ast.Policy {
|
||||
if count < 2 {
|
||||
panic(errors.New("the number of \"_\" in role definition should be at least 2"))
|
||||
}
|
||||
if len(rule) < count {
|
||||
panic(errors.New("grouping policy elements do not meet role definition"))
|
||||
}
|
||||
|
||||
if count == 2 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1])
|
||||
} else if count == 3 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1], rule[2])
|
||||
} else if count == 4 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1], rule[2], rule[3])
|
||||
}
|
||||
}
|
||||
|
||||
log.LogPrint("Role links for: " + ast.Key)
|
||||
ast.RM.PrintRoles()
|
||||
}
|
||||
40
src/vendor/github.com/casbin/casbin/model/function.go
generated
vendored
Normal file
40
src/vendor/github.com/casbin/casbin/model/function.go
generated
vendored
Normal file
@ -0,0 +1,40 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import "github.com/casbin/casbin/util"
|
||||
|
||||
// FunctionMap represents the collection of Function.
|
||||
type FunctionMap map[string]func(args ...interface{}) (interface{}, error)
|
||||
|
||||
// Function represents a function that is used in the matchers, used to get attributes in ABAC.
|
||||
type Function func(args ...interface{}) (interface{}, error)
|
||||
|
||||
// AddFunction adds an expression function.
|
||||
func (fm FunctionMap) AddFunction(name string, function Function) {
|
||||
fm[name] = function
|
||||
}
|
||||
|
||||
// LoadFunctionMap loads an initial function map.
|
||||
func LoadFunctionMap() FunctionMap {
|
||||
fm := make(FunctionMap)
|
||||
|
||||
fm.AddFunction("keyMatch", util.KeyMatchFunc)
|
||||
fm.AddFunction("keyMatch2", util.KeyMatch2Func)
|
||||
fm.AddFunction("regexMatch", util.RegexMatchFunc)
|
||||
fm.AddFunction("ipMatch", util.IPMatchFunc)
|
||||
|
||||
return fm
|
||||
}
|
||||
130
src/vendor/github.com/casbin/casbin/model/model.go
generated
vendored
Normal file
130
src/vendor/github.com/casbin/casbin/model/model.go
generated
vendored
Normal file
@ -0,0 +1,130 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"strconv"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/config"
|
||||
"github.com/casbin/casbin/log"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Model represents the whole access control model.
|
||||
type Model map[string]AssertionMap
|
||||
|
||||
// AssertionMap is the collection of assertions, can be "r", "p", "g", "e", "m".
|
||||
type AssertionMap map[string]*Assertion
|
||||
|
||||
var sectionNameMap = map[string]string{
|
||||
"r": "request_definition",
|
||||
"p": "policy_definition",
|
||||
"g": "role_definition",
|
||||
"e": "policy_effect",
|
||||
"m": "matchers",
|
||||
}
|
||||
|
||||
func loadAssertion(model Model, cfg config.ConfigInterface, sec string, key string) bool {
|
||||
value := cfg.String(sectionNameMap[sec] + "::" + key)
|
||||
return model.AddDef(sec, key, value)
|
||||
}
|
||||
|
||||
// AddDef adds an assertion to the model.
|
||||
func (model Model) AddDef(sec string, key string, value string) bool {
|
||||
ast := Assertion{}
|
||||
ast.Key = key
|
||||
ast.Value = value
|
||||
|
||||
if ast.Value == "" {
|
||||
return false
|
||||
}
|
||||
|
||||
if sec == "r" || sec == "p" {
|
||||
ast.Tokens = strings.Split(ast.Value, ", ")
|
||||
for i := range ast.Tokens {
|
||||
ast.Tokens[i] = key + "_" + ast.Tokens[i]
|
||||
}
|
||||
} else {
|
||||
ast.Value = util.RemoveComments(util.EscapeAssertion(ast.Value))
|
||||
}
|
||||
|
||||
_, ok := model[sec]
|
||||
if !ok {
|
||||
model[sec] = make(AssertionMap)
|
||||
}
|
||||
|
||||
model[sec][key] = &ast
|
||||
return true
|
||||
}
|
||||
|
||||
func getKeySuffix(i int) string {
|
||||
if i == 1 {
|
||||
return ""
|
||||
}
|
||||
|
||||
return strconv.Itoa(i)
|
||||
}
|
||||
|
||||
func loadSection(model Model, cfg config.ConfigInterface, sec string) {
|
||||
i := 1
|
||||
for {
|
||||
if !loadAssertion(model, cfg, sec, sec+getKeySuffix(i)) {
|
||||
break
|
||||
} else {
|
||||
i++
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// LoadModel loads the model from model CONF file.
|
||||
func (model Model) LoadModel(path string) {
|
||||
cfg, err := config.NewConfig(path)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
loadSection(model, cfg, "r")
|
||||
loadSection(model, cfg, "p")
|
||||
loadSection(model, cfg, "e")
|
||||
loadSection(model, cfg, "m")
|
||||
|
||||
loadSection(model, cfg, "g")
|
||||
}
|
||||
|
||||
// LoadModelFromText loads the model from the text.
|
||||
func (model Model) LoadModelFromText(text string) {
|
||||
cfg, err := config.NewConfigFromText(text)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
loadSection(model, cfg, "r")
|
||||
loadSection(model, cfg, "p")
|
||||
loadSection(model, cfg, "e")
|
||||
loadSection(model, cfg, "m")
|
||||
|
||||
loadSection(model, cfg, "g")
|
||||
}
|
||||
|
||||
// PrintModel prints the model to the log.
|
||||
func (model Model) PrintModel() {
|
||||
log.LogPrint("Model:")
|
||||
for k, v := range model {
|
||||
for i, j := range v {
|
||||
log.LogPrintf("%s.%s: %s", k, i, j.Value)
|
||||
}
|
||||
}
|
||||
}
|
||||
146
src/vendor/github.com/casbin/casbin/model/policy.go
generated
vendored
Normal file
146
src/vendor/github.com/casbin/casbin/model/policy.go
generated
vendored
Normal file
@ -0,0 +1,146 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"github.com/casbin/casbin/log"
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// BuildRoleLinks initializes the roles in RBAC.
|
||||
func (model Model) BuildRoleLinks(rm rbac.RoleManager) {
|
||||
for _, ast := range model["g"] {
|
||||
ast.buildRoleLinks(rm)
|
||||
}
|
||||
}
|
||||
|
||||
// PrintPolicy prints the policy to log.
|
||||
func (model Model) PrintPolicy() {
|
||||
log.LogPrint("Policy:")
|
||||
for key, ast := range model["p"] {
|
||||
log.LogPrint(key, ": ", ast.Value, ": ", ast.Policy)
|
||||
}
|
||||
|
||||
for key, ast := range model["g"] {
|
||||
log.LogPrint(key, ": ", ast.Value, ": ", ast.Policy)
|
||||
}
|
||||
}
|
||||
|
||||
// ClearPolicy clears all current policy.
|
||||
func (model Model) ClearPolicy() {
|
||||
for _, ast := range model["p"] {
|
||||
ast.Policy = nil
|
||||
}
|
||||
|
||||
for _, ast := range model["g"] {
|
||||
ast.Policy = nil
|
||||
}
|
||||
}
|
||||
|
||||
// GetPolicy gets all rules in a policy.
|
||||
func (model Model) GetPolicy(sec string, ptype string) [][]string {
|
||||
return model[sec][ptype].Policy
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets rules based on field filters from a policy.
|
||||
func (model Model) GetFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
res := [][]string{}
|
||||
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
matched := true
|
||||
for i, fieldValue := range fieldValues {
|
||||
if fieldValue != "" && rule[fieldIndex+i] != fieldValue {
|
||||
matched = false
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if matched {
|
||||
res = append(res, rule)
|
||||
}
|
||||
}
|
||||
|
||||
return res
|
||||
}
|
||||
|
||||
// HasPolicy determines whether a model has the specified policy rule.
|
||||
func (model Model) HasPolicy(sec string, ptype string, rule []string) bool {
|
||||
for _, r := range model[sec][ptype].Policy {
|
||||
if util.ArrayEquals(rule, r) {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the model.
|
||||
func (model Model) AddPolicy(sec string, ptype string, rule []string) bool {
|
||||
if !model.HasPolicy(sec, ptype, rule) {
|
||||
model[sec][ptype].Policy = append(model[sec][ptype].Policy, rule)
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the model.
|
||||
func (model Model) RemovePolicy(sec string, ptype string, rule []string) bool {
|
||||
for i, r := range model[sec][ptype].Policy {
|
||||
if util.ArrayEquals(rule, r) {
|
||||
model[sec][ptype].Policy = append(model[sec][ptype].Policy[:i], model[sec][ptype].Policy[i+1:]...)
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules based on field filters from the model.
|
||||
func (model Model) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
tmp := [][]string{}
|
||||
res := false
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
matched := true
|
||||
for i, fieldValue := range fieldValues {
|
||||
if fieldValue != "" && rule[fieldIndex+i] != fieldValue {
|
||||
matched = false
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if matched {
|
||||
res = true
|
||||
} else {
|
||||
tmp = append(tmp, rule)
|
||||
}
|
||||
}
|
||||
|
||||
model[sec][ptype].Policy = tmp
|
||||
return res
|
||||
}
|
||||
|
||||
// GetValuesForFieldInPolicy gets all values for a field for all rules in a policy, duplicated values are removed.
|
||||
func (model Model) GetValuesForFieldInPolicy(sec string, ptype string, fieldIndex int) []string {
|
||||
values := []string{}
|
||||
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
values = append(values, rule[fieldIndex])
|
||||
}
|
||||
|
||||
util.ArrayRemoveDuplicates(&values)
|
||||
|
||||
return values
|
||||
}
|
||||
56
src/vendor/github.com/casbin/casbin/persist/adapter.go
generated
vendored
Normal file
56
src/vendor/github.com/casbin/casbin/persist/adapter.go
generated
vendored
Normal file
@ -0,0 +1,56 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
import (
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
)
|
||||
|
||||
// LoadPolicyLine loads a text line as a policy rule to model.
|
||||
func LoadPolicyLine(line string, model model.Model) {
|
||||
if line == "" {
|
||||
return
|
||||
}
|
||||
|
||||
if strings.HasPrefix(line, "#") {
|
||||
return
|
||||
}
|
||||
|
||||
tokens := strings.Split(line, ", ")
|
||||
|
||||
key := tokens[0]
|
||||
sec := key[:1]
|
||||
model[sec][key].Policy = append(model[sec][key].Policy, tokens[1:])
|
||||
}
|
||||
|
||||
// Adapter is the interface for Casbin adapters.
|
||||
type Adapter interface {
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
LoadPolicy(model model.Model) error
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
SavePolicy(model model.Model) error
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
AddPolicy(sec string, ptype string, rule []string) error
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
RemovePolicy(sec string, ptype string, rule []string) error
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error
|
||||
}
|
||||
29
src/vendor/github.com/casbin/casbin/persist/adapter_filtered.go
generated
vendored
Normal file
29
src/vendor/github.com/casbin/casbin/persist/adapter_filtered.go
generated
vendored
Normal file
@ -0,0 +1,29 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
import (
|
||||
"github.com/casbin/casbin/model"
|
||||
)
|
||||
|
||||
// FilteredAdapter is the interface for Casbin adapters supporting filtered policies.
|
||||
type FilteredAdapter interface {
|
||||
Adapter
|
||||
|
||||
// LoadFilteredPolicy loads only policy rules that match the filter.
|
||||
LoadFilteredPolicy(model model.Model, filter interface{}) error
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
IsFiltered() bool
|
||||
}
|
||||
117
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter.go
generated
vendored
Normal file
117
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter.go
generated
vendored
Normal file
@ -0,0 +1,117 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"bytes"
|
||||
"errors"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Adapter is the file adapter for Casbin.
|
||||
// It can load policy from file or save policy to file.
|
||||
type Adapter struct {
|
||||
filePath string
|
||||
}
|
||||
|
||||
// NewAdapter is the constructor for Adapter.
|
||||
func NewAdapter(filePath string) *Adapter {
|
||||
return &Adapter{filePath: filePath}
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *Adapter) LoadPolicy(model model.Model) error {
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
return a.loadPolicyFile(model, persist.LoadPolicyLine)
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *Adapter) SavePolicy(model model.Model) error {
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
var tmp bytes.Buffer
|
||||
|
||||
for ptype, ast := range model["p"] {
|
||||
for _, rule := range ast.Policy {
|
||||
tmp.WriteString(ptype + ", ")
|
||||
tmp.WriteString(util.ArrayToString(rule))
|
||||
tmp.WriteString("\n")
|
||||
}
|
||||
}
|
||||
|
||||
for ptype, ast := range model["g"] {
|
||||
for _, rule := range ast.Policy {
|
||||
tmp.WriteString(ptype + ", ")
|
||||
tmp.WriteString(util.ArrayToString(rule))
|
||||
tmp.WriteString("\n")
|
||||
}
|
||||
}
|
||||
|
||||
return a.savePolicyFile(strings.TrimRight(tmp.String(), "\n"))
|
||||
}
|
||||
|
||||
func (a *Adapter) loadPolicyFile(model model.Model, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
scanner := bufio.NewScanner(f)
|
||||
for scanner.Scan() {
|
||||
line := strings.TrimSpace(scanner.Text())
|
||||
handler(line, model)
|
||||
}
|
||||
return scanner.Err()
|
||||
}
|
||||
|
||||
func (a *Adapter) savePolicyFile(text string) error {
|
||||
f, err := os.Create(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
w := bufio.NewWriter(f)
|
||||
// error intentionally ignored
|
||||
w.WriteString(text)
|
||||
w.Flush()
|
||||
f.Close()
|
||||
return nil
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
func (a *Adapter) AddPolicy(sec string, ptype string, rule []string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
func (a *Adapter) RemovePolicy(sec string, ptype string, rule []string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
func (a *Adapter) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
137
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter_filtered.go
generated
vendored
Normal file
137
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter_filtered.go
generated
vendored
Normal file
@ -0,0 +1,137 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"errors"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// FilteredAdapter is the filtered file adapter for Casbin. It can load policy
|
||||
// from file or save policy to file and supports loading of filtered policies.
|
||||
type FilteredAdapter struct {
|
||||
*Adapter
|
||||
filtered bool
|
||||
}
|
||||
|
||||
// Filter defines the filtering rules for a FilteredAdapter's policy. Empty values
|
||||
// are ignored, but all others must match the filter.
|
||||
type Filter struct {
|
||||
P []string
|
||||
G []string
|
||||
}
|
||||
|
||||
// NewFilteredAdapter is the constructor for FilteredAdapter.
|
||||
func NewFilteredAdapter(filePath string) *FilteredAdapter {
|
||||
a := FilteredAdapter{}
|
||||
a.Adapter = NewAdapter(filePath)
|
||||
return &a
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *FilteredAdapter) LoadPolicy(model model.Model) error {
|
||||
a.filtered = false
|
||||
return a.Adapter.LoadPolicy(model)
|
||||
}
|
||||
|
||||
// LoadFilteredPolicy loads only policy rules that match the filter.
|
||||
func (a *FilteredAdapter) LoadFilteredPolicy(model model.Model, filter interface{}) error {
|
||||
if filter == nil {
|
||||
return a.LoadPolicy(model)
|
||||
}
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
filterValue, ok := filter.(*Filter)
|
||||
if !ok {
|
||||
return errors.New("invalid filter type")
|
||||
}
|
||||
err := a.loadFilteredPolicyFile(model, filterValue, persist.LoadPolicyLine)
|
||||
if err == nil {
|
||||
a.filtered = true
|
||||
}
|
||||
return err
|
||||
}
|
||||
|
||||
func (a *FilteredAdapter) loadFilteredPolicyFile(model model.Model, filter *Filter, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
scanner := bufio.NewScanner(f)
|
||||
for scanner.Scan() {
|
||||
line := strings.TrimSpace(scanner.Text())
|
||||
|
||||
if filterLine(line, filter) {
|
||||
continue
|
||||
}
|
||||
|
||||
handler(line, model)
|
||||
}
|
||||
return scanner.Err()
|
||||
}
|
||||
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
func (a *FilteredAdapter) IsFiltered() bool {
|
||||
return a.filtered
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *FilteredAdapter) SavePolicy(model model.Model) error {
|
||||
if a.filtered {
|
||||
return errors.New("cannot save a filtered policy")
|
||||
}
|
||||
return a.Adapter.SavePolicy(model)
|
||||
}
|
||||
|
||||
func filterLine(line string, filter *Filter) bool {
|
||||
if filter == nil {
|
||||
return false
|
||||
}
|
||||
p := strings.Split(line, ",")
|
||||
if len(p) == 0 {
|
||||
return true
|
||||
}
|
||||
var filterSlice []string
|
||||
switch strings.TrimSpace(p[0]) {
|
||||
case "p":
|
||||
filterSlice = filter.P
|
||||
case "g":
|
||||
filterSlice = filter.G
|
||||
}
|
||||
return filterWords(p, filterSlice)
|
||||
}
|
||||
|
||||
func filterWords(line []string, filter []string) bool {
|
||||
if len(line) < len(filter)+1 {
|
||||
return true
|
||||
}
|
||||
var skipLine bool
|
||||
for i, v := range filter {
|
||||
if len(v) > 0 && strings.TrimSpace(v) != strings.TrimSpace(line[i+1]) {
|
||||
skipLine = true
|
||||
break
|
||||
}
|
||||
}
|
||||
return skipLine
|
||||
}
|
||||
100
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter_mock.go
generated
vendored
Normal file
100
src/vendor/github.com/casbin/casbin/persist/file-adapter/adapter_mock.go
generated
vendored
Normal file
@ -0,0 +1,100 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"errors"
|
||||
"io"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// AdapterMock is the file adapter for Casbin.
|
||||
// It can load policy from file or save policy to file.
|
||||
type AdapterMock struct {
|
||||
filePath string
|
||||
errorValue string
|
||||
}
|
||||
|
||||
// NewAdapterMock is the constructor for AdapterMock.
|
||||
func NewAdapterMock(filePath string) *AdapterMock {
|
||||
a := AdapterMock{}
|
||||
a.filePath = filePath
|
||||
return &a
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *AdapterMock) LoadPolicy(model model.Model) error {
|
||||
err := a.loadPolicyFile(model, persist.LoadPolicyLine)
|
||||
return err
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *AdapterMock) SavePolicy(model model.Model) error {
|
||||
return nil
|
||||
}
|
||||
|
||||
func (a *AdapterMock) loadPolicyFile(model model.Model, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
buf := bufio.NewReader(f)
|
||||
for {
|
||||
line, err := buf.ReadString('\n')
|
||||
line = strings.TrimSpace(line)
|
||||
handler(line, model)
|
||||
if err != nil {
|
||||
if err == io.EOF {
|
||||
return nil
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// SetMockErr sets string to be returned by of the mock during testing
|
||||
func (a *AdapterMock) SetMockErr(errorToSet string) {
|
||||
a.errorValue = errorToSet
|
||||
}
|
||||
|
||||
// GetMockErr returns a mock error or nil
|
||||
func (a *AdapterMock) GetMockErr() error {
|
||||
var returnError error
|
||||
if a.errorValue != "" {
|
||||
returnError = errors.New(a.errorValue)
|
||||
}
|
||||
return returnError
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
func (a *AdapterMock) AddPolicy(sec string, ptype string, rule []string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
func (a *AdapterMock) RemovePolicy(sec string, ptype string, rule []string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
func (a *AdapterMock) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
27
src/vendor/github.com/casbin/casbin/persist/watcher.go
generated
vendored
Normal file
27
src/vendor/github.com/casbin/casbin/persist/watcher.go
generated
vendored
Normal file
@ -0,0 +1,27 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
// Watcher is the interface for Casbin watchers.
|
||||
type Watcher interface {
|
||||
// SetUpdateCallback sets the callback function that the watcher will call
|
||||
// when the policy in DB has been changed by other instances.
|
||||
// A classic callback is Enforcer.LoadPolicy().
|
||||
SetUpdateCallback(func(string)) error
|
||||
// Update calls the update callback of other instances to synchronize their policy.
|
||||
// It is usually called after changing the policy in DB, like Enforcer.SavePolicy(),
|
||||
// Enforcer.AddPolicy(), Enforcer.RemovePolicy(), etc.
|
||||
Update() error
|
||||
}
|
||||
257
src/vendor/github.com/casbin/casbin/rbac/default-role-manager/role_manager.go
generated
vendored
Normal file
257
src/vendor/github.com/casbin/casbin/rbac/default-role-manager/role_manager.go
generated
vendored
Normal file
@ -0,0 +1,257 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package defaultrolemanager
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"sync"
|
||||
|
||||
"github.com/casbin/casbin/log"
|
||||
"github.com/casbin/casbin/rbac"
|
||||
)
|
||||
|
||||
// RoleManager provides a default implementation for the RoleManager interface
|
||||
type RoleManager struct {
|
||||
allRoles *sync.Map
|
||||
maxHierarchyLevel int
|
||||
}
|
||||
|
||||
// NewRoleManager is the constructor for creating an instance of the
|
||||
// default RoleManager implementation.
|
||||
func NewRoleManager(maxHierarchyLevel int) rbac.RoleManager {
|
||||
rm := RoleManager{}
|
||||
rm.allRoles = &sync.Map{}
|
||||
rm.maxHierarchyLevel = maxHierarchyLevel
|
||||
return &rm
|
||||
}
|
||||
|
||||
func (rm *RoleManager) hasRole(name string) bool {
|
||||
_, ok := rm.allRoles.Load(name)
|
||||
return ok
|
||||
}
|
||||
|
||||
func (rm *RoleManager) createRole(name string) *Role {
|
||||
role, _ := rm.allRoles.LoadOrStore(name, newRole(name))
|
||||
return role.(*Role)
|
||||
}
|
||||
|
||||
// Clear clears all stored data and resets the role manager to the initial state.
|
||||
func (rm *RoleManager) Clear() error {
|
||||
rm.allRoles = &sync.Map{}
|
||||
return nil
|
||||
}
|
||||
|
||||
// AddLink adds the inheritance link between role: name1 and role: name2.
|
||||
// aka role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) AddLink(name1 string, name2 string, domain ...string) error {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
role2 := rm.createRole(name2)
|
||||
role1.addRole(role2)
|
||||
return nil
|
||||
}
|
||||
|
||||
// DeleteLink deletes the inheritance link between role: name1 and role: name2.
|
||||
// aka role: name1 does not inherit role: name2 any more.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) DeleteLink(name1 string, name2 string, domain ...string) error {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if !rm.hasRole(name1) || !rm.hasRole(name2) {
|
||||
return errors.New("error: name1 or name2 does not exist")
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
role2 := rm.createRole(name2)
|
||||
role1.deleteRole(role2)
|
||||
return nil
|
||||
}
|
||||
|
||||
// HasLink determines whether role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) HasLink(name1 string, name2 string, domain ...string) (bool, error) {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return false, errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if name1 == name2 {
|
||||
return true, nil
|
||||
}
|
||||
|
||||
if !rm.hasRole(name1) || !rm.hasRole(name2) {
|
||||
return false, nil
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
return role1.hasRole(name2, rm.maxHierarchyLevel), nil
|
||||
}
|
||||
|
||||
// GetRoles gets the roles that a subject inherits.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) GetRoles(name string, domain ...string) ([]string, error) {
|
||||
if len(domain) == 1 {
|
||||
name = domain[0] + "::" + name
|
||||
} else if len(domain) > 1 {
|
||||
return nil, errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if !rm.hasRole(name) {
|
||||
return []string{}, nil
|
||||
}
|
||||
|
||||
roles := rm.createRole(name).getRoles()
|
||||
if len(domain) == 1 {
|
||||
for i := range roles {
|
||||
roles[i] = roles[i][len(domain[0])+2:]
|
||||
}
|
||||
}
|
||||
return roles, nil
|
||||
}
|
||||
|
||||
// GetUsers gets the users that inherits a subject.
|
||||
// domain is an unreferenced parameter here, may be used in other implementations.
|
||||
func (rm *RoleManager) GetUsers(name string, domain ...string) ([]string, error) {
|
||||
if !rm.hasRole(name) {
|
||||
return nil, errors.New("error: name does not exist")
|
||||
}
|
||||
|
||||
names := []string{}
|
||||
rm.allRoles.Range(func(_, value interface{}) bool {
|
||||
role := value.(*Role)
|
||||
if role.hasDirectRole(name) {
|
||||
names = append(names, role.name)
|
||||
}
|
||||
return true
|
||||
})
|
||||
return names, nil
|
||||
}
|
||||
|
||||
// PrintRoles prints all the roles to log.
|
||||
func (rm *RoleManager) PrintRoles() error {
|
||||
line := ""
|
||||
rm.allRoles.Range(func(_, value interface{}) bool {
|
||||
if text := value.(*Role).toString(); text != "" {
|
||||
if line == "" {
|
||||
line = text
|
||||
} else {
|
||||
line += ", " + text
|
||||
}
|
||||
}
|
||||
return true
|
||||
})
|
||||
log.LogPrint(line)
|
||||
return nil
|
||||
}
|
||||
|
||||
// Role represents the data structure for a role in RBAC.
|
||||
type Role struct {
|
||||
name string
|
||||
roles []*Role
|
||||
}
|
||||
|
||||
func newRole(name string) *Role {
|
||||
r := Role{}
|
||||
r.name = name
|
||||
return &r
|
||||
}
|
||||
|
||||
func (r *Role) addRole(role *Role) {
|
||||
for _, rr := range r.roles {
|
||||
if rr.name == role.name {
|
||||
return
|
||||
}
|
||||
}
|
||||
|
||||
r.roles = append(r.roles, role)
|
||||
}
|
||||
|
||||
func (r *Role) deleteRole(role *Role) {
|
||||
for i, rr := range r.roles {
|
||||
if rr.name == role.name {
|
||||
r.roles = append(r.roles[:i], r.roles[i+1:]...)
|
||||
return
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
func (r *Role) hasRole(name string, hierarchyLevel int) bool {
|
||||
if r.name == name {
|
||||
return true
|
||||
}
|
||||
|
||||
if hierarchyLevel <= 0 {
|
||||
return false
|
||||
}
|
||||
|
||||
for _, role := range r.roles {
|
||||
if role.hasRole(name, hierarchyLevel-1) {
|
||||
return true
|
||||
}
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func (r *Role) hasDirectRole(name string) bool {
|
||||
for _, role := range r.roles {
|
||||
if role.name == name {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
func (r *Role) toString() string {
|
||||
names := ""
|
||||
if len(r.roles) == 0 {
|
||||
return ""
|
||||
}
|
||||
for i, role := range r.roles {
|
||||
if i == 0 {
|
||||
names += role.name
|
||||
} else {
|
||||
names += ", " + role.name
|
||||
}
|
||||
}
|
||||
|
||||
if len(r.roles) == 1 {
|
||||
return r.name + " < " + names
|
||||
} else {
|
||||
return r.name + " < (" + names + ")"
|
||||
}
|
||||
}
|
||||
|
||||
func (r *Role) getRoles() []string {
|
||||
names := []string{}
|
||||
for _, role := range r.roles {
|
||||
names = append(names, role.name)
|
||||
}
|
||||
return names
|
||||
}
|
||||
38
src/vendor/github.com/casbin/casbin/rbac/role_manager.go
generated
vendored
Normal file
38
src/vendor/github.com/casbin/casbin/rbac/role_manager.go
generated
vendored
Normal file
@ -0,0 +1,38 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package rbac
|
||||
|
||||
// RoleManager provides interface to define the operations for managing roles.
|
||||
type RoleManager interface {
|
||||
// Clear clears all stored data and resets the role manager to the initial state.
|
||||
Clear() error
|
||||
// AddLink adds the inheritance link between two roles. role: name1 and role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
AddLink(name1 string, name2 string, domain ...string) error
|
||||
// DeleteLink deletes the inheritance link between two roles. role: name1 and role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
DeleteLink(name1 string, name2 string, domain ...string) error
|
||||
// HasLink determines whether a link exists between two roles. role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
HasLink(name1 string, name2 string, domain ...string) (bool, error)
|
||||
// GetRoles gets the roles that a user inherits.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
GetRoles(name string, domain ...string) ([]string, error)
|
||||
// GetUsers gets the users that inherits a role.
|
||||
// domain is a prefix to the users (can be used for other purposes).
|
||||
GetUsers(name string, domain ...string) ([]string, error)
|
||||
// PrintRoles prints all the roles to log.
|
||||
PrintRoles() error
|
||||
}
|
||||
184
src/vendor/github.com/casbin/casbin/rbac_api.go
generated
vendored
Normal file
184
src/vendor/github.com/casbin/casbin/rbac_api.go
generated
vendored
Normal file
@ -0,0 +1,184 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUser gets the roles that a user has.
|
||||
func (e *Enforcer) GetRolesForUser(name string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetRoles(name)
|
||||
return res
|
||||
}
|
||||
|
||||
// GetUsersForRole gets the users that has a role.
|
||||
func (e *Enforcer) GetUsersForRole(name string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetUsers(name)
|
||||
return res
|
||||
}
|
||||
|
||||
// HasRoleForUser determines whether a user has a role.
|
||||
func (e *Enforcer) HasRoleForUser(name string, role string) bool {
|
||||
roles := e.GetRolesForUser(name)
|
||||
|
||||
hasRole := false
|
||||
for _, r := range roles {
|
||||
if r == role {
|
||||
hasRole = true
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
return hasRole
|
||||
}
|
||||
|
||||
// AddRoleForUser adds a role for a user.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *Enforcer) AddRoleForUser(user string, role string) bool {
|
||||
return e.AddGroupingPolicy(user, role)
|
||||
}
|
||||
|
||||
// DeleteRoleForUser deletes a role for a user.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *Enforcer) DeleteRoleForUser(user string, role string) bool {
|
||||
return e.RemoveGroupingPolicy(user, role)
|
||||
}
|
||||
|
||||
// DeleteRolesForUser deletes all roles for a user.
|
||||
// Returns false if the user does not have any roles (aka not affected).
|
||||
func (e *Enforcer) DeleteRolesForUser(user string) bool {
|
||||
return e.RemoveFilteredGroupingPolicy(0, user)
|
||||
}
|
||||
|
||||
// DeleteUser deletes a user.
|
||||
// Returns false if the user does not exist (aka not affected).
|
||||
func (e *Enforcer) DeleteUser(user string) bool {
|
||||
return e.RemoveFilteredGroupingPolicy(0, user)
|
||||
}
|
||||
|
||||
// DeleteRole deletes a role.
|
||||
func (e *Enforcer) DeleteRole(role string) {
|
||||
e.RemoveFilteredGroupingPolicy(1, role)
|
||||
e.RemoveFilteredPolicy(0, role)
|
||||
}
|
||||
|
||||
// DeletePermission deletes a permission.
|
||||
// Returns false if the permission does not exist (aka not affected).
|
||||
func (e *Enforcer) DeletePermission(permission ...string) bool {
|
||||
return e.RemoveFilteredPolicy(1, permission...)
|
||||
}
|
||||
|
||||
// AddPermissionForUser adds a permission for a user or role.
|
||||
// Returns false if the user or role already has the permission (aka not affected).
|
||||
func (e *Enforcer) AddPermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.AddPolicy(params...)
|
||||
}
|
||||
|
||||
// DeletePermissionForUser deletes a permission for a user or role.
|
||||
// Returns false if the user or role does not have the permission (aka not affected).
|
||||
func (e *Enforcer) DeletePermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.RemovePolicy(params...)
|
||||
}
|
||||
|
||||
// DeletePermissionsForUser deletes permissions for a user or role.
|
||||
// Returns false if the user or role does not have any permissions (aka not affected).
|
||||
func (e *Enforcer) DeletePermissionsForUser(user string) bool {
|
||||
return e.RemoveFilteredPolicy(0, user)
|
||||
}
|
||||
|
||||
// GetPermissionsForUser gets permissions for a user or role.
|
||||
func (e *Enforcer) GetPermissionsForUser(user string) [][]string {
|
||||
return e.GetFilteredPolicy(0, user)
|
||||
}
|
||||
|
||||
// HasPermissionForUser determines whether a user has a permission.
|
||||
func (e *Enforcer) HasPermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.HasPolicy(params...)
|
||||
}
|
||||
|
||||
// GetImplicitRolesForUser gets implicit roles that a user has.
|
||||
// Compared to GetRolesForUser(), this function retrieves indirect roles besides direct roles.
|
||||
// For example:
|
||||
// g, alice, role:admin
|
||||
// g, role:admin, role:user
|
||||
//
|
||||
// GetRolesForUser("alice") can only get: ["role:admin"].
|
||||
// But GetImplicitRolesForUser("alice") will get: ["role:admin", "role:user"].
|
||||
func (e *Enforcer) GetImplicitRolesForUser(name string) []string {
|
||||
res := []string{}
|
||||
roleSet := make(map[string]bool)
|
||||
roleSet[name] = true
|
||||
|
||||
q := make([]string, 0)
|
||||
q = append(q, name)
|
||||
|
||||
for len(q) > 0 {
|
||||
name := q[0]
|
||||
q = q[1:]
|
||||
|
||||
roles, err := e.rm.GetRoles(name)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
for _, r := range roles {
|
||||
if _, ok := roleSet[r]; !ok {
|
||||
res = append(res, r)
|
||||
q = append(q, r)
|
||||
roleSet[r] = true
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
return res
|
||||
}
|
||||
|
||||
// GetImplicitPermissionsForUser gets implicit permissions for a user or role.
|
||||
// Compared to GetPermissionsForUser(), this function retrieves permissions for inherited roles.
|
||||
// For example:
|
||||
// p, admin, data1, read
|
||||
// p, alice, data2, read
|
||||
// g, alice, admin
|
||||
//
|
||||
// GetPermissionsForUser("alice") can only get: [["alice", "data2", "read"]].
|
||||
// But GetImplicitPermissionsForUser("alice") will get: [["admin", "data1", "read"], ["alice", "data2", "read"]].
|
||||
func (e *Enforcer) GetImplicitPermissionsForUser(user string) [][]string {
|
||||
roles := e.GetImplicitRolesForUser(user)
|
||||
roles = append([]string{user}, roles...)
|
||||
|
||||
res := [][]string{}
|
||||
for _, role := range roles {
|
||||
permissions := e.GetPermissionsForUser(role)
|
||||
res = append(res, permissions...)
|
||||
}
|
||||
return res
|
||||
}
|
||||
121
src/vendor/github.com/casbin/casbin/rbac_api_synced.go
generated
vendored
Normal file
121
src/vendor/github.com/casbin/casbin/rbac_api_synced.go
generated
vendored
Normal file
@ -0,0 +1,121 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUser gets the roles that a user has.
|
||||
func (e *SyncedEnforcer) GetRolesForUser(name string) []string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetRolesForUser(name)
|
||||
}
|
||||
|
||||
// GetUsersForRole gets the users that has a role.
|
||||
func (e *SyncedEnforcer) GetUsersForRole(name string) []string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetUsersForRole(name)
|
||||
}
|
||||
|
||||
// HasRoleForUser determines whether a user has a role.
|
||||
func (e *SyncedEnforcer) HasRoleForUser(name string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.HasRoleForUser(name, role)
|
||||
}
|
||||
|
||||
// AddRoleForUser adds a role for a user.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *SyncedEnforcer) AddRoleForUser(user string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddRoleForUser(user, role)
|
||||
}
|
||||
|
||||
// DeleteRoleForUser deletes a role for a user.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteRoleForUser(user string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteRoleForUser(user, role)
|
||||
}
|
||||
|
||||
// DeleteRolesForUser deletes all roles for a user.
|
||||
// Returns false if the user does not have any roles (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteRolesForUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteRolesForUser(user)
|
||||
}
|
||||
|
||||
// DeleteUser deletes a user.
|
||||
// Returns false if the user does not exist (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteUser(user)
|
||||
}
|
||||
|
||||
// DeleteRole deletes a role.
|
||||
func (e *SyncedEnforcer) DeleteRole(role string) {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
e.Enforcer.DeleteRole(role)
|
||||
}
|
||||
|
||||
// DeletePermission deletes a permission.
|
||||
// Returns false if the permission does not exist (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermission(permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermission(permission...)
|
||||
}
|
||||
|
||||
// AddPermissionForUser adds a permission for a user or role.
|
||||
// Returns false if the user or role already has the permission (aka not affected).
|
||||
func (e *SyncedEnforcer) AddPermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddPermissionForUser(user, permission...)
|
||||
}
|
||||
|
||||
// DeletePermissionForUser deletes a permission for a user or role.
|
||||
// Returns false if the user or role does not have the permission (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermissionForUser(user, permission...)
|
||||
}
|
||||
|
||||
// DeletePermissionsForUser deletes permissions for a user or role.
|
||||
// Returns false if the user or role does not have any permissions (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermissionsForUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermissionsForUser(user)
|
||||
}
|
||||
|
||||
// GetPermissionsForUser gets permissions for a user or role.
|
||||
func (e *SyncedEnforcer) GetPermissionsForUser(user string) [][]string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetPermissionsForUser(user)
|
||||
}
|
||||
|
||||
// HasPermissionForUser determines whether a user has a permission.
|
||||
func (e *SyncedEnforcer) HasPermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.HasPermissionForUser(user, permission...)
|
||||
}
|
||||
38
src/vendor/github.com/casbin/casbin/rbac_api_with_domains.go
generated
vendored
Normal file
38
src/vendor/github.com/casbin/casbin/rbac_api_with_domains.go
generated
vendored
Normal file
@ -0,0 +1,38 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUserInDomain gets the roles that a user has inside a domain.
|
||||
func (e *Enforcer) GetRolesForUserInDomain(name string, domain string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetRoles(name, domain)
|
||||
return res
|
||||
}
|
||||
|
||||
// GetPermissionsForUserInDomain gets permissions for a user or role inside a domain.
|
||||
func (e *Enforcer) GetPermissionsForUserInDomain(user string, domain string) [][]string {
|
||||
return e.GetFilteredPolicy(0, user, domain)
|
||||
}
|
||||
|
||||
// AddRoleForUserInDomain adds a role for a user inside a domain.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *Enforcer) AddRoleForUserInDomain(user string, role string, domain string) bool {
|
||||
return e.AddGroupingPolicy(user, role, domain)
|
||||
}
|
||||
|
||||
// DeleteRoleForUserInDomain deletes a role for a user inside a domain.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *Enforcer) DeleteRoleForUserInDomain(user string, role string, domain string) bool {
|
||||
return e.RemoveGroupingPolicy(user, role, domain)
|
||||
}
|
||||
160
src/vendor/github.com/casbin/casbin/util/builtin_operators.go
generated
vendored
Normal file
160
src/vendor/github.com/casbin/casbin/util/builtin_operators.go
generated
vendored
Normal file
@ -0,0 +1,160 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package util
|
||||
|
||||
import (
|
||||
"net"
|
||||
"regexp"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/rbac"
|
||||
)
|
||||
|
||||
// KeyMatch determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*"
|
||||
func KeyMatch(key1 string, key2 string) bool {
|
||||
i := strings.Index(key2, "*")
|
||||
if i == -1 {
|
||||
return key1 == key2
|
||||
}
|
||||
|
||||
if len(key1) > i {
|
||||
return key1[:i] == key2[:i]
|
||||
}
|
||||
return key1 == key2[:i]
|
||||
}
|
||||
|
||||
// KeyMatchFunc is the wrapper for KeyMatch.
|
||||
func KeyMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return bool(KeyMatch(name1, name2)), nil
|
||||
}
|
||||
|
||||
// KeyMatch2 determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*", "/resource1" matches "/:resource"
|
||||
func KeyMatch2(key1 string, key2 string) bool {
|
||||
key2 = strings.Replace(key2, "/*", "/.*", -1)
|
||||
|
||||
re := regexp.MustCompile(`(.*):[^/]+(.*)`)
|
||||
for {
|
||||
if !strings.Contains(key2, "/:") {
|
||||
break
|
||||
}
|
||||
|
||||
key2 = "^" + re.ReplaceAllString(key2, "$1[^/]+$2") + "$"
|
||||
}
|
||||
|
||||
return RegexMatch(key1, key2)
|
||||
}
|
||||
|
||||
// KeyMatch2Func is the wrapper for KeyMatch2.
|
||||
func KeyMatch2Func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return bool(KeyMatch2(name1, name2)), nil
|
||||
}
|
||||
|
||||
// KeyMatch3 determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*", "/resource1" matches "/{resource}"
|
||||
func KeyMatch3(key1 string, key2 string) bool {
|
||||
key2 = strings.Replace(key2, "/*", "/.*", -1)
|
||||
|
||||
re := regexp.MustCompile(`(.*)\{[^/]+\}(.*)`)
|
||||
for {
|
||||
if !strings.Contains(key2, "/{") {
|
||||
break
|
||||
}
|
||||
|
||||
key2 = re.ReplaceAllString(key2, "$1[^/]+$2")
|
||||
}
|
||||
|
||||
return RegexMatch(key1, key2)
|
||||
}
|
||||
|
||||
// KeyMatch3Func is the wrapper for KeyMatch3.
|
||||
func KeyMatch3Func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return bool(KeyMatch3(name1, name2)), nil
|
||||
}
|
||||
|
||||
// RegexMatch determines whether key1 matches the pattern of key2 in regular expression.
|
||||
func RegexMatch(key1 string, key2 string) bool {
|
||||
res, err := regexp.MatchString(key2, key1)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
return res
|
||||
}
|
||||
|
||||
// RegexMatchFunc is the wrapper for RegexMatch.
|
||||
func RegexMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return bool(RegexMatch(name1, name2)), nil
|
||||
}
|
||||
|
||||
// IPMatch determines whether IP address ip1 matches the pattern of IP address ip2, ip2 can be an IP address or a CIDR pattern.
|
||||
// For example, "192.168.2.123" matches "192.168.2.0/24"
|
||||
func IPMatch(ip1 string, ip2 string) bool {
|
||||
objIP1 := net.ParseIP(ip1)
|
||||
if objIP1 == nil {
|
||||
panic("invalid argument: ip1 in IPMatch() function is not an IP address.")
|
||||
}
|
||||
|
||||
_, cidr, err := net.ParseCIDR(ip2)
|
||||
if err != nil {
|
||||
objIP2 := net.ParseIP(ip2)
|
||||
if objIP2 == nil {
|
||||
panic("invalid argument: ip2 in IPMatch() function is neither an IP address nor a CIDR.")
|
||||
}
|
||||
|
||||
return objIP1.Equal(objIP2)
|
||||
}
|
||||
|
||||
return cidr.Contains(objIP1)
|
||||
}
|
||||
|
||||
// IPMatchFunc is the wrapper for IPMatch.
|
||||
func IPMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
ip1 := args[0].(string)
|
||||
ip2 := args[1].(string)
|
||||
|
||||
return bool(IPMatch(ip1, ip2)), nil
|
||||
}
|
||||
|
||||
// GenerateGFunction is the factory method of the g(_, _) function.
|
||||
func GenerateGFunction(rm rbac.RoleManager) func(args ...interface{}) (interface{}, error) {
|
||||
return func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
if rm == nil {
|
||||
return name1 == name2, nil
|
||||
} else if len(args) == 2 {
|
||||
res, _ := rm.HasLink(name1, name2)
|
||||
return res, nil
|
||||
} else {
|
||||
domain := args[2].(string)
|
||||
res, _ := rm.HasLink(name1, name2, domain)
|
||||
return res, nil
|
||||
}
|
||||
}
|
||||
}
|
||||
105
src/vendor/github.com/casbin/casbin/util/util.go
generated
vendored
Normal file
105
src/vendor/github.com/casbin/casbin/util/util.go
generated
vendored
Normal file
@ -0,0 +1,105 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package util
|
||||
|
||||
import (
|
||||
"sort"
|
||||
"strings"
|
||||
)
|
||||
|
||||
// EscapeAssertion escapes the dots in the assertion, because the expression evaluation doesn't support such variable names.
|
||||
func EscapeAssertion(s string) string {
|
||||
s = strings.Replace(s, "r.", "r_", -1)
|
||||
s = strings.Replace(s, "p.", "p_", -1)
|
||||
return s
|
||||
}
|
||||
|
||||
// RemoveComments removes the comments starting with # in the text.
|
||||
func RemoveComments(s string) string {
|
||||
pos := strings.Index(s, "#")
|
||||
if pos == -1 {
|
||||
return s
|
||||
}
|
||||
return strings.TrimSpace(s[0:pos])
|
||||
}
|
||||
|
||||
// ArrayEquals determines whether two string arrays are identical.
|
||||
func ArrayEquals(a []string, b []string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
for i, v := range a {
|
||||
if v != b[i] {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
|
||||
// Array2DEquals determines whether two 2-dimensional string arrays are identical.
|
||||
func Array2DEquals(a [][]string, b [][]string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
for i, v := range a {
|
||||
if !ArrayEquals(v, b[i]) {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
|
||||
// ArrayRemoveDuplicates removes any duplicated elements in a string array.
|
||||
func ArrayRemoveDuplicates(s *[]string) {
|
||||
found := make(map[string]bool)
|
||||
j := 0
|
||||
for i, x := range *s {
|
||||
if !found[x] {
|
||||
found[x] = true
|
||||
(*s)[j] = (*s)[i]
|
||||
j++
|
||||
}
|
||||
}
|
||||
*s = (*s)[:j]
|
||||
}
|
||||
|
||||
// ArrayToString gets a printable string for a string array.
|
||||
func ArrayToString(s []string) string {
|
||||
return strings.Join(s, ", ")
|
||||
}
|
||||
|
||||
// ParamsToString gets a printable string for variable number of parameters.
|
||||
func ParamsToString(s ...string) string {
|
||||
return strings.Join(s, ", ")
|
||||
}
|
||||
|
||||
// SetEquals determines whether two string sets are identical.
|
||||
func SetEquals(a []string, b []string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
sort.Strings(a)
|
||||
sort.Strings(b)
|
||||
|
||||
for i, v := range a {
|
||||
if v != b[i] {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
24
src/vendor/github.com/pkg/errors/.gitignore
generated
vendored
Normal file
24
src/vendor/github.com/pkg/errors/.gitignore
generated
vendored
Normal file
@ -0,0 +1,24 @@
|
||||
# Compiled Object files, Static and Dynamic libs (Shared Objects)
|
||||
*.o
|
||||
*.a
|
||||
*.so
|
||||
|
||||
# Folders
|
||||
_obj
|
||||
_test
|
||||
|
||||
# Architecture specific extensions/prefixes
|
||||
*.[568vq]
|
||||
[568vq].out
|
||||
|
||||
*.cgo1.go
|
||||
*.cgo2.c
|
||||
_cgo_defun.c
|
||||
_cgo_gotypes.go
|
||||
_cgo_export.*
|
||||
|
||||
_testmain.go
|
||||
|
||||
*.exe
|
||||
*.test
|
||||
*.prof
|
||||
11
src/vendor/github.com/pkg/errors/.travis.yml
generated
vendored
Normal file
11
src/vendor/github.com/pkg/errors/.travis.yml
generated
vendored
Normal file
@ -0,0 +1,11 @@
|
||||
language: go
|
||||
go_import_path: github.com/pkg/errors
|
||||
go:
|
||||
- 1.4.3
|
||||
- 1.5.4
|
||||
- 1.6.2
|
||||
- 1.7.1
|
||||
- tip
|
||||
|
||||
script:
|
||||
- go test -v ./...
|
||||
23
src/vendor/github.com/pkg/errors/LICENSE
generated
vendored
Normal file
23
src/vendor/github.com/pkg/errors/LICENSE
generated
vendored
Normal file
@ -0,0 +1,23 @@
|
||||
Copyright (c) 2015, Dave Cheney <dave@cheney.net>
|
||||
All rights reserved.
|
||||
|
||||
Redistribution and use in source and binary forms, with or without
|
||||
modification, are permitted provided that the following conditions are met:
|
||||
|
||||
* Redistributions of source code must retain the above copyright notice, this
|
||||
list of conditions and the following disclaimer.
|
||||
|
||||
* Redistributions in binary form must reproduce the above copyright notice,
|
||||
this list of conditions and the following disclaimer in the documentation
|
||||
and/or other materials provided with the distribution.
|
||||
|
||||
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
|
||||
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
|
||||
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
|
||||
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
|
||||
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
|
||||
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
|
||||
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
|
||||
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
|
||||
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
|
||||
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
|
||||
52
src/vendor/github.com/pkg/errors/README.md
generated
vendored
Normal file
52
src/vendor/github.com/pkg/errors/README.md
generated
vendored
Normal file
@ -0,0 +1,52 @@
|
||||
# errors [](https://travis-ci.org/pkg/errors) [](https://ci.appveyor.com/project/davecheney/errors/branch/master) [](http://godoc.org/github.com/pkg/errors) [](https://goreportcard.com/report/github.com/pkg/errors)
|
||||
|
||||
Package errors provides simple error handling primitives.
|
||||
|
||||
`go get github.com/pkg/errors`
|
||||
|
||||
The traditional error handling idiom in Go is roughly akin to
|
||||
```go
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
```
|
||||
which applied recursively up the call stack results in error reports without context or debugging information. The errors package allows programmers to add context to the failure path in their code in a way that does not destroy the original value of the error.
|
||||
|
||||
## Adding context to an error
|
||||
|
||||
The errors.Wrap function returns a new error that adds context to the original error. For example
|
||||
```go
|
||||
_, err := ioutil.ReadAll(r)
|
||||
if err != nil {
|
||||
return errors.Wrap(err, "read failed")
|
||||
}
|
||||
```
|
||||
## Retrieving the cause of an error
|
||||
|
||||
Using `errors.Wrap` constructs a stack of errors, adding context to the preceding error. Depending on the nature of the error it may be necessary to reverse the operation of errors.Wrap to retrieve the original error for inspection. Any error value which implements this interface can be inspected by `errors.Cause`.
|
||||
```go
|
||||
type causer interface {
|
||||
Cause() error
|
||||
}
|
||||
```
|
||||
`errors.Cause` will recursively retrieve the topmost error which does not implement `causer`, which is assumed to be the original cause. For example:
|
||||
```go
|
||||
switch err := errors.Cause(err).(type) {
|
||||
case *MyError:
|
||||
// handle specifically
|
||||
default:
|
||||
// unknown error
|
||||
}
|
||||
```
|
||||
|
||||
[Read the package documentation for more information](https://godoc.org/github.com/pkg/errors).
|
||||
|
||||
## Contributing
|
||||
|
||||
We welcome pull requests, bug fixes and issue reports. With that said, the bar for adding new symbols to this package is intentionally set high.
|
||||
|
||||
Before proposing a change, please discuss your change by raising an issue.
|
||||
|
||||
## Licence
|
||||
|
||||
BSD-2-Clause
|
||||
32
src/vendor/github.com/pkg/errors/appveyor.yml
generated
vendored
Normal file
32
src/vendor/github.com/pkg/errors/appveyor.yml
generated
vendored
Normal file
@ -0,0 +1,32 @@
|
||||
version: build-{build}.{branch}
|
||||
|
||||
clone_folder: C:\gopath\src\github.com\pkg\errors
|
||||
shallow_clone: true # for startup speed
|
||||
|
||||
environment:
|
||||
GOPATH: C:\gopath
|
||||
|
||||
platform:
|
||||
- x64
|
||||
|
||||
# http://www.appveyor.com/docs/installed-software
|
||||
install:
|
||||
# some helpful output for debugging builds
|
||||
- go version
|
||||
- go env
|
||||
# pre-installed MinGW at C:\MinGW is 32bit only
|
||||
# but MSYS2 at C:\msys64 has mingw64
|
||||
- set PATH=C:\msys64\mingw64\bin;%PATH%
|
||||
- gcc --version
|
||||
- g++ --version
|
||||
|
||||
build_script:
|
||||
- go install -v ./...
|
||||
|
||||
test_script:
|
||||
- set PATH=C:\gopath\bin;%PATH%
|
||||
- go test -v ./...
|
||||
|
||||
#artifacts:
|
||||
# - path: '%GOPATH%\bin\*.exe'
|
||||
deploy: off
|
||||
269
src/vendor/github.com/pkg/errors/errors.go
generated
vendored
Normal file
269
src/vendor/github.com/pkg/errors/errors.go
generated
vendored
Normal file
@ -0,0 +1,269 @@
|
||||
// Package errors provides simple error handling primitives.
|
||||
//
|
||||
// The traditional error handling idiom in Go is roughly akin to
|
||||
//
|
||||
// if err != nil {
|
||||
// return err
|
||||
// }
|
||||
//
|
||||
// which applied recursively up the call stack results in error reports
|
||||
// without context or debugging information. The errors package allows
|
||||
// programmers to add context to the failure path in their code in a way
|
||||
// that does not destroy the original value of the error.
|
||||
//
|
||||
// Adding context to an error
|
||||
//
|
||||
// The errors.Wrap function returns a new error that adds context to the
|
||||
// original error by recording a stack trace at the point Wrap is called,
|
||||
// and the supplied message. For example
|
||||
//
|
||||
// _, err := ioutil.ReadAll(r)
|
||||
// if err != nil {
|
||||
// return errors.Wrap(err, "read failed")
|
||||
// }
|
||||
//
|
||||
// If additional control is required the errors.WithStack and errors.WithMessage
|
||||
// functions destructure errors.Wrap into its component operations of annotating
|
||||
// an error with a stack trace and an a message, respectively.
|
||||
//
|
||||
// Retrieving the cause of an error
|
||||
//
|
||||
// Using errors.Wrap constructs a stack of errors, adding context to the
|
||||
// preceding error. Depending on the nature of the error it may be necessary
|
||||
// to reverse the operation of errors.Wrap to retrieve the original error
|
||||
// for inspection. Any error value which implements this interface
|
||||
//
|
||||
// type causer interface {
|
||||
// Cause() error
|
||||
// }
|
||||
//
|
||||
// can be inspected by errors.Cause. errors.Cause will recursively retrieve
|
||||
// the topmost error which does not implement causer, which is assumed to be
|
||||
// the original cause. For example:
|
||||
//
|
||||
// switch err := errors.Cause(err).(type) {
|
||||
// case *MyError:
|
||||
// // handle specifically
|
||||
// default:
|
||||
// // unknown error
|
||||
// }
|
||||
//
|
||||
// causer interface is not exported by this package, but is considered a part
|
||||
// of stable public API.
|
||||
//
|
||||
// Formatted printing of errors
|
||||
//
|
||||
// All error values returned from this package implement fmt.Formatter and can
|
||||
// be formatted by the fmt package. The following verbs are supported
|
||||
//
|
||||
// %s print the error. If the error has a Cause it will be
|
||||
// printed recursively
|
||||
// %v see %s
|
||||
// %+v extended format. Each Frame of the error's StackTrace will
|
||||
// be printed in detail.
|
||||
//
|
||||
// Retrieving the stack trace of an error or wrapper
|
||||
//
|
||||
// New, Errorf, Wrap, and Wrapf record a stack trace at the point they are
|
||||
// invoked. This information can be retrieved with the following interface.
|
||||
//
|
||||
// type stackTracer interface {
|
||||
// StackTrace() errors.StackTrace
|
||||
// }
|
||||
//
|
||||
// Where errors.StackTrace is defined as
|
||||
//
|
||||
// type StackTrace []Frame
|
||||
//
|
||||
// The Frame type represents a call site in the stack trace. Frame supports
|
||||
// the fmt.Formatter interface that can be used for printing information about
|
||||
// the stack trace of this error. For example:
|
||||
//
|
||||
// if err, ok := err.(stackTracer); ok {
|
||||
// for _, f := range err.StackTrace() {
|
||||
// fmt.Printf("%+s:%d", f)
|
||||
// }
|
||||
// }
|
||||
//
|
||||
// stackTracer interface is not exported by this package, but is considered a part
|
||||
// of stable public API.
|
||||
//
|
||||
// See the documentation for Frame.Format for more details.
|
||||
package errors
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
"io"
|
||||
)
|
||||
|
||||
// New returns an error with the supplied message.
|
||||
// New also records the stack trace at the point it was called.
|
||||
func New(message string) error {
|
||||
return &fundamental{
|
||||
msg: message,
|
||||
stack: callers(),
|
||||
}
|
||||
}
|
||||
|
||||
// Errorf formats according to a format specifier and returns the string
|
||||
// as a value that satisfies error.
|
||||
// Errorf also records the stack trace at the point it was called.
|
||||
func Errorf(format string, args ...interface{}) error {
|
||||
return &fundamental{
|
||||
msg: fmt.Sprintf(format, args...),
|
||||
stack: callers(),
|
||||
}
|
||||
}
|
||||
|
||||
// fundamental is an error that has a message and a stack, but no caller.
|
||||
type fundamental struct {
|
||||
msg string
|
||||
*stack
|
||||
}
|
||||
|
||||
func (f *fundamental) Error() string { return f.msg }
|
||||
|
||||
func (f *fundamental) Format(s fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 'v':
|
||||
if s.Flag('+') {
|
||||
io.WriteString(s, f.msg)
|
||||
f.stack.Format(s, verb)
|
||||
return
|
||||
}
|
||||
fallthrough
|
||||
case 's':
|
||||
io.WriteString(s, f.msg)
|
||||
case 'q':
|
||||
fmt.Fprintf(s, "%q", f.msg)
|
||||
}
|
||||
}
|
||||
|
||||
// WithStack annotates err with a stack trace at the point WithStack was called.
|
||||
// If err is nil, WithStack returns nil.
|
||||
func WithStack(err error) error {
|
||||
if err == nil {
|
||||
return nil
|
||||
}
|
||||
return &withStack{
|
||||
err,
|
||||
callers(),
|
||||
}
|
||||
}
|
||||
|
||||
type withStack struct {
|
||||
error
|
||||
*stack
|
||||
}
|
||||
|
||||
func (w *withStack) Cause() error { return w.error }
|
||||
|
||||
func (w *withStack) Format(s fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 'v':
|
||||
if s.Flag('+') {
|
||||
fmt.Fprintf(s, "%+v", w.Cause())
|
||||
w.stack.Format(s, verb)
|
||||
return
|
||||
}
|
||||
fallthrough
|
||||
case 's':
|
||||
io.WriteString(s, w.Error())
|
||||
case 'q':
|
||||
fmt.Fprintf(s, "%q", w.Error())
|
||||
}
|
||||
}
|
||||
|
||||
// Wrap returns an error annotating err with a stack trace
|
||||
// at the point Wrap is called, and the supplied message.
|
||||
// If err is nil, Wrap returns nil.
|
||||
func Wrap(err error, message string) error {
|
||||
if err == nil {
|
||||
return nil
|
||||
}
|
||||
err = &withMessage{
|
||||
cause: err,
|
||||
msg: message,
|
||||
}
|
||||
return &withStack{
|
||||
err,
|
||||
callers(),
|
||||
}
|
||||
}
|
||||
|
||||
// Wrapf returns an error annotating err with a stack trace
|
||||
// at the point Wrapf is call, and the format specifier.
|
||||
// If err is nil, Wrapf returns nil.
|
||||
func Wrapf(err error, format string, args ...interface{}) error {
|
||||
if err == nil {
|
||||
return nil
|
||||
}
|
||||
err = &withMessage{
|
||||
cause: err,
|
||||
msg: fmt.Sprintf(format, args...),
|
||||
}
|
||||
return &withStack{
|
||||
err,
|
||||
callers(),
|
||||
}
|
||||
}
|
||||
|
||||
// WithMessage annotates err with a new message.
|
||||
// If err is nil, WithMessage returns nil.
|
||||
func WithMessage(err error, message string) error {
|
||||
if err == nil {
|
||||
return nil
|
||||
}
|
||||
return &withMessage{
|
||||
cause: err,
|
||||
msg: message,
|
||||
}
|
||||
}
|
||||
|
||||
type withMessage struct {
|
||||
cause error
|
||||
msg string
|
||||
}
|
||||
|
||||
func (w *withMessage) Error() string { return w.msg + ": " + w.cause.Error() }
|
||||
func (w *withMessage) Cause() error { return w.cause }
|
||||
|
||||
func (w *withMessage) Format(s fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 'v':
|
||||
if s.Flag('+') {
|
||||
fmt.Fprintf(s, "%+v\n", w.Cause())
|
||||
io.WriteString(s, w.msg)
|
||||
return
|
||||
}
|
||||
fallthrough
|
||||
case 's', 'q':
|
||||
io.WriteString(s, w.Error())
|
||||
}
|
||||
}
|
||||
|
||||
// Cause returns the underlying cause of the error, if possible.
|
||||
// An error value has a cause if it implements the following
|
||||
// interface:
|
||||
//
|
||||
// type causer interface {
|
||||
// Cause() error
|
||||
// }
|
||||
//
|
||||
// If the error does not implement Cause, the original error will
|
||||
// be returned. If the error is nil, nil will be returned without further
|
||||
// investigation.
|
||||
func Cause(err error) error {
|
||||
type causer interface {
|
||||
Cause() error
|
||||
}
|
||||
|
||||
for err != nil {
|
||||
cause, ok := err.(causer)
|
||||
if !ok {
|
||||
break
|
||||
}
|
||||
err = cause.Cause()
|
||||
}
|
||||
return err
|
||||
}
|
||||
178
src/vendor/github.com/pkg/errors/stack.go
generated
vendored
Normal file
178
src/vendor/github.com/pkg/errors/stack.go
generated
vendored
Normal file
@ -0,0 +1,178 @@
|
||||
package errors
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
"io"
|
||||
"path"
|
||||
"runtime"
|
||||
"strings"
|
||||
)
|
||||
|
||||
// Frame represents a program counter inside a stack frame.
|
||||
type Frame uintptr
|
||||
|
||||
// pc returns the program counter for this frame;
|
||||
// multiple frames may have the same PC value.
|
||||
func (f Frame) pc() uintptr { return uintptr(f) - 1 }
|
||||
|
||||
// file returns the full path to the file that contains the
|
||||
// function for this Frame's pc.
|
||||
func (f Frame) file() string {
|
||||
fn := runtime.FuncForPC(f.pc())
|
||||
if fn == nil {
|
||||
return "unknown"
|
||||
}
|
||||
file, _ := fn.FileLine(f.pc())
|
||||
return file
|
||||
}
|
||||
|
||||
// line returns the line number of source code of the
|
||||
// function for this Frame's pc.
|
||||
func (f Frame) line() int {
|
||||
fn := runtime.FuncForPC(f.pc())
|
||||
if fn == nil {
|
||||
return 0
|
||||
}
|
||||
_, line := fn.FileLine(f.pc())
|
||||
return line
|
||||
}
|
||||
|
||||
// Format formats the frame according to the fmt.Formatter interface.
|
||||
//
|
||||
// %s source file
|
||||
// %d source line
|
||||
// %n function name
|
||||
// %v equivalent to %s:%d
|
||||
//
|
||||
// Format accepts flags that alter the printing of some verbs, as follows:
|
||||
//
|
||||
// %+s path of source file relative to the compile time GOPATH
|
||||
// %+v equivalent to %+s:%d
|
||||
func (f Frame) Format(s fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 's':
|
||||
switch {
|
||||
case s.Flag('+'):
|
||||
pc := f.pc()
|
||||
fn := runtime.FuncForPC(pc)
|
||||
if fn == nil {
|
||||
io.WriteString(s, "unknown")
|
||||
} else {
|
||||
file, _ := fn.FileLine(pc)
|
||||
fmt.Fprintf(s, "%s\n\t%s", fn.Name(), file)
|
||||
}
|
||||
default:
|
||||
io.WriteString(s, path.Base(f.file()))
|
||||
}
|
||||
case 'd':
|
||||
fmt.Fprintf(s, "%d", f.line())
|
||||
case 'n':
|
||||
name := runtime.FuncForPC(f.pc()).Name()
|
||||
io.WriteString(s, funcname(name))
|
||||
case 'v':
|
||||
f.Format(s, 's')
|
||||
io.WriteString(s, ":")
|
||||
f.Format(s, 'd')
|
||||
}
|
||||
}
|
||||
|
||||
// StackTrace is stack of Frames from innermost (newest) to outermost (oldest).
|
||||
type StackTrace []Frame
|
||||
|
||||
func (st StackTrace) Format(s fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 'v':
|
||||
switch {
|
||||
case s.Flag('+'):
|
||||
for _, f := range st {
|
||||
fmt.Fprintf(s, "\n%+v", f)
|
||||
}
|
||||
case s.Flag('#'):
|
||||
fmt.Fprintf(s, "%#v", []Frame(st))
|
||||
default:
|
||||
fmt.Fprintf(s, "%v", []Frame(st))
|
||||
}
|
||||
case 's':
|
||||
fmt.Fprintf(s, "%s", []Frame(st))
|
||||
}
|
||||
}
|
||||
|
||||
// stack represents a stack of program counters.
|
||||
type stack []uintptr
|
||||
|
||||
func (s *stack) Format(st fmt.State, verb rune) {
|
||||
switch verb {
|
||||
case 'v':
|
||||
switch {
|
||||
case st.Flag('+'):
|
||||
for _, pc := range *s {
|
||||
f := Frame(pc)
|
||||
fmt.Fprintf(st, "\n%+v", f)
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
func (s *stack) StackTrace() StackTrace {
|
||||
f := make([]Frame, len(*s))
|
||||
for i := 0; i < len(f); i++ {
|
||||
f[i] = Frame((*s)[i])
|
||||
}
|
||||
return f
|
||||
}
|
||||
|
||||
func callers() *stack {
|
||||
const depth = 32
|
||||
var pcs [depth]uintptr
|
||||
n := runtime.Callers(3, pcs[:])
|
||||
var st stack = pcs[0:n]
|
||||
return &st
|
||||
}
|
||||
|
||||
// funcname removes the path prefix component of a function's name reported by func.Name().
|
||||
func funcname(name string) string {
|
||||
i := strings.LastIndex(name, "/")
|
||||
name = name[i+1:]
|
||||
i = strings.Index(name, ".")
|
||||
return name[i+1:]
|
||||
}
|
||||
|
||||
func trimGOPATH(name, file string) string {
|
||||
// Here we want to get the source file path relative to the compile time
|
||||
// GOPATH. As of Go 1.6.x there is no direct way to know the compiled
|
||||
// GOPATH at runtime, but we can infer the number of path segments in the
|
||||
// GOPATH. We note that fn.Name() returns the function name qualified by
|
||||
// the import path, which does not include the GOPATH. Thus we can trim
|
||||
// segments from the beginning of the file path until the number of path
|
||||
// separators remaining is one more than the number of path separators in
|
||||
// the function name. For example, given:
|
||||
//
|
||||
// GOPATH /home/user
|
||||
// file /home/user/src/pkg/sub/file.go
|
||||
// fn.Name() pkg/sub.Type.Method
|
||||
//
|
||||
// We want to produce:
|
||||
//
|
||||
// pkg/sub/file.go
|
||||
//
|
||||
// From this we can easily see that fn.Name() has one less path separator
|
||||
// than our desired output. We count separators from the end of the file
|
||||
// path until it finds two more than in the function name and then move
|
||||
// one character forward to preserve the initial path segment without a
|
||||
// leading separator.
|
||||
const sep = "/"
|
||||
goal := strings.Count(name, sep) + 2
|
||||
i := len(file)
|
||||
for n := 0; n < goal; n++ {
|
||||
i = strings.LastIndex(file[:i], sep)
|
||||
if i == -1 {
|
||||
// not enough separators found, set i so that the slice expression
|
||||
// below leaves file unmodified
|
||||
i = -len(sep)
|
||||
break
|
||||
}
|
||||
}
|
||||
// get back to 0 or trim the leading separator
|
||||
file = file[i+len(sep):]
|
||||
return file
|
||||
}
|
||||
Loading…
Reference in New Issue
Block a user